File Info
| Exam | Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) |
| Number | 350-401 |
| File Name | Cisco.350-401.PremiumDumps.2021-04-03.350q.vcex |
| Size | 13 MB |
| Posted | Apr 03, 2021 |
| Download | Cisco.350-401.PremiumDumps.2021-04-03.350q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
Drag and drop the solutions that comprise Cisco Cyber Threat Defense from the left onto the objectives they accomplish on the right.
Correct answer: To work with this question, an Exam Simulator is required.
Question 2
What are two characteristics of Cisco SD-Access elements? (Choose two)
- Fabric endpoints are connected directly to the border node
- The border node is required for communication between fabric and nonfabric devices
- The control plane node has the full RLOC-to-EID mapping database
- Traffic within the fabric always goes through the control plane node
- The border node has the full RLOC-to-EID mapping database
Correct answer: BC
Question 3
Refer to the exhibit.
Current configuration: 142 bytes
vrf definition STAFF
!
!
interface GigabitEthernet1
vrf forwarding STAFF
no ip address
negotiation auto
no mop enabled
no mop sysid
end
An engineer must assign an IP address of 192.168.1.1/24 to the GigabitEthemet1 interface. Which two commands must be added to the existing configuration to accomplish this task? (Choose two)
- Router(config-vrf)#address-family ipv6
- Router(config-if)#ip address 192.168.1.1 255.255.255.0
- Router(config-vrf)#ip address 192.168.1.1 255.255.255.0
- Router(config-if)#address-family ipv4
- Router(config-vrf)#address-family ipv4
Correct answer: BE
Question 4
What is the data policy in a Cisco SD-WAN deployment?
- list of ordered statements that define node configurations and authentication used within the SD-WAN overlay
- Set of statements that defines how data is forwarded based on IP packet information and specific VPNs
- detailed database mapping several kinds of addresses with their corresponding location
- group of services tested to guarantee devices and links liveliness within the SD -WAN overlay
Correct answer: B
Question 5

Refer to the exhibit.

Which action resolves the EtherChannel issue between SW2 and SW3?
- Configure switchport mode trunk on SW2
- Configure switchport nonegotiate on SW3
- Configure channel-group 1 mode desirable on both interfaces
- Configure channel-group 1 mode active on both interfaces
Correct answer: CD
Question 6

Refer to the exhibit.

A network engineer configures OSPF and reviews the router configuration. Which interface or interfaces are able to establish OSPF adjacency?
- GigabitEthemet0/1 and GigabitEthernet0/1.40
- Gigabit Ethernet0/0 and GigabitEthemet0/1
- only GigabitEthernet0/0
- only GigabitEthernet0/1
Correct answer: C
Question 7
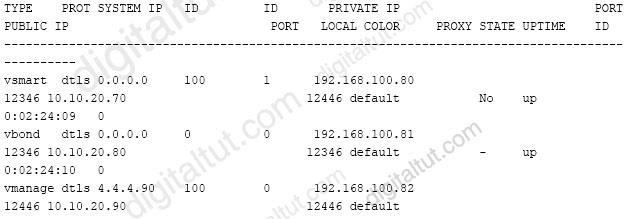
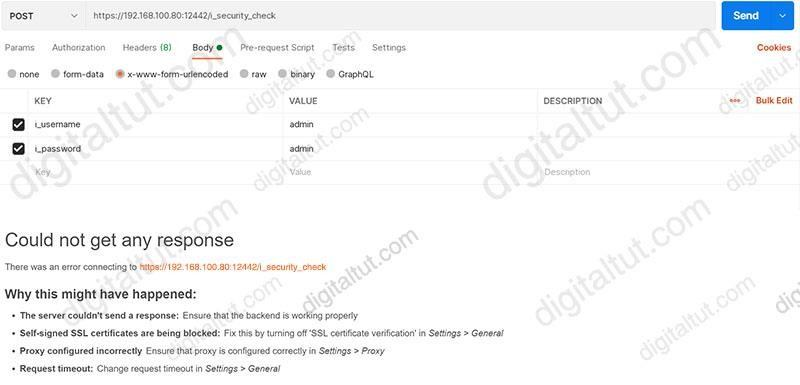
Refer to the exhibit.


What step resolves the authentication issue?
- restart the vsmart host
- target 192.168.100.82 in the URI
- change the port to 12446
- use basic authentication
Correct answer: B
Question 8
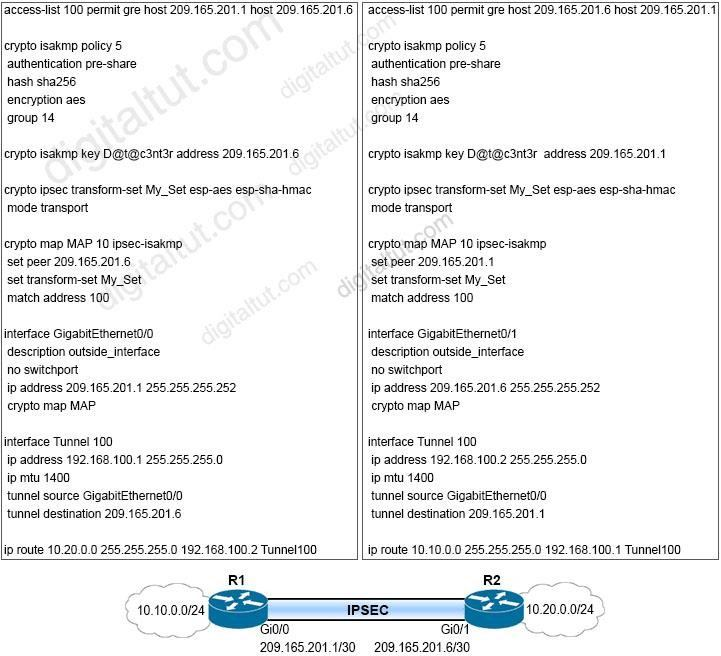
Refer to the exhibit.

A network engineer must simplify the IPsec configuration by enabling IPsec over GRE using IPsec profiles.
Which two configuration changes accomplish this? (Choose two)
- Apply the crypto map to the tunnel interface and change the tunnel mode to tunnel mode ipsec ipv4
- Remove all configuration related to crypto map from R1 and R2 and eliminate the ACL
- Remove the crypto map and modify the ACL to allow traffic between 10.10.0.0/24 to 10.20.0.0/24
- Create an IPsec profile, associate the transform-set, and apply the profile to the tunnel interface
Correct answer: AD
Question 9
Which encryption hashing algorithm does NTP use for authentication?
- SSL
- AES256
- AES128
- MD5
Correct answer: D
Question 10
What is a VPN in a Cisco SD-WAN deployment?
- virtual channel used to carry control plane information
- attribute to identify a set of services offered in specific places in the SD-WAN fabric
- common exchange point between two different services
- virtualized environment that provides traffic isolation and segmentation in the SD-WAN fabric
Correct answer: D

