File Info
| Exam | Fortinet NSE 7 - OT Security 7.2 |
| Number | NSE7_OTS-7.2 |
| File Name | Fortinet.NSE7_OTS-7.2.VCEplus.2024-04-29.30q.vcex |
| Size | 2 MB |
| Posted | Apr 29, 2024 |
| Download | Fortinet.NSE7_OTS-7.2.VCEplus.2024-04-29.30q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
An OT administrator has configured FSSO and local firewall authentication. A user who is part of a user group is not prompted from credentials during authentication.
What is a possible reason?
- FortiGate determined the user by passive authentication
- The user was determined by Security Fabric
- Two-factor authentication is not configured with RADIUS authentication method
- FortiNAC determined the user by DHCP fingerprint method
Correct answer: A
Question 2
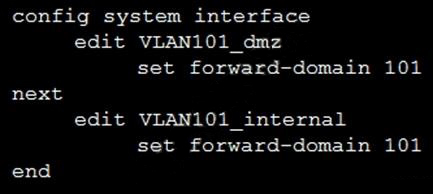
Refer to the exhibit.

Given the configurations on the FortiGate, which statement is true?
- FortiGate is configured with forward-domains to reduce unnecessary traffic.
- FortiGate is configured with forward-domains to forward only domain controller traffic.
- FortiGate is configured with forward-domains to forward only company domain website traffic.
- FortiGate is configured with forward-domains to filter and drop non-domain controller traffic.
Correct answer: A
Question 3
To increase security protection in an OT network, how does application control on ForliGate detect industrial traffic?
- By inspecting software and software-based vulnerabilities
- By inspecting applications only on nonprotected traffic
- By inspecting applications with more granularity by inspecting subapplication traffic
- By inspecting protocols used in the application traffic
Correct answer: B
Question 4
What are two critical tasks the OT network auditors must perform during OT network risk assessment and management? (Choose two.)
- Planning a threat hunting strategy
- Implementing strategies to automatically bring PLCs offline
- Creating disaster recovery plans to switch operations to a backup plant
- Evaluating what can go wrong before it happens
Correct answer: AC
Question 5

Refer to the exhibit.

PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT cannot send traffic to each other.
Which two statements about the traffic between PCL-1 and PLC-2 are true? (Choose two.)
- The switch on FGT-2 must be hardware to implement micro-segmentation.
- Micro-segmentation on FGT-2 prevents direct device-to-device communication.
- Traffic must be inspected by FGT-EDGE in OT networks.
- FGT-2 controls intra-VLAN traffic through firewall policies.
Correct answer: BD
Question 6
Which three Fortinet products can you use for device identification in an OT industrial control system (ICS)? (Choose three.)
- FortiSIEM
- FortiManager
- FortiAnalyzer
- FortiGate
- FortiNAC
Correct answer: ADE
Question 7

Refer to the exhibit.

In order for a FortiGate device to act as router on a stick, what configuration must an OT network architect implement on FortiGate to achieve inter-VLAN routing?
- Set a unique forward domain on each interface on the network.
- Set FortiGate to operate in transparent mode.
- Set a software switch on FortiGate to handle inter-VLAN traffic.
- Set a FortiGate interface with the switch to operate as an 802.1 q trunk.
Correct answer: D
Question 8
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
- You must set correct operator in event handler to trigger an event.
- You can automate SOC tasks through playbooks.
- Each playbook can include multiple triggers.
- You cannot use Windows and Linux hosts security events with FortiSoC.
Correct answer: AB
Explanation:
Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc
Question 9
You are investigating a series of incidents that occurred in the OT network over past 24 hours in FortiSIEM.
Which three FortiSIEM options can you use to investigate these incidents? (Choose three.)
- Security
- IPS
- List
- Risk
- Overview
Correct answer: CDE
Question 10
When you create a user or host profile, which three criteria can you use? (Choose three.)
- Host or user group memberships
- Administrative group membership
- An existing access control policy
- Location
- Host or user attributes
Correct answer: ADE
Explanation:
https://docs.fortinet.com/document/fortinac/9.2.0/administration-guide/15797/user-host-profiles https://docs.fortinet.com/document/fortinac/9.2.0/administration-guide/15797/user-host-profiles

