File Info
| Exam | Check Point Certified Security Administrator R81 |
| Number | 156-215.81 |
| File Name | Checkpoint.156-215.81.NewDumps.2022-07-09.50q.vcex |
| Size | 2 MB |
| Posted | Jul 09, 2022 |
| Download | Checkpoint.156-215.81.NewDumps.2022-07-09.50q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
Which set of objects have an Authentication tab?
- Templates, Users
- Users, Networks
- Users, User Group
- Networks, Hosts
Correct answer: A
Explanation:
Question 2
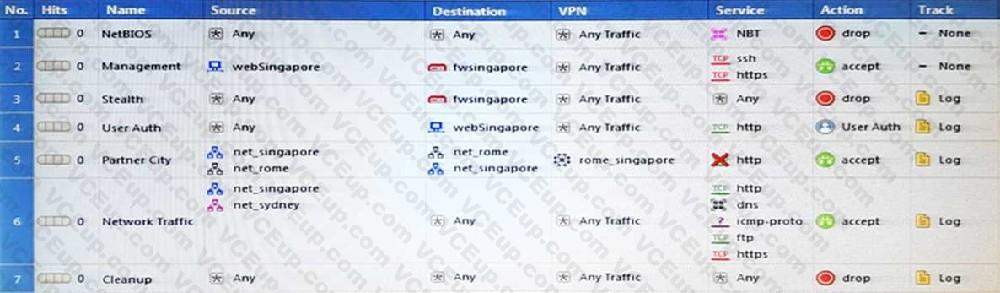
Which rule is responsible for the user authentication failure?

- Rule 4
- Rule 6
- Rule 3
- Rule 5
Correct answer: C
Explanation:
Question 3
Which tool CANNOT be launched from SmartUpdate R77?
- IP Appliance Voyager
- snapshot
- GAiA WebUI
- cpinfo
Correct answer: B
Explanation:
Question 4
Which of the following is a hash algorithm?
- 3DES
- IDEA
- DES
- MD5
Correct answer: D
Explanation:
Question 5
Katie has been asked to do a backup on the Blue Security Gateway. Which command would accomplish this in the Gaia CLI?
- Blue > add local backup
- Expert&Blue#add local backing
- Blue > set backup local
- Blue > add backup local
Correct answer: D
Explanation:
Question 6
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities sh you do first?
- Create a new logical-server object to represent your partner's CA
- Exchange exported CA keys and use them to create a new server object to represent your partner's Certificate Authority (CA)
- Manually import your partner's Certificate Revocation List.
- Manually import your partner's Access Control List.
Correct answer: B
Explanation:
Question 7
What must a Security Administrator do to comply with a management requirement to log all traffic accepted through the perimeter Security Gateway?
- In Global Properties > Reporting Tools check the box Enable tracking all rules (including rules marked as None in the Track column). Send these logs to a secondary log server for a complete logging history. Use your normal log serverfor standard logging for troubleshooting.
- Install the View Implicit Rules package using SmartUpdate.
- Define two log servers on the R77 Gateway object. Lof Implied Rules on the first log server. Enable Log Rule Base on the second log server. Use SmartReporter to merge the two log server records into the same database for HIPPA logaudits.
- Check the Log Implied Rules Globally box on the R77 Gateway object.
Correct answer: A
Explanation:
Question 8
What is the appropriate default Gaia Portal address?
- HTTP://[IPADDRESS]
- HTTPS://[IPADDRESS]:8080
- HTTPS://[IPADDRESS]:4434
- HTTPS://[IPADDRESS]
Correct answer: D
Explanation:
Question 9
Your boss wants you to closely monitor an employee suspected of transferring company secrets to the competition. The IT department discovered the suspect installed a WinSCP client in order to use encrypted communication. Which of the following methods is BEST to accomplish this task?
- Use SmartView Tracker to follow his actions by filtering log entries that feature the WinSCP destination port. Then, export the corresponding entries to a separate log file for documentation.
- Use SmartDashboard to add a rule in the firewall Rule Base that matches his IP address, and those of potential targets and suspicious protocols. Apply the alert action or customized messaging.
- Watch his IP in SmartView Monitor by setting an alert action to any packet that matches your Rule Base and his IP address for inbound and outbound traffic.
- Send the suspect an email with a keylogging Trojan attached, to get direct information about his wrongdoings.
Correct answer: A
Question 10
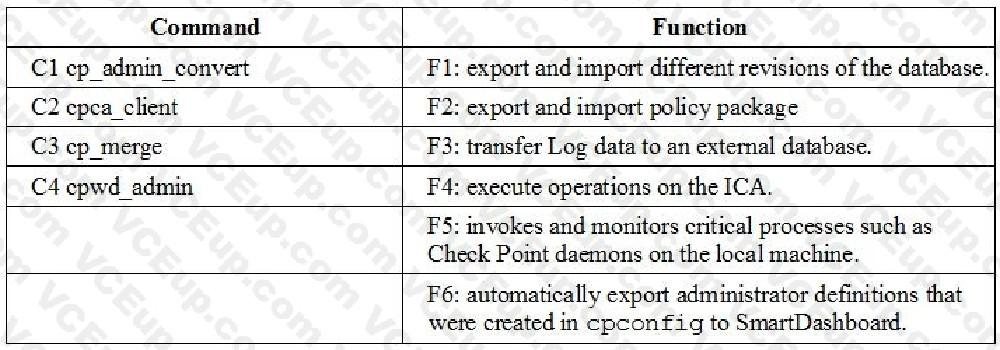
Match the following commands to their correct function. Each command has one function only listed.

- C1>F6; C2>F4; C3>F2; C4>F5
- C1>F2; C2>F1; C3>F6; C4>F4
- C1>F2; C2>F4; C3>F1; C4>F5
- C1>F4; C2>F6; C3>F3; C4>F5
Correct answer: A
Explanation:

