File Info
| Exam | Certified Ethical Hacker v10 Exam |
| Number | 312-50v10 |
| File Name | ECCouncil.312-50v10.BrainDumps.2018-09-12.55q.vcex |
| Size | 45 KB |
| Posted | Sep 12, 2018 |
| Download | ECCouncil.312-50v10.BrainDumps.2018-09-12.55q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
PGP, SSL, and IKE are all examples of which type of cryptography?
- Hash Algorithm
- Digest
- Secret Key
- Public Key
Correct answer: D
Question 2
Which of the following is considered as one of the most reliable forms of TCP scanning?
- TCP Connect/Full Open Scan
- Half-open Scan
- NULL Scan
- Xmas Scan
Correct answer: A
Explanation:
Question 3
Which of the following scanning method splits the TCP header into several packets and makes it difficult for packet filters to detect the purpose of the packet?
- ICMP Echo scanning
- SYN/FIN scanning using IP fragments
- ACK flag probe scanning
- IPID scanning
Correct answer: B
Question 4
Which of the following is the BEST way to defend against network sniffing?
- Restrict Physical Access to Server Rooms hosting Critical Servers
- Use Static IP Address
- Using encryption protocols to secure network communications
- Register all machines MAC Address in a Centralized Database
Correct answer: C
Question 5
Websites and web portals that provide web services commonly use the Simple Object Access Protocol (SOAP).
Which of the following is an incorrect definition or characteristics of the protocol?
- Based on XML
- Only compatible with the application protocol HTTP
- Exchanges data between web services
- Provides a structured model for messaging
Correct answer: B
Question 6
You have gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your toolkit, you have an Ubuntu 9.10 Linux LiveCD. Which Linux-based tool can change any user’s password or activate disabled Windows accounts?
- John the Ripper
- SET
- CHNTPW
- Cain & Abel
Correct answer: C
Question 7
What type of vulnerability/attack is it when the malicious person forces the user’s browser to send an authenticated request to a server?
- Cross-site request forgery
- Cross-site scripting
- Session hijacking
- Server side request forgery
Correct answer: A
Explanation:
Question 8
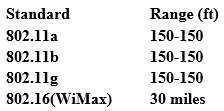
From the following table, identify the wrong answer in terms of Range (ft).
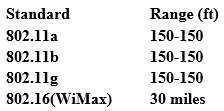
- 802.11b
- 802.11g
- 802.16(WiMax)
- 802.11a
Correct answer: D
Question 9
What would you enter, if you wanted to perform a stealth scan using Nmap?
- nmap -sU
- nmap -sS
- nmap -sM
- nmap -sT
Correct answer: B
Question 10
You are doing an internal security audit and intend to find out what ports are open on all the servers. What is the best way to find out?
- Scan servers with Nmap
- Scan servers with MBSA
- Telnet to every port on each server
- Physically go to each server
Correct answer: A

