File Info
| Exam | Check Point Certified Security Administrator |
| Number | 156-215.80 |
| File Name | Checkpoint.156-215.80.Pass4Sure.2018-11-12.251q.tqb |
| Size | 9 MB |
| Posted | Nov 12, 2018 |
| Download | Checkpoint.156-215.80.Pass4Sure.2018-11-12.251q.tqb |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
Packages and licenses are loaded from all of these sources EXCEPT
- Download Center Web site
- UserUpdate
- User Center
- Check Point DVD
Correct answer: B
Explanation:
Packages and licenses are loaded into these repositories from several sources: the Download Center web site (packages) the Check Point DVD (packages) the User Center (licenses) by importing a file (packages and licenses) by running the cplic command line Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_Installation_and_Upgrade_Guide-webAdmin/13128.htm Packages and licenses are loaded into these repositories from several sources:
- the Download Center web site (packages)
- the Check Point DVD (packages)
- the User Center (licenses)
- by importing a file (packages and licenses)
- by running the cplic command line
Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_Installation_and_Upgrade_Guide-webAdmin/13128.htm
Question 2
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
- INSPECT Engine
- Stateful Inspection
- Packet Filtering
- Application Layer Firewall
Correct answer: B
Explanation:
Reference: https://www.checkpoint.com/smb/help/utm1/8.2/7080.htm Reference: https://www.checkpoint.com/smb/help/utm1/8.2/7080.htm
Question 3
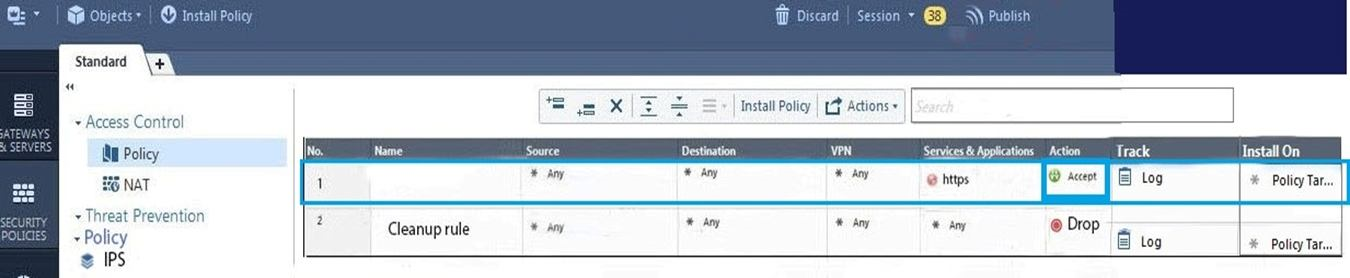
On the following graphic, you will find layers of policies.

What is a precedence of traffic inspection for the defined polices?
- A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if implicit Drop Rule drops the packet, it comes next to IPS layer and then after accepting the packet it passes to Threat Prevention layer.
- A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if there is any rule which accepts the packet, it comes next to IPS layer and then after accepting the packet it passes to Threat Prevention layer
- A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if there is any rule which accepts the packet, it comes next to Threat Prevention layer and then after accepting the packet it passes to IPS layer.
- A packet arrives at the gateway, it is checked against the rules in IPS policy layer and then it comes next to the Network policy layer and then after accepting the packet it passes to Threat Prevention layer.
Correct answer: B
Explanation:
To simplify Policy management, R80 organizes the policy into Policy Layers. A layer is a set of rules, or a Rule Base. For example, when you upgrade to R80 from earlier versions:* Gateways that have the Firewall and the Application Control Software Blades enabled will have their Access Control Policy split into two ordered layers: Network and Applications.When the gateway matches a rule in a layer, it starts to evaluate the rules in the next layer. * Gateways that have the IPS and Threat Emulation Software Blades enabled will have their Threat Prevention policies split into two parallel layers: IPS and Threat Prevention.All layers are evaluated in parallel Reference: https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197 To simplify Policy management, R80 organizes the policy into Policy Layers. A layer is a set of rules, or a Rule Base.
For example, when you upgrade to R80 from earlier versions:
* Gateways that have the Firewall and the Application Control Software Blades enabled will have their Access Control Policy split into two ordered layers: Network and Applications.
When the gateway matches a rule in a layer, it starts to evaluate the rules in the next layer.
* Gateways that have the IPS and Threat Emulation Software Blades enabled will have their Threat Prevention policies split into two parallel layers: IPS and Threat Prevention.
All layers are evaluated in parallel
Reference: https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?topic=documents/R80/CP_R80_SecMGMT/126197

