File Info
| Exam | Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) |
| Number | 350-401 |
| File Name | Cisco.350-401.Marks4Sure.2022-01-07.311q.vcex |
| Size | 29 MB |
| Posted | Jan 07, 2022 |
| Download | Cisco.350-401.Marks4Sure.2022-01-07.311q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
An engineer is implementing a Cisco MPLS TE tunnel to improve the streaming experience for the clients of a video-on-demand server. Which action must the engineer perform to configure extended discovery to support the MPLS LDP session between the headend and tailend routers?
- Configure the interface bandwidth to handle TCP and UDP traffic between the LDP peers
- Configure a Cisco MPLS TE tunnel on both ends of the session
- Configure an access list on the interface to permit TCP and UDP traffic
- Configure a targeted neighbor session.
Correct answer: B
Question 2
What is a characteristic of a next-generation firewall?
- only required at the network perimeter
- required in each layer of the network
- filters traffic using Layer 3 and Layer 4 information only
- provides intrusion prevention
Correct answer: D
Explanation:
The feature set for NGFWs build upon traditional firewall features by including critical security functions like intrusion prevention, VPN, and anti-virus, and even encrypted web traffic inspection to help prevent packets containing malicious content from entering the network The feature set for NGFWs build upon traditional firewall features by including critical security functions like intrusion prevention, VPN, and anti-virus, and even encrypted web traffic inspection to help prevent packets containing malicious content from entering the network
Question 3
What is the difference between a RIB and a FIB?
- The RIB is used to make IP source prefix-based switching decisions
- The FIB is where all IP routing information is stored
- The RIB maintains a mirror image of the FIB
- The FIB is populated based on RIB content
Correct answer: D
Explanation:
CEF uses a Forwarding Information Base (FIB) to make IP destination prefix-based switching decisions. The FIB is conceptually similar to a routing table or information base. It maintains a mirror image of the forwarding information contained in the IP routing table. When routing or topology changes occur in the network, the IP routing table is updated, and those changes are reflected in the FIB. The FIB maintains next-hop address information based on the information in the IP routing table. Because there is a one-to-one correlation between FIB entries and routing table entries, the FIB contains all known routes and eliminates the need for route cache maintenance that is associated with earlier switching paths such as fast switching and optimum switching. Note: In order to view the Routing information base (RIB) table, use the “show ip route” command. To view the Forwarding Information Base (FIB), use the “show ip cef” command. RIB is in Control plane while FIB is in Data plane. CEF uses a Forwarding Information Base (FIB) to make IP destination prefix-based switching decisions. The FIB is conceptually similar to a routing table or information base. It maintains a mirror image of the forwarding information contained in the IP routing table. When routing or topology changes occur in the network, the IP routing table is updated, and those changes are reflected in the FIB. The FIB maintains next-hop address information based on the information in the IP routing table. Because there is a one-to-one correlation between FIB entries and routing table entries, the FIB contains all known routes and eliminates the need for route cache maintenance that is associated with earlier switching paths such as fast switching and optimum switching.
Note: In order to view the Routing information base (RIB) table, use the “show ip route” command. To view the Forwarding Information Base (FIB), use the “show ip cef” command. RIB is in Control plane while FIB is in Data plane.
Question 4
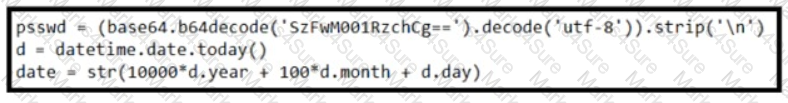

Refer to the exhibit. Which result does the python code achieve?
- The code encrypts a base64 decrypted password.
- The code converts time to the "year/month/day" time format.
- The code converts time to the yyyymmdd representation.
- The code converts time to the Epoch LINUX time format.
Correct answer: B
Question 5
In an SD-Access solution what is the role of a fabric edge node?
- to connect external Layer 3- network to the SD-Access fabric
- to connect wired endpoint to the SD-Access fabric
- to advertise fabric IP address space to external network
- to connect the fusion router to the SD-Access fabric
Correct answer: B
Explanation:
+ Fabric edge node: This fabric device (for example, access or distribution layer device) connects + Fabric edge node: This fabric device (for example, access or distribution layer device) connects
Question 6
Which three methods does Cisco DNA Centre use to discover devices? (Choose three)
- CDP
- SNMP
- LLDP
- ping
- NETCONF
- a specified range of IP addresses
Correct answer: ACF
Question 7
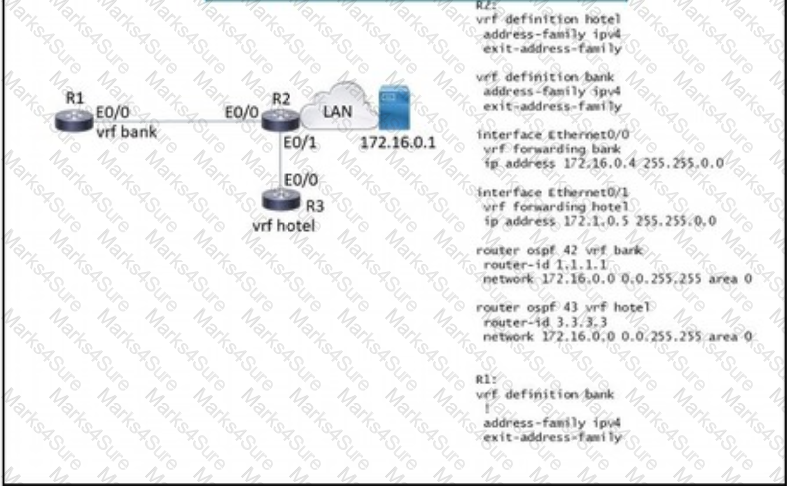


Refer to the exhibit. Which configuration must be applied to R1 to enable R1 to reach the server at 172.16.0.1?

- Option A
- Option B
- Option C
- Option D
Correct answer: D
Question 8
What is the responsibility of a secondary WLC?
- It shares the traffic load of the LAPs with the primary controller.
- It avoids congestion on the primary controller by sharing the registration load on the LAPs.
- It registers the LAPs if the primary controller fails.
- It enables Layer 2 and Layer 3 roaming between Itself and the primary controller.
Correct answer: C
Question 9
An engineer is concerned with the deployment of new application that is sensitive to inter-packet delay variance. Which command configures the router to be the destination of jitter measurements?
- Router(config)# ip sla responder udp-connect 172.29.139.134 5000
- Router(config)# ip sla responder tcp-connect 172.29.139.134 5000
- Router(config)# ip sla responder udp-echo 172.29.139.134 5000
- Router(config)# ip sla responder tcp-echo 172.29.139.134 5000
Correct answer: C
Question 10
Which NGFW mode block flows crossing the firewall?
- Passive
- Tap
- Inline tap
- Inline
Correct answer: D
Explanation:
Firepower Threat Defense (FTD) provides six interface modes which are: Routed, Switched, Inline Pair, Inline Pair with Tap, Passive, Passive (ERSPAN).When Inline Pair Mode is in use, packets can be blocked since they are processed inline When you use Inline Pair mode, the packet goes mainly through the FTD Snort engine When Tap Mode is enabled, a copy of the packet is inspected and dropped internally while the actual traffic goes through FTD unmodified Firepower Threat Defense (FTD) provides six interface modes which are: Routed, Switched, Inline Pair, Inline Pair with Tap, Passive, Passive (ERSPAN).When Inline Pair Mode is in use, packets can be blocked since they are processed inline When you use Inline Pair mode, the packet goes mainly through the FTD Snort engine When Tap Mode is enabled, a copy of the packet is inspected and dropped internally while the actual traffic goes through FTD unmodified

