File Info
| Exam | Check Point Certified Security Master |
| Number | 156-115.77 |
| File Name | Checkpoint.156-115.77.RealExams.2018-10-05.179q.vcex |
| Size | 2 MB |
| Posted | Oct 05, 2018 |
| Download | Checkpoint.156-115.77.RealExams.2018-10-05.179q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
The command fw ctl kdebug <params> is used to:
- list enabled debug parameters.
- read the kernel debug buffer to obtain debug messages.
- enable kernel debugging.
- select specific kernel modules for debugging.
Correct answer: B
Question 2
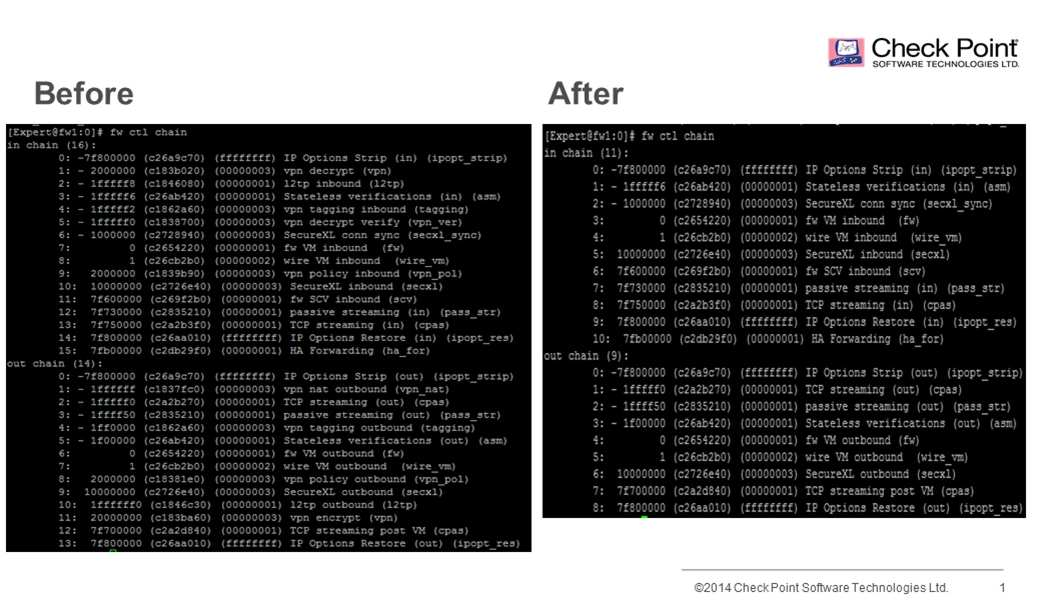
Compare these two images to establish which blade/feature was disabled on the firewall.

- IPS
- VPN
- NAT
- L2TP
Correct answer: B
Question 3
What command would give you a summary of all the tables available to the firewall kernel?
- fw tab
- fw tab -s
- fw tab -h
- fw tab -o
Correct answer: B
Question 4
What flag option(s) must be used to dump the complete table in friendly format, assuming there are more than one hundred connections in the table?
- fw tab -t connections -f
- fw tab -t connect -f -u
- fw tab -t connections -s
- fw tab -t connections -f –u
Correct answer: B
Question 5
Which directory below contains the URL Filtering engine update info? Here you can also go to see the status of the URL Filtering and Application Control updates.
- $FWDIR/urlf/update
- $FWDIR/appi/update
- $FWDIR/appi/urlf
- $FWDIR/update/appi
Correct answer: B
Question 6
You are troubleshooting a Security Gateway, attempting to determine which chain is causing a problem.
What command would you use to show all the chains through which traffic passed?
- [Expert@HostName]# fw ctl chain
- [Expert@HostName]# fw monitor -e "accept;" -p all
- [Expert@HostName]# fw ctl debug –m
- [Expert@HostName]# fw ctl zdebug all
Correct answer: B
Explanation:
Question 7
True or False: Software blades perform their inspection primarily through the kernel chain modules.
- False. Software blades do not pass through the chain modules.
- True. Many software blades have their own dedicated kernel chain module for inspection.
- True. All software blades are inspected by the IP Options chain module.
- True. Most software blades are inspected by the TCP streaming or Passive Streaming chain module.
Correct answer: B
Question 8
You are running a debugging session and you have set the debug environment to TDERROR_ALL_ALL=5 using the command export TDERROR_ALL_ALL=5.
How do you return the debug value to defaults?
- fw ctl debug 0x1ffffe0
- fw debug 0x1ffffe0
- export TDERROR_ALL_ALL
- unset TDERROR_ALL_ALL
Correct answer: D
Question 9
What command would you use to view which debugs are set in your current working environment?
- “env” and “fw ctl debug”
- “cat /proc/etc”
- “fw ctl debug all”
- “export”
Correct answer: A
Question 10
What causes the SIP Early NAT chain module to appear in the chain?
- The SIP traffic is trying to pass through the firewall.
- SIP is configured in IPS.
- A VOIP domain is configured.
- The default SIP service is used in the Rule Base.
Correct answer: D

