File Info
| Exam | Implementing and Operating Cisco Security Core Technologies |
| Number | 350-701 |
| File Name | Cisco.350-701.NewDumps.2021-02-14.213q.vcex |
| Size | 6 MB |
| Posted | Feb 14, 2021 |
| Download | Cisco.350-701.NewDumps.2021-02-14.213q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
Which two key and block sizes are valid for AES? (Choose two.)
- 64-bit block size, 112-bit key length
- 64-bit block size, 168-bit key length
- 128-bit block size, 192-bit key length
- 128-bit block size, 256-bit key length
- 192-bit block size, 256-bit key length
Correct answer: CD
Question 2
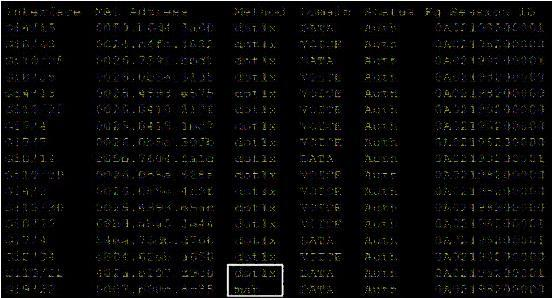
Refer to the exhibit.

Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?
- show authentication registrations
- show authentication method
- show dot1x all
- show authentication sessions
Correct answer: D
Question 3
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
- transparent
- redirection
- forward
- proxy gateway
Correct answer: A
Question 4
Which Cisco product is open, scalable, and built on IETF standards to allow multiple security products from Cisco and other vendors to share data and interoperate with each other?
- Platform Exchange Grid
- Advanced Malware Protection
- Multifactor Platform Integration
- Firepower Threat Defense
Correct answer: A
Question 5
Which PKI enrollment method allows the user to separate authentication and enrollment actions and also provides an option to specify HTTP/TFTP commands to perform file retrieval from the server?
- url
- profile
- terminal
- selfsigned
Correct answer: B
Question 6
What are two list types within AMP for Endpoints Outbreak Control? (Choose two.)
- blocked ports
- simple custom detections
- command and control
- allowed applications
- URL
Correct answer: BD
Question 7
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast packets have been flooding the network. What must be configured, based on a predefined threshold, to address this issue?
- Bridge Protocol Data Unit guard
- embedded event monitoring
- access control lists
- Storm Control
Correct answer: D
Explanation:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/eem/command/eem-cr-book/eem-cr-e1.html https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/eem/command/eem-cr-book/eem-cr-e1.html
Question 8
What is the purpose of the certificate signing request when adding a new certificate for a server?
- It is the password for the certificate that is needed to install it with.
- It provides the server information so a certificate can be created and signed
- It is the certificate that will be loaded onto the server
- It provides the certificate client information so the server can authenticate against it when installing
Correct answer: B
Explanation:
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_cert.html https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_cert.html
Question 9
In which cloud services model is the tenant responsible for virtual machine OS patching?
- IaaS
- UCaaS
- PaaS
- SaaS
Correct answer: A
Question 10
What is the benefit of installing Cisco AMP for Endpoints on a network?
- It provides operating system patches on the endpoints for security.
- It provides flow-based visibility for the endpoints' network connections.
- It protects endpoint systems through application control and real-time scanning.
- It enables behavioral analysis to be used for the endpoints.
Correct answer: C
Explanation:
https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/advanced-malware-protection/at-a-glance https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/advanced-malware-protection/at-a-glance

