File Info
| Exam | Check Point Certified Security Master R80 |
| Number | 156-115.80 |
| File Name | Checkpoint.156-115.80.PracticeTest.2017-12-22.295q.vcex |
| Size | 5 MB |
| Posted | Dec 22, 2017 |
| Download | Checkpoint.156-115.80.PracticeTest.2017-12-22.295q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
What command would you use for a packet capture on an absolute position for TCP streaming (out) 1ffffe0
- fw ctl chain -po 1ffffe0 -o monitor.out
- fw monitor -po -0x1ffffe0 -o monitor.out
- fw monitor -e 0x1ffffe0 -o monitor.out
- fw monitor -pr 1ffffe0 -o monitor.out
Correct answer: B
Question 2
The command fw monitor -p all displays what type of information?
- It captures all points of the chain as the packet goes through the firewall kernel.
- This is not a valid command.
- The -p is used to resolve MAC address in the firewall capture.
- It does a firewall monitor capture on all interfaces.
Correct answer: A
Question 3
What does the IP Options Strip represent under the fw chain output?
- IP Options Strip is not a valid fw chain output.
- The IP Options Strip removes the IP header of the packet prior to be passed to the other kernel functions.
- The IP Options Strip copies the header details to forward the details for further IPS inspections.
- IP Options Strip is only used when VPN is involved.
Correct answer: B
Question 4
The command that lists the firewall kernel modules on a Security Gateway is:
- fw list kernel modules
- fw ctl kernel chain
- fw ctl debug -m
- fw list modules
Correct answer: C
Question 5
Which of the following BEST describes the command fw ctl chain function?
- View how CoreXL is distributing traffic among the firewall kernel instances.
- View established connections in the connections table.
- View the inbound and outbound kernel modules and the order in which they are applied.
- Determine if VPN Security Associations are being established.
Correct answer: C
Question 6
The command _____________ shows which firewall chain modules are active on a gateway.
- fw stat
- fw ctl debug
- fw ctl chain
- fw ctl multik stat
Correct answer: C
Question 7
The command fw ctl kdebug <params> is used to:
- list enabled debug parameters.
- read the kernel debug buffer to obtain debug messages.
- enable kernel debugging.
- select specific kernel modules for debugging.
Correct answer: B
Question 8
Compare these two images to establish which blade/feature was disabled on the firewall.
(Click the Exhibits button)
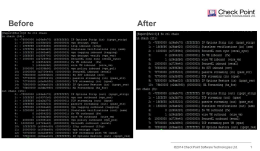

- IPS
- VPN
- NAT
- L2TP
Correct answer: B
Question 9
What command would give you a summary of all the tables available to the firewall kernel?
- fw tab
- fw tab -s
- fw tab -h
- fw tab -o
Correct answer: B
Question 10
What flag option(s) must be used to dump the complete table in friendly format, assuming there are more than one hundred connections in the table?
- fw tab -t connections -f
- fw tab -t connect -f -u
- fw tab -t connections -s
- fw tab -t connections -f –u
Correct answer: B

