File Info
| Exam | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) |
| Number | 200-201 |
| File Name | Cisco.200-201.NewDumps.2023-08-02.60q.vcex |
| Size | 2 MB |
| Posted | Aug 02, 2023 |
| Downloads: | 1 |
| Download | Cisco.200-201.NewDumps.2023-08-02.60q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
- examination
- investigation
- collection
- reporting
Correct answer: C
Question 2
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
- syslog messages
- full packet capture
- NetFlow
- firewall event logs
Correct answer: C
Question 3
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
- context
- session
- laptop
- firewall logs
- threat actor
Correct answer: AE
Question 4
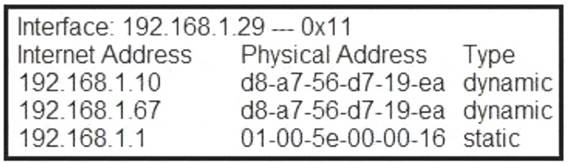
Refer to the exhibit.

What is occurring in this network?
- ARP cache poisoning
- DNS cache poisoning
- MAC address table overflow
- MAC flooding attack
Correct answer: A
Question 5
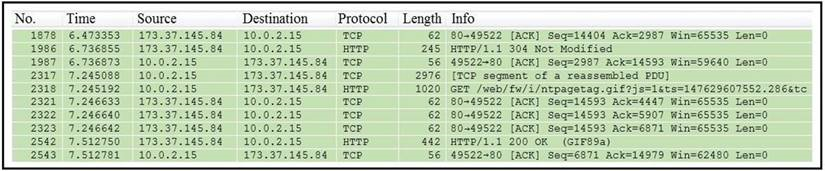
Refer to the exhibit.

Which packet contains a file that is extractable within Wireshark?
- 2317
- 1986
- 2318
- 2542
Correct answer: D
Question 6
Which process is used when IPS events are removed to improve data integrity?
- data availability
- data normalization
- data signature
- data protection
Correct answer: B
Question 7
Drag and drop the technology on the left onto the data type the technology provides on the right.
Correct answer: To work with this question, an Exam Simulator is required.
Question 8
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
- detection and analysis
- post-incident activity
- vulnerability management
- risk assessment
- vulnerability scoring
Correct answer: AB
Question 9
Which category relates to improper use or disclosure of PII data?
- legal
- compliance
- regulated
- contractual
Correct answer: C
Question 10
Which piece of information is needed for attribution in an investigation?
- proxy logs showing the source RFC 1918 IP addresses
- RDP allowed from the Internet
- known threat actor behavior
- 802.1x RADIUS authentication pass arid fail logs
Correct answer: C

