File Info
| Exam | Implementing and Operating Cisco Security Core Technologies |
| Number | 350-701 |
| File Name | Cisco.350-701.TestKing.2020-03-05.61q.vcex |
| Size | 719 KB |
| Posted | Mar 05, 2020 |
| Download | Cisco.350-701.TestKing.2020-03-05.61q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
Which feature requires a network discovery policy on the Cisco Firepower Next Generation Intrusion Prevention System?
- security intelligence
- impact flags
- health monitoring
- URL filtering
Correct answer: A
Question 2
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention System?
- correlation
- intrusion
- access control
- network discovery
Correct answer: D
Question 3
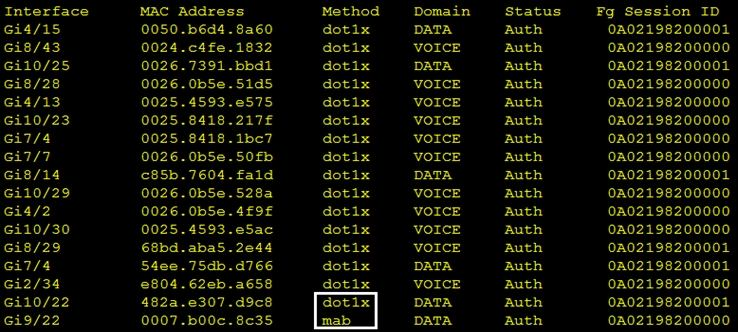

Refer to the exhibit. Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?
- show authentication registrations
- show authentication method
- show dot1x all
- show authentication sessions
Correct answer: B
Question 4
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?
- group policy
- access control policy
- device management policy
- platform service policy
Correct answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/622/configuration/guide/fpmc-config-guide-v622/platform_settings_policies_for_managed_devices.pdf Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/622/configuration/guide/fpmc-config-guide-v622/platform_settings_policies_for_managed_devices.pdf
Question 5
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the corporate network. The endpoints must have the corporate antivirus application installed and be running the latest build of Windows 10. What must the administrator implement to ensure that all devices are compliant before they are allowed on the network?
- Cisco Identity Services Engine and AnyConnect Posture module
- Cisco Stealthwatch and Cisco Identity Services Engine integration
- Cisco ASA firewall with Dynamic Access Policies configured
- Cisco Identity Services Engine with PxGrid services enabled
Correct answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect46/administration/guide/b_AnyConnect_Administrator_Guide_4-6/configure-posture.html Reference: https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect46/administration/guide/b_AnyConnect_Administrator_Guide_4-6/configure-posture.html
Question 6
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
- smurf
- distributed denial of service
- cross-site scripting
- rootkit exploit
Correct answer: C
Question 7
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two.)
- Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically.
- The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device.
- The IPsec configuration that is set up on the active device must be duplicated on the standby device.
- Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically.
- The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device.
Correct answer: BC
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnav/configuration/15-mt/sec-vpn-availability-15-mt-book/sec-state-fail-ipsec.html Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnav/configuration/15-mt/sec-vpn-availability-15-mt-book/sec-state-fail-ipsec.html
Question 8
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats?
- Application Control
- Security Category Blocking
- Content Category Blocking
- File Analysis
Correct answer: B
Explanation:
Reference: https://support.umbrella.com/hc/en-us/articles/115004563666-Understanding-Security-Categories Reference: https://support.umbrella.com/hc/en-us/articles/115004563666-Understanding-Security-Categories
Question 9
What two mechanisms are used to redirect users to a web portal to authenticate to ISE for guest services? (Choose two.)
- TACACS+
- central web auth
- single sign-on
- multiple factor auth
- local web auth
Correct answer: BE
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2-2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_01110.html Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2-2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_01110.html
Question 10
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
- user input validation in a web page or web application
- Linux and Windows operating systems
- database
- web page images
Correct answer: C
Explanation:
Reference: https://tools.cisco.com/security/center/resources/sql_injection Reference: https://tools.cisco.com/security/center/resources/sql_injection

