File Info
| Exam | Computer Hacking Forensic Investigator |
| Number | 312-49v10 |
| File Name | ECCouncil.312-49v10.VCEplus.2021-10-05.117q.vcex |
| Size | 1 MB |
| Posted | Oct 05, 2021 |
| Download | ECCouncil.312-49v10.VCEplus.2021-10-05.117q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
What information do you need to recover when searching a victim’s computer for a crime committed with specific e-mail message?
- Internet service provider information
- E-mail header
- Username and password
- Firewall log
Correct answer: B
Question 2
Melanie was newly assigned to an investigation and asked to make a copy of all the evidence from the compromised system. Melanie did a DOS copy of all the files on the system.
What would be the primary reason for you to recommend a disk imaging tool?
- A disk imaging tool would check for CRC32s for internal self-checking and validation and have MD5 checksum
- Evidence file format will contain case data entered by the examiner and encrypted at the beginning of the evidence file
- A simple DOS copy will not include deleted files, file slack and other information
- There is no case for an imaging tool as it will use a closed, proprietary format that if compared to the original will not match up sector for sector
Correct answer: C
Question 3
You are employed directly by an attorney to help investigate an alleged sexual harassment case at a large pharmaceutical manufacture. While at the corporate office of the company, the CEO demands to know the status of the investigation. What prevents you from discussing the case with the CEO?
- the attorney-work-product rule
- Good manners
- Trade secrets
- ISO 17799
Correct answer: A
Question 4
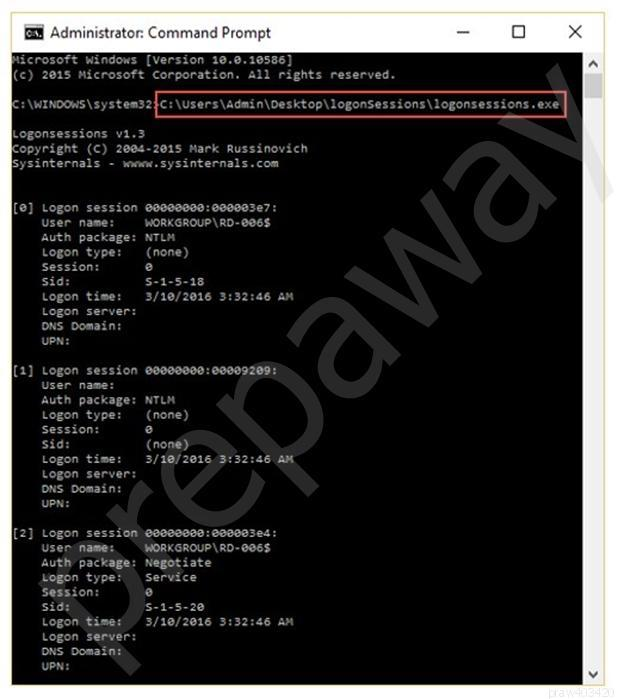
What is the investigator trying to analyze if the system gives the following image as output?

- All the logon sessions
- Currently active logon sessions
- Inactive logon sessions
- Details of users who can logon
Correct answer: B
Question 5
This organization maintains a database of hash signatures for known software.
- International Standards Organization
- Institute of Electrical and Electronics Engineers
- National Software Reference Library
- American National standards Institute
Correct answer: C
Question 6
The ____________________ refers to handing over the results of private investigations to the authorities because of indications of criminal activity.
- Locard Exchange Principle
- Clark Standard
- Kelly Policy
- Silver-Platter Doctrine
Correct answer: D
Explanation:
Question 7
You are working as Computer Forensics investigator and are called by the owner of an accounting firm to investigate possible computer abuse by one of the firm’s employees. You meet with the owner of the firm and discover that the company has never published a policy stating that they reserve the right to inspect their computing assets at will. What do you do?
- Inform the owner that conducting an investigation without a policy is not a problem because the company is privately owned
- Inform the owner that conducting an investigation without a policy is a violation of the 4th amendment
- Inform the owner that conducting an investigation without a policy is a violation of the employee’s expectation of privacy
- Inform the owner that conducting an investigation without a policy is not a problem because a policy is only necessary for government agencies
Correct answer: C
Question 8
During the course of a corporate investigation, you find that an Employee is committing a crime.
Can the Employer file a criminal complaint with Police?
- Yes, and all evidence can be turned over to the police
- Yes, but only if you turn the evidence over to a federal law enforcement agency
- No, because the investigation was conducted without following standard police procedures
- No, because the investigation was conducted without warrant
Correct answer: A
Question 9
____________________ is simply the application of Computer Investigation and analysis techniques in the interests of determining potential legal evidence.
- Network Forensics
- Computer Forensics
- Incident Response
- Event Reaction
Correct answer: B
Question 10
What is the name of the Standard Linux Command that is also available as windows application that can be used to create bit-stream images?
- mcopy
- image
- MD5
- dd
Correct answer: D
Explanation:

