File Info
| Exam | Conducting Forensic Analysis & Incident Response Using Cisco Technologies for CyberOps |
| Number | 300-215 |
| File Name | Cisco.300-215.VCEplus.2020-12-17.58q.tqb |
| Size | 7 MB |
| Posted | Dec 17, 2020 |
| Download | Cisco.300-215.VCEplus.2020-12-17.58q.tqb |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
A security team is discussing lessons learned and suggesting process changes after a security breach incident. During the incident, members of the security team failed to report the abnormal system activity due to a high project workload.
Additionally, when the incident was identified, the response took six hours due to management being unavailable to provide the approvals needed. Which two steps will prevent these issues from occurring in the future? (Choose two.)
- Introduce a priority rating for incident response workloads.
- Provide phishing awareness training for the fill security team.
- Conduct a risk audit of the incident response workflow.
- Create an executive team delegation plan.
- Automate security alert timeframes with escalation triggers.
Correct answer: AE
Question 2
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected application on their workstation. Several alerts are seen from the intrusion detection system of unknown outgoing internet traffic from this workstation. The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
- Restore to a system recovery point.
- Replace the faulty CPU.
- Disconnect from the network.
- Format the workstation drives.
- Take an image of the workstation.
Correct answer: AE
Question 3
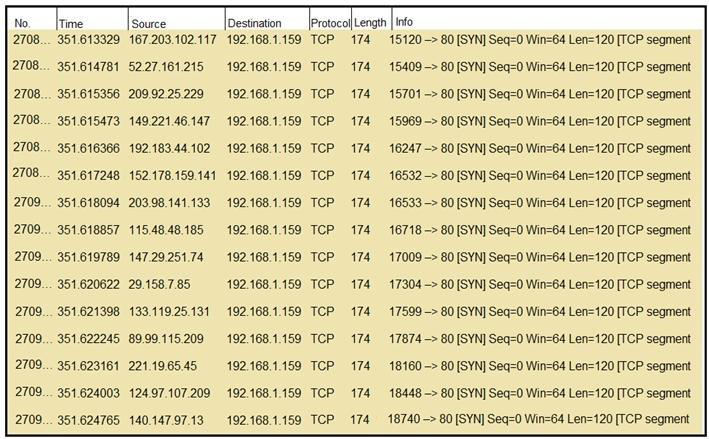
Refer to the exhibit. What should an engineer determine from this Wireshark capture of suspicious network traffic?

- There are signs of SYN flood attack, and the engineer should increase the backlog and recycle the oldest half-open TCP connections.
- There are signs of a malformed packet attack, and the engineer should limit the packet size and set a threshold of bytes as a countermeasure.
- There are signs of a DNS attack, and the engineer should hide the BIND version and restrict zone transfers as a countermeasure.
- There are signs of ARP spoofing, and the engineer should use Static ARP entries and IP address-to-MAC address mappings as a countermeasure.
Correct answer: A

