File Info
| Exam | Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) |
| Number | 350-401 |
| File Name | Cisco.350-401.NewDumps.2021-05-25.375q.vcex |
| Size | 27 MB |
| Posted | May 25, 2021 |
| Download | Cisco.350-401.NewDumps.2021-05-25.375q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
A client with IP address 209 16b 201 2b must access a web server on port 80 at 209 I6b.200.22b. To allow this traffic. an engineer must add a statement to an access control list that is applied in the inbound direction on the port connecting to the web server Which statement allows this traffic?
- permit tcp host 209 165 200 225 eq 80 host 209.165.201.25
- permit tcp host 209 165.201 25 host 209.165.200.225 eq 80
- permit tcp host 209.165.200 225 It 80 host 209.165.201.25
- permit tcp host 209.165.200.225 host 209.165.201.25 eq 80
Correct answer: B
Question 2
What is a requirement for an Ansible-managed node?
- It must have an Ansible Tower installed.
- It must have an SSH server running
- It must support ad hoc commands
- It must be a Linux server or a Cisco device
Correct answer: B
Question 3
Drag and drop the virtual component from the left onto their descriptions on the right.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
+ configuration file containing settings for a virtual machine such as guest OS: VMX + component of a virtual machine responsible for sending packets to the hypervisor: vNIC + zip file containing a virtual machine configuration file and a virtual disk: OVA + file containing a virtual machine disk drive: VMDKThe VMX file simply holds the virtual machine configuration. VMDK (short for Virtual Machine Disk) is a file format that describes containers for virtual hard disk drives to be used in virtual machines like VMware Workstation or VirtualBox. An OVA file is an Open Virtualization Appliance that contains a compressed, "installable" version of a virtual machine. When you open an OVA file it extracts the VM and imports it into whatever virtualization software you have installed on your computer. + configuration file containing settings for a virtual machine such as guest OS: VMX
+ component of a virtual machine responsible for sending packets to the hypervisor: vNIC
+ zip file containing a virtual machine configuration file and a virtual disk: OVA
+ file containing a virtual machine disk drive: VMDK
The VMX file simply holds the virtual machine configuration. VMDK (short for Virtual Machine Disk) is a file format that describes containers for virtual hard disk drives to be used in virtual machines like VMware Workstation or VirtualBox. An OVA file is an Open Virtualization Appliance that contains a compressed, "installable" version of a virtual machine. When you open an OVA file it extracts the VM and imports it into whatever virtualization software you have installed on your computer.
Question 4
What is provided by the Stealthwatch component of the Cisco Cyber Threat Defense solution?
- real-time threat management to stop DDoS attacks to the core and access networks
- real-time awareness of users, devices and traffic on the network
- malware control
- dynamic threat control for web traffic
Correct answer: A
Question 5
Which benefit is offered by a cloud infrastructure deployment but is lacking in an on-premises deployment?
- efficient scalability
- virtualization
- storage capacity
- supported systems
Correct answer: A
Question 6
Which two characteristics define the Intent API provided by Cisco DNA Center? (Choose two.)
- northbound API
- business outcome oriented
- device-oriented
- southbound API
- procedural
Correct answer: AB
Explanation:
The Intent API is a Northbound REST API that exposes specific capabilities of the Cisco DNA Center platform. The Intent API provides policy-based abstraction of business intent, allowing focus on an outcome rather than struggling with individual mechanisms steps. Reference:https://developer.cisco.com/docs/dna-center/#!cisco-dna-center-platform-overview/intent-api- northbound The Intent API is a Northbound REST API that exposes specific capabilities of the Cisco DNA Center platform. The Intent API provides policy-based abstraction of business intent, allowing focus on an outcome rather than struggling with individual mechanisms steps.
Reference:
https://developer.cisco.com/docs/dna-center/#!cisco-dna-center-platform-overview/intent-api- northbound
Question 7
A client device fails to see the enterprise SSID, but other devices are connected to it. What is the cause of this issue?
- The hidden SSID was not manually configured on the client.
- The broadcast SSID was not manually configured on the client.
- The client has incorrect credentials stored for the configured hidden SSID.
- The client has incorrect credentials stored for the configured broadcast SSID.
Correct answer: A
Question 8
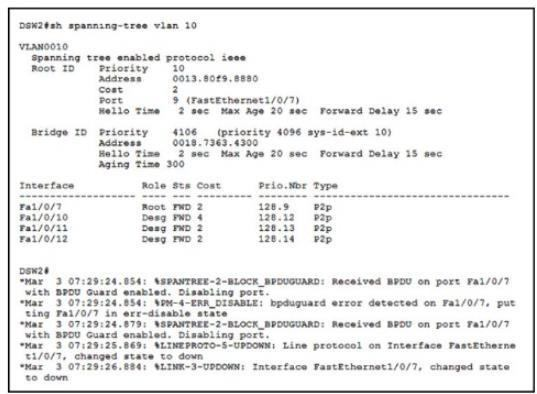

Refer to the exhibit.

An engineer entered the command no spanning-tree bpduguard enable on interface Fa 1/0/7. What is the effect of this command on Fa 1/0/7?
- It remains in err-disabled state until the shutdown/no shutdown command is entered in the interface configuration mode.
- It remains in err-disabled state until the errdisable recovery cause failed-port-state command is entered in the global configuration mode.
- It remains in err-disabled state until the no shutdown command is entered in the interface configuration mode.
- It remains in err-disabled state until the spanning-tree portfast bpduguard disable command is entered in the interface configuration mode.
Correct answer: A
Explanation:

Question 9
An engineer is describing QoS to a client. Which two facts apply to traffic policing? (Choose two.)
- Policing adapts to network congestion by queuing excess traffic
- Policing should be performed as close to the destination as possible
- Policing drops traffic that exceeds the defined rate
- Policing typically delays the traffic, rather than drops it IT Certification Guaranteed, The Easy Way!
- Policing should be performed as close to the source as possible
Correct answer: CE
Explanation:
Traffic policing propagates bursts. When the traffic rate reaches the configured maximum rate (or committed information rate), excess traffic is dropped (or remarked). The result is an output rate that appears as a saw-tooth with crests and troughs. Unlike traffic shaping, traffic policing does not cause delay. Classification (which includes traffic policing, traffic shaping and queuing techniques) should take place at the network edge. It is recommended that classification occur as close to the source of the traffic as possible. Also according to this Cisco link, "policing traffic as close to the source as possible". Traffic policing propagates bursts. When the traffic rate reaches the configured maximum rate (or committed information rate), excess traffic is dropped (or remarked). The result is an output rate that appears as a saw-tooth with crests and troughs.
Unlike traffic shaping, traffic policing does not cause delay. Classification (which includes traffic policing, traffic shaping and queuing techniques) should take place at the network edge. It is recommended that classification occur as close to the source of the traffic as possible.
Also according to this Cisco link, "policing traffic as close to the source as possible".
Question 10
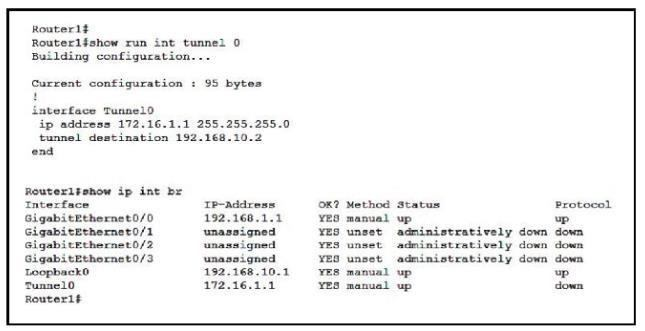
Refer to the exhibit.

Which command must be applied to Routed to bring the GRE tunnel to an up/up state?
- Router1(config)#interface tunnel0
- Router1(config-if)#tunnel source GigabitEthernet0/1
- Router1(config-if)#tunnel mode gre multipoint
- Router1(config-if)#tunnel source Loopback0
Correct answer: D
Explanation:
In order to make a Point-to-Point GRE Tunnel interface in up/up state, two requirements must be met: + A valid tunnel source (which is in up/up state and has an IP address configured on it) and tunnel destination must be configured + A valid tunnel destination is one which is routable. However, it does not have to be reachable. In order to make a Point-to-Point GRE Tunnel interface in up/up state, two requirements must be met: + A valid tunnel source (which is in up/up state and has an IP address configured on it) and tunnel destination must be configured + A valid tunnel destination is one which is routable. However, it does not have to be reachable.

