File Info
| Exam | BTA Certified Blockchain Solution Architect |
| Number | CBSA |
| File Name | Blockchain.CBSA.PrepAway.2019-04-01.67q.vcex |
| Size | 253 KB |
| Posted | Apr 01, 2019 |
| Download | Blockchain.CBSA.PrepAway.2019-04-01.67q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
What are two challenges with using a Proof of Work algorithm? (Select two.)
- Mining pools not allowed
- Difficulty rate goes done every year.
- Expensive
- Power Intensive
Correct answer: CD
Explanation:
Reference: http://www.hl.co.uk/news/2018/2/16/a-brief-history-of-blockchain-technology-everyone-should-read Reference: http://www.hl.co.uk/news/2018/2/16/a-brief-history-of-blockchain-technology-everyone-should-read
Question 2
Your customer is an enterprise that is focused on financial sectors. What type of blockchain would this customer likely want specified for their enterprise?
- Permissionless
- Decentralized
- Hybrid
- Permissioned
Correct answer: D
Explanation:
Sometimes referred to as “private” blockchains, you are required to have some sort of permission to access any or parts of that blockchain. There are a multitude of variants and hybrid permissioned/permissionless blockchains that exist. Reference: https://medium.com/@dustindreifuerst/permissioned-vs-permissionless-blockchains-acb8661ee095 Sometimes referred to as “private” blockchains, you are required to have some sort of permission to access any or parts of that blockchain. There are a multitude of variants and hybrid permissioned/permissionless blockchains that exist.
Reference: https://medium.com/@dustindreifuerst/permissioned-vs-permissionless-blockchains-acb8661ee095
Question 3
Ethereum is considered to be a ______________type of blockchain.
- Permissionless
- Permission Based
- Hybrid
- Private
Correct answer: A
Explanation:
Permissionless - anyone can join Anyone can run a node, run mining software/hardware, access a wallet and write data onto and transact within the blockchain (as long as they follow the rules of the bitcoin blockchain). There is no way to censor anyone, ever, on the permissionless bitcoin blockchain. Reference: https://medium.com/@dustindreifuerst/permissioned-vs-permissionless-blockchains-acb8661ee095 Permissionless - anyone can join Anyone can run a node, run mining software/hardware, access a wallet and write data onto and transact within the blockchain (as long as they follow the rules of the bitcoin blockchain). There is no way to censor anyone, ever, on the permissionless bitcoin blockchain.
Reference: https://medium.com/@dustindreifuerst/permissioned-vs-permissionless-blockchains-acb8661ee095
Question 4
Your company working for is now considering the blockchain. They would like to perform a POC with R3 Corda. The CIO was reading about different blockchain consensus algos and would like to understand what type of consensus algos is used with Corda.
What is the best answer?
- R3 Corda is a pluggable blockchain and allows the enterprise flexibility
- R3 Corda is a byzantine fault tolerant blokchain
- R3 Corda is a proof of stake based blockchain
- R3 Corda is a proof of work based blockchain
Correct answer: A
Explanation:
Corda does not share the same requirements as Bitcoin: we require absolute certainty over transaction finality and we need to know who our counterparts are. So we had the freedom – and took this opportunity – to solve the consensus problem in a different way. In particular, Corda solves the privacy issue in a number of manners, primarily by allowing for separation of consensus into a service which we call the Notary Cluster. Corda was designed for business from the start. It has no cryptocurrency built into the platform and does not require mining-style consensus, which imposes great cost with little business benefit. Corda does not share the same requirements as Bitcoin: we require absolute certainty over transaction finality and we need to know who our counterparts are. So we had the freedom – and took this opportunity – to solve the consensus problem in a different way. In particular, Corda solves the privacy issue in a number of manners, primarily by allowing for separation of consensus into a service which we call the Notary Cluster. Corda was designed for business from the start. It has no cryptocurrency built into the platform and does not require mining-style consensus, which imposes great cost with little business benefit.
Question 5
Secure Hash Algorithm (SHA-256) output is always 256 bits or 32 bytes in length regardless of the length of the input (even if input is millions of bytes). Select best answer.
- NSA is spying on us so what’s it matters.
- Depends on input
- False
- True
Correct answer: D
Explanation:
SHA stands for Secure Hash Algorithm. This is used to prove data integrity. The same input(s) will always produce the exact same output. This output is always 256 bits or 32 bytes in length regardless of the length of the input (even if input is millions of bytes). Reference: https://medium.com/all-things-ledger/bitcoins-implementation-of-blockchain-2be713f662c2 SHA stands for Secure Hash Algorithm. This is used to prove data integrity. The same input(s) will always produce the exact same output. This output is always 256 bits or 32 bytes in length regardless of the length of the input (even if input is millions of bytes).
Reference: https://medium.com/all-things-ledger/bitcoins-implementation-of-blockchain-2be713f662c2
Question 6
In the Ethereum EVM there are two types of memory areas. (Select two.)
- Storage
- Database
- Memory
- Persistent
- Ephemeral
Correct answer: AC
Explanation:
Reference: https://solidity.readthedocs.io/en/latest/introduction-to-smart-contracts.html#the-ethereum-virtual-machine Reference: https://solidity.readthedocs.io/en/latest/introduction-to-smart-contracts.html#the-ethereum-virtual-machine
Question 7
What are some advantages of Proof of Stake(POS) mining over Proof of Work(POW) mining? (Select three.)
- Energy efficient in regards to that it could consume for electricity as compared to PoW
- Faster Hashing algorithms
- No need for expensive compared to POW
- Faster validations compared to POW
- Better blockchain security compared to POW
Correct answer: ACD
Explanation:
This eliminates the below challenges from PoW and believed to have an advantage. No need of expensive hardware (a normal laptop or computer running the respective coin’s Validator client will do as long as your laptop or computer is online) Energy efficient as it won’t consume high electricity as PoW does More loyal Validators As higher the stake the Validators have for a long time, more chances for the Validator to be picked up for “forging” and earn the transaction fee Faster validations Reference: https://medium.com/@karthik.seshu/cryptocurrency-proof-of-work-vs-proof-of-stake-e1eee1420b10 This eliminates the below challenges from PoW and believed to have an advantage.
No need of expensive hardware (a normal laptop or computer running the respective coin’s Validator client will do as long as your laptop or computer is online) Energy efficient as it won’t consume high electricity as PoW does More loyal Validators As higher the stake the Validators have for a long time, more chances for the Validator to be picked up for “forging” and earn the transaction fee Faster validations
Reference: https://medium.com/@karthik.seshu/cryptocurrency-proof-of-work-vs-proof-of-stake-e1eee1420b10
Question 8
Application Specific Integrated Circuit (ASIC) are used always in enterprise blockchains.
- TRUE
- FALSE
Correct answer: B
Explanation:
ASICS are generally used in blockchains such as BTC that have a Proof of Work consensus due to competition Reference: https://www.trymining.com/pages/asic-vs-gpu ASICS are generally used in blockchains such as BTC that have a Proof of Work consensus due to competition
Reference: https://www.trymining.com/pages/asic-vs-gpu
Question 9
Which of the following would NOT be true about what a smart contract gives your organization?
- Accuracy
- Savings
- Autonomy
- Trust
- Legal Assurance
Correct answer: E
Explanation:
Smart contracts generally are not legal contracts. However, its possible that a smart contract could be accepted as a legal contract but not normally. Read more about Smart contracts here Reference: https://blockgeeks.com/guides/smart-contracts/ Smart contracts generally are not legal contracts. However, its possible that a smart contract could be accepted as a legal contract but not normally. Read more about Smart contracts here
Reference: https://blockgeeks.com/guides/smart-contracts/
Question 10
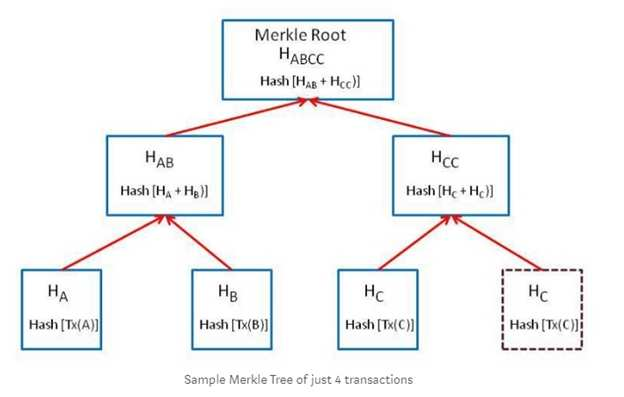
The ____________of the tree is the topmost node and hence this tree is represented upside down. The bottommost nodes are called as ________nodes. Each node is simply a cryptographic hash of a transaction.

In the above diagram, Transaction A,B, C,C from the leaves of the tree. Select one.
- Root, Hash
- Root, Leaf Nodes
- Has, Root nodes
- Leaf nodes, Root
- Leaf Nodes, Root
Correct answer: B
Explanation:
The root of the tree is the topmost node and hence this tree is represented upside down. The bottommost nodes are called as leaf nodes. Each node is simply a cryptographic hash of a transaction. In the above diagram, Transaction A,B,C,C form the leaves of the tree. Reference: https://medium.com/all-things-ledger/bitcoins-implementation-of-blockchain-2be713f662c2 The root of the tree is the topmost node and hence this tree is represented upside down. The bottommost nodes are called as leaf nodes. Each node is simply a cryptographic hash of a transaction. In the above diagram, Transaction A,B,C,C form the leaves of the tree.
Reference: https://medium.com/all-things-ledger/bitcoins-implementation-of-blockchain-2be713f662c2

