File Info
| Exam | FCP-FortiAnalyzer 7.4 Analyst |
| Number | FCP_FAZ_AN-7.4 |
| File Name | Fortinet.FCP_FAZ_AN-7.4.VCEplus.2024-12-16.20q.vcex |
| Size | 839 KB |
| Posted | Dec 16, 2024 |
| Download | Fortinet.FCP_FAZ_AN-7.4.VCEplus.2024-12-16.20q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
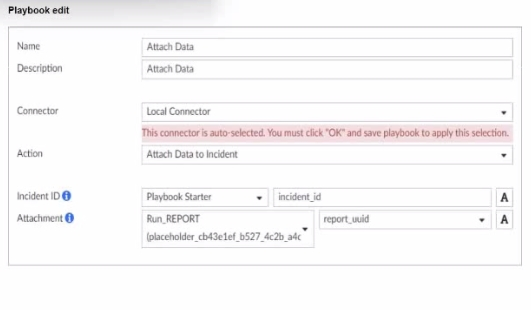
Exhibit.

What is the analyst trying to create?
- The analyst is trying to create a trigger variable to the used in the playbook.
- The analyst is trying to create an output variable to be used in the playbook.
- The analyst is trying to create a report in the playbook.
- The analyst is trying to create a SOC report in the playbook.
Correct answer: B
Explanation:
In the exhibit, the playbook configuration shows the analyst working with the 'Attach Data' action within a playbook. Here's a breakdown of key aspects:Incident ID: This field is linked to the 'Playbook Starter,' which indicates that the playbook will attach data to an existing incident.Attachment: The analyst is configuring an attachment by selecting Run_REPORT with a placeholder ID for report_uuid. This suggests that the report's UUID will dynamically populate as part of the playbook execution.Analysis of Options:Option A - Creating a Trigger Variable:A trigger variable would typically be set up in the playbook starter or initiation configuration, not within the 'Attach Data' action. The setup here does not indicate a trigger, as it's focusing on data attachment.Conclusion: Incorrect.Option B - Creating an Output Variable:The field Attachment with a report_uuid placeholder suggests that the analyst is defining an output variable that will store the report data or ID, allowing it to be attached to the incident. This variable can then be referenced or passed within the playbook for further actions or reporting.Conclusion: Correct.Option C - Creating a Report in the Playbook:While Run_REPORT is selected, it appears to be an attachment action rather than a report generation task. The purpose here is to attach an existing or dynamically generated report to an incident, not to create the report itself.Conclusion: Incorrect.Option D - Creating a SOC Report:Similarly, this configuration is focused on attaching data, not specifically generating a SOC report. SOC reports are generally predefined and generated outside the playbook.Conclusion: Incorrect.Conclusion:Correct Answe r : B. The analyst is trying to create an output variable to be used in the playbook.The setup allows the playbook to dynamically assign the report_uuid as an output variable, which can then be used in further actions within the playbook.FortiAnalyzer 7.4.1 documentation on playbook configurations, output variables, and data attachment functionalities. In the exhibit, the playbook configuration shows the analyst working with the 'Attach Data' action within a playbook. Here's a breakdown of key aspects:
Incident ID: This field is linked to the 'Playbook Starter,' which indicates that the playbook will attach data to an existing incident.
Attachment: The analyst is configuring an attachment by selecting Run_REPORT with a placeholder ID for report_uuid. This suggests that the report's UUID will dynamically populate as part of the playbook execution.
Analysis of Options:
Option A - Creating a Trigger Variable:
A trigger variable would typically be set up in the playbook starter or initiation configuration, not within the 'Attach Data' action. The setup here does not indicate a trigger, as it's focusing on data attachment.
Conclusion: Incorrect.
Option B - Creating an Output Variable:
The field Attachment with a report_uuid placeholder suggests that the analyst is defining an output variable that will store the report data or ID, allowing it to be attached to the incident. This variable can then be referenced or passed within the playbook for further actions or reporting.
Conclusion: Correct.
Option C - Creating a Report in the Playbook:
While Run_REPORT is selected, it appears to be an attachment action rather than a report generation task. The purpose here is to attach an existing or dynamically generated report to an incident, not to create the report itself.
Conclusion: Incorrect.
Option D - Creating a SOC Report:
Similarly, this configuration is focused on attaching data, not specifically generating a SOC report. SOC reports are generally predefined and generated outside the playbook.
Conclusion: Incorrect.
Conclusion:
Correct Answe r : B. The analyst is trying to create an output variable to be used in the playbook.
The setup allows the playbook to dynamically assign the report_uuid as an output variable, which can then be used in further actions within the playbook.
FortiAnalyzer 7.4.1 documentation on playbook configurations, output variables, and data attachment functionalities.
Question 2
Which FortiAnalyzer feature allows you to use a proactive approach when managing your network security?
- FortiView Monitor
- Outbreak alert services
- Incidents dashboard
- Threat hunting
Correct answer: D
Explanation:
FortiAnalyzer offers several features for monitoring, alerting, and incident management, each serving different purposes. Let's examine each option to determine which one best supports a proactive security approach.Option A - FortiView Monitor:FortiView is a visualization tool that provides real-time and historical insights into network traffic, threats, and logs. While it gives visibility into network activity, it is generally more reactive than proactive, as it relies on existing log data and incidents.Conclusion: Incorrect. Option B - Outbreak Alert Services:Outbreak Alert Services in FortiAnalyzer notify administrators of emerging threats and outbreaks based on FortiGuard intelligence. This is beneficial for awareness of potential threats but does not offer a hands-on, investigative approach. It's more of a notification service rather than an active, proactive investigation tool.Conclusion: Incorrect.Option C - Incidents Dashboard:The Incidents Dashboard provides a summary of incidents and current security statuses within the network. While it assists with ongoing incident response, it is used to manage and track existing incidents rather than proactively identifying new threats.Conclusion: Incorrect.Option D - Threat Hunting:Threat Hunting in FortiAnalyzer enables security analysts to actively search for hidden threats or malicious activities within the network by leveraging historical data, analytics, and intelligence. This is a proactive approach as it allows analysts to seek out threats before they escalate into incidents.Conclusion: Correct.Conclusion:Correct Answe r : D. Threat huntingThreat hunting is the most proactive feature among the options, as it involves actively searching for threats within the network rather than reacting to already detected incidents.FortiAnalyzer 7.4.1 documentation on Threat Hunting and proactive security measures. FortiAnalyzer offers several features for monitoring, alerting, and incident management, each serving different purposes. Let's examine each option to determine which one best supports a proactive security approach.
Option A - FortiView Monitor:
FortiView is a visualization tool that provides real-time and historical insights into network traffic, threats, and logs. While it gives visibility into network activity, it is generally more reactive than proactive, as it relies on existing log data and incidents.
Conclusion: Incorrect.
Option B - Outbreak Alert Services:
Outbreak Alert Services in FortiAnalyzer notify administrators of emerging threats and outbreaks based on FortiGuard intelligence. This is beneficial for awareness of potential threats but does not offer a hands-on, investigative approach. It's more of a notification service rather than an active, proactive investigation tool.
Conclusion: Incorrect.
Option C - Incidents Dashboard:
The Incidents Dashboard provides a summary of incidents and current security statuses within the network. While it assists with ongoing incident response, it is used to manage and track existing incidents rather than proactively identifying new threats.
Conclusion: Incorrect.
Option D - Threat Hunting:
Threat Hunting in FortiAnalyzer enables security analysts to actively search for hidden threats or malicious activities within the network by leveraging historical data, analytics, and intelligence. This is a proactive approach as it allows analysts to seek out threats before they escalate into incidents.
Conclusion: Correct.
Conclusion:
Correct Answe r : D. Threat hunting
Threat hunting is the most proactive feature among the options, as it involves actively searching for threats within the network rather than reacting to already detected incidents.
FortiAnalyzer 7.4.1 documentation on Threat Hunting and proactive security measures.
Question 3
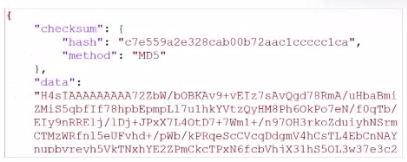
Refer to the exhibit with partial output:

Your colleague exported a playbook and has sent it to you for review. You open the file in a text editor and observer the output as shown in the exhibit.
Which statement about the export is true?
- The export data type is zipped.
- The playbook is misconfigured.
- The option to include the connector was not selected.
- Your colleague put a password on the export.
Correct answer: A
Explanation:
In the exhibit, the data structure shows a checksum field and a data field with a long, seemingly encoded string. This format is indicative of a file that has been compressed or encoded for storage and transfer.Export Data Type:The data field is likely a base64-encoded string, which is commonly used to represent binary data in text format. Base64 encoding is often applied to data that has been compressed (zipped) for easier handling and transfer.The checksum field, with an MD5 hash, provides a way to verify the integrity of the data after decompression. Option Analysis:A . The export data type is zipped: Correct. The compressed and encoded format of the data suggests that the export is in a zipped format, allowing for efficient storage and transfer.B . The playbook is misconfigured: There is no indication of misconfiguration in this exhibit. The presence of the checksum and data fields aligns with standard export practices.C . The option to include the connector was not selected: There is no evidence in the output to conclude that connectors are missing. Connectors are typically listed separately and would not directly affect the checksum and encoded data structure.D . Your colleague put a password on the export: There's no indication of password protection in the exhibit. Password protection would likely alter the data structure, and there would be some mention of encryption.Conclusion:Correct Answe r : A. The export data type is zipped.This answer is consistent with the typical use of base64 encoding for compressed (zipped) data exports in FortiAnalyzer.FortiAnalyzer 7.4.1 documentation on exporting playbooks and data compression methods. In the exhibit, the data structure shows a checksum field and a data field with a long, seemingly encoded string. This format is indicative of a file that has been compressed or encoded for storage and transfer.
Export Data Type:
The data field is likely a base64-encoded string, which is commonly used to represent binary data in text format. Base64 encoding is often applied to data that has been compressed (zipped) for easier handling and transfer.
The checksum field, with an MD5 hash, provides a way to verify the integrity of the data after decompression.
Option Analysis:
A . The export data type is zipped: Correct. The compressed and encoded format of the data suggests that the export is in a zipped format, allowing for efficient storage and transfer.
B . The playbook is misconfigured: There is no indication of misconfiguration in this exhibit. The presence of the checksum and data fields aligns with standard export practices.
C . The option to include the connector was not selected: There is no evidence in the output to conclude that connectors are missing. Connectors are typically listed separately and would not directly affect the checksum and encoded data structure.
D . Your colleague put a password on the export: There's no indication of password protection in the exhibit. Password protection would likely alter the data structure, and there would be some mention of encryption.
Conclusion:
Correct Answe r : A. The export data type is zipped.
This answer is consistent with the typical use of base64 encoding for compressed (zipped) data exports in FortiAnalyzer.
FortiAnalyzer 7.4.1 documentation on exporting playbooks and data compression methods.
Question 4
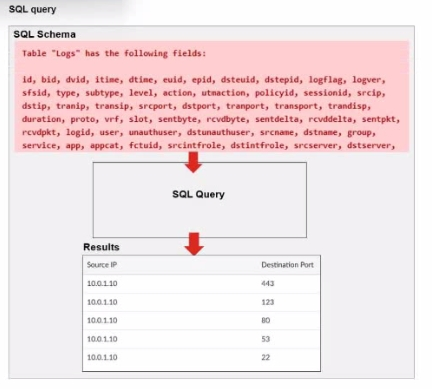
Exhibit.

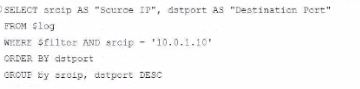
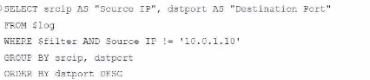
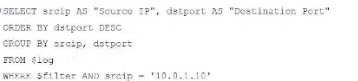
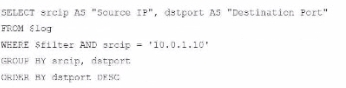
A fortiAnalyzer analyst is customizing a SQL query to use in a report.
Which SQL query should the analyst run to get the expected results?
Correct answer: A
Explanation:
The requirement here is to construct a SQL query that retrieves logs with specific fields, namely 'Source IP' and 'Destination Port,' for entries where the source IP address matches 10.0.1.10. The correct syntax is essential for selecting, filtering, ordering, and grouping the results as shown in the expected outcome.Analysis of the Options:Option A Explanation:SELECT srcip AS 'Source IP', dstport AS 'Destination Port': This syntax selects srcip and dstport, renaming them to 'Source IP' and 'Destination Port' respectively in the output.FROM $log: Specifies the log table as the data source.WHERE $filter AND srcip = '10.0.1.10': This line filters logs to only include entries with srcip equal to 10.0.1.10.ORDER BY dstport DESC: Orders the results in descending order by dstport.GROUP BY srcip, dstport: Groups results by srcip and dstport, which is valid SQL syntax.This option meets all the requirements to get the expected results accurately.Option B Explanation:WHERE $filter AND Source IP != '10.0.1.10': Uses != instead of =. This would exclude logs from the specified IP 10.0.1.10, which is contrary to the expected result.Option C Explanation:The ORDER BY clause appears before the FROM clause, which is incorrect syntax. SQL requires the FROM clause to follow the SELECT clause directly.Option D Explanation:The GROUP BY clause should follow the FROM clause. However, here, it's located after WHERE, making it syntactically incorrect.Conclusion:Correct Answe r : A. Option AThis option aligns perfectly with standard SQL syntax and filters correctly for srcip = '10.0.1.10', while ordering and grouping as required.FortiAnalyzer 7.4.1 SQL query capabilities and syntax for report customization. The requirement here is to construct a SQL query that retrieves logs with specific fields, namely 'Source IP' and 'Destination Port,' for entries where the source IP address matches 10.0.1.10. The correct syntax is essential for selecting, filtering, ordering, and grouping the results as shown in the expected outcome.
Analysis of the Options:
Option A Explanation:
SELECT srcip AS 'Source IP', dstport AS 'Destination Port': This syntax selects srcip and dstport, renaming them to 'Source IP' and 'Destination Port' respectively in the output.
FROM $log: Specifies the log table as the data source.
WHERE $filter AND srcip = '10.0.1.10': This line filters logs to only include entries with srcip equal to 10.0.1.10.
ORDER BY dstport DESC: Orders the results in descending order by dstport.
GROUP BY srcip, dstport: Groups results by srcip and dstport, which is valid SQL syntax.
This option meets all the requirements to get the expected results accurately.
Option B Explanation:
WHERE $filter AND Source IP != '10.0.1.10': Uses != instead of =. This would exclude logs from the specified IP 10.0.1.10, which is contrary to the expected result.
Option C Explanation:
The ORDER BY clause appears before the FROM clause, which is incorrect syntax. SQL requires the FROM clause to follow the SELECT clause directly.
Option D Explanation:
The GROUP BY clause should follow the FROM clause. However, here, it's located after WHERE, making it syntactically incorrect.
Conclusion:
Correct Answe r : A. Option A
This option aligns perfectly with standard SQL syntax and filters correctly for srcip = '10.0.1.10', while ordering and grouping as required.
FortiAnalyzer 7.4.1 SQL query capabilities and syntax for report customization.
Question 5
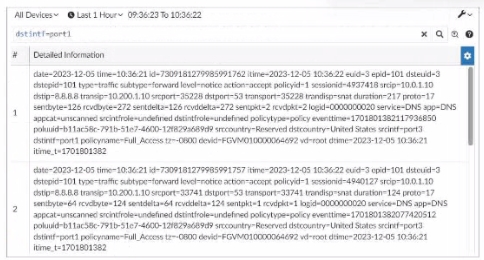
Exhibit.

What can you conclude about these search results? (Choose two.)
- They can be downloaded to a file.
- They are sortable by columns and customizable.
- They are not available for analysis in FortiView.
- They were searched by using text mode.
Correct answer: AD
Explanation:
In this exhibit, we observe a search query on the FortiAnalyzer interface displaying log data with details about the connection events, including fields like date, srcip, dstip, service, and dstintf. This setup allows for several functionalities within FortiAnalyzer.Option A - Download Capability:FortiAnalyzer provides the option to download search results and reports to a file in multiple formats, such as CSV or PDF, allowing for further offline analysis or archival. This makes it possible to save the search results shown in the exhibit to a file.Conclusion: Correct.Option B - Sorting and Customization:The FortiAnalyzer interface allows users to sort and customize columns for search results. This helps in organizing and viewing the logs in a manner that fits the analyst's needs, such as ordering logs by time, srcip, dstip, or other fields.Conclusion: Correct.Option C - Availability in FortiView:FortiView is a tool within FortiAnalyzer that visualizes data and provides analysis capabilities, including traffic and security event logs. Since these are traffic logs, they are typically available for visualization and analysis within FortiView.Conclusion: Incorrect.Option D - Text Mode Search:The search displayed here appears to be in a structured format, which implies it might be utilizing filters rather than a free-text search. FortiAnalyzer allows both structured searches and text searches, but there's no indication here that text mode was used.Conclusion: Incorrect.Conclusion:Correct Answe r : A. They can be downloaded to a file. and B. They are sortable by columns and customizable.These options are consistent with FortiAnalyzer's capabilities for managing, exporting, and customizing log data.FortiAnalyzer 7.4.1 documentation on search, export functionalities, and customizable views. In this exhibit, we observe a search query on the FortiAnalyzer interface displaying log data with details about the connection events, including fields like date, srcip, dstip, service, and dstintf. This setup allows for several functionalities within FortiAnalyzer.
Option A - Download Capability:
FortiAnalyzer provides the option to download search results and reports to a file in multiple formats, such as CSV or PDF, allowing for further offline analysis or archival. This makes it possible to save the search results shown in the exhibit to a file.
Conclusion: Correct.
Option B - Sorting and Customization:
The FortiAnalyzer interface allows users to sort and customize columns for search results. This helps in organizing and viewing the logs in a manner that fits the analyst's needs, such as ordering logs by time, srcip, dstip, or other fields.
Conclusion: Correct.
Option C - Availability in FortiView:
FortiView is a tool within FortiAnalyzer that visualizes data and provides analysis capabilities, including traffic and security event logs. Since these are traffic logs, they are typically available for visualization and analysis within FortiView.
Conclusion: Incorrect.
Option D - Text Mode Search:
The search displayed here appears to be in a structured format, which implies it might be utilizing filters rather than a free-text search. FortiAnalyzer allows both structured searches and text searches, but there's no indication here that text mode was used.
Conclusion: Incorrect.
Conclusion:
Correct Answe r : A. They can be downloaded to a file. and B. They are sortable by columns and customizable.
These options are consistent with FortiAnalyzer's capabilities for managing, exporting, and customizing log data.
FortiAnalyzer 7.4.1 documentation on search, export functionalities, and customizable views.
Question 6
Which two methods can you use to send notifications when an event occurs that matches a configured event handler? (Choose two.)
- Send Alert through Fabric Connectors
- Send SNMP trap
- Send SMS notification
- Send Alert through FortiSIEM MEA
Correct answer: BC
Explanation:
In FortiAnalyzer, event handlers can be configured to trigger specific notifications when an event matches defined criteria. These notifications are designed to alert administrators in real time about critical events.Option B - Send SNMP Trap:FortiAnalyzer supports sending SNMP traps as one of the notification methods when an event matches an event handler. This allows integration with SNMP-enabled network management systems, which can then trigger further alerts or actions based on the trap received.Conclusion: Correct.Option C - Send SMS Notification:FortiAnalyzer also supports SMS notifications, enabling alerts to be sent via SMS to predefined recipients. This method is useful for administrators who require immediate alerts but may not have access to email or other notification systems at all times.Conclusion: Correct.Option A - Send Alert through Fabric Connectors:While Fabric Connectors allow FortiAnalyzer to interact with other parts of the Security Fabric, they are primarily used for data sharing and automation rather than directly for sending alerts or notifications.Conclusion: Incorrect.Option D - Send Alert through FortiSIEM MEA:FortiSIEM integration allows for data sharing and further analysis within the Fortinet ecosystem, but it does not directly act as a notification method from FortiAnalyzer itself.Conclusion: Incorrect.Conclusion:Correct Answe r : B. Send SNMP trap and C. Send SMS notificationThese options represent valid notification methods for FortiAnalyzer's event handler configuration.FortiAnalyzer 7.4.1 documentation on event handler configuration and available notification methods. In FortiAnalyzer, event handlers can be configured to trigger specific notifications when an event matches defined criteria. These notifications are designed to alert administrators in real time about critical events.
Option B - Send SNMP Trap:
FortiAnalyzer supports sending SNMP traps as one of the notification methods when an event matches an event handler. This allows integration with SNMP-enabled network management systems, which can then trigger further alerts or actions based on the trap received.
Conclusion: Correct.
Option C - Send SMS Notification:
FortiAnalyzer also supports SMS notifications, enabling alerts to be sent via SMS to predefined recipients. This method is useful for administrators who require immediate alerts but may not have access to email or other notification systems at all times.
Conclusion: Correct.
Option A - Send Alert through Fabric Connectors:
While Fabric Connectors allow FortiAnalyzer to interact with other parts of the Security Fabric, they are primarily used for data sharing and automation rather than directly for sending alerts or notifications.
Conclusion: Incorrect.
Option D - Send Alert through FortiSIEM MEA:
FortiSIEM integration allows for data sharing and further analysis within the Fortinet ecosystem, but it does not directly act as a notification method from FortiAnalyzer itself.
Conclusion: Incorrect.
Conclusion:
Correct Answe r : B. Send SNMP trap and C. Send SMS notification
These options represent valid notification methods for FortiAnalyzer's event handler configuration.
FortiAnalyzer 7.4.1 documentation on event handler configuration and available notification methods.
Question 7
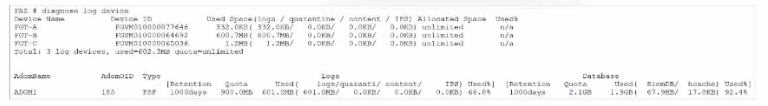
Exhibit.

What can you conclude from this output?
- There is not disk quota allocated to quarantining files.
- FGT_B is the Security Fabric root.
- The allocated disk quote to ADOM1 is 3 GB.
- Archive logs are using more space than analytic logs.
Correct answer: C
Explanation:
The exhibit displays a diagnose log device output on a FortiAnalyzer, showing details about disk space usage and quotas for different FortiGate devices and ADOMs (Administrative Domains). Here's a breakdown of key details: Disk Quota for Quarantined Files:The output includes columns labeled for used space in categories such as 'logs,' 'quarantine,' 'content,' and 'DB.' For each device, the quarantine column consistently shows 0.0KB used, indicating that there is no disk quota allocated or utilized for quarantining files.Conclusion: Correct.FGT_B as Security Fabric Root:There is no direct indication from this output that specifies FGT_B is the root of the Security Fabric. Information on Security Fabric topology or root designation would typically come from a Security Fabric configuration command rather than a disk usage summary.Conclusion: Incorrect.Allocated Disk Quota for ADOM1:The output shows the quota for ADOM1 is 'unlimited,' not a fixed 3 GB quota. Therefore, there is no set 3 GB limit for ADOM1.Conclusion: Incorrect.Comparison of Archive Logs and Analytic Logs:The output does not differentiate between archive logs and analytic logs; it only shows overall disk usage by type (e.g., logs, quarantine). Therefore, no conclusion can be made about which type of logs (archive or analytic) is using more space.Conclusion: Incorrect.Conclusion:Correct Answe r : A. There is no disk quota allocated to quarantining files.This answer aligns with the observed data, where no disk space is used or allocated for quarantine files.FortiAnalyzer 7.4.1 documentation on diagnose log device command usage and disk quota settings. The exhibit displays a diagnose log device output on a FortiAnalyzer, showing details about disk space usage and quotas for different FortiGate devices and ADOMs (Administrative Domains). Here's a breakdown of key details:
Disk Quota for Quarantined Files:
The output includes columns labeled for used space in categories such as 'logs,' 'quarantine,' 'content,' and 'DB.' For each device, the quarantine column consistently shows 0.0KB used, indicating that there is no disk quota allocated or utilized for quarantining files.
Conclusion: Correct.
FGT_B as Security Fabric Root:
There is no direct indication from this output that specifies FGT_B is the root of the Security Fabric. Information on Security Fabric topology or root designation would typically come from a Security Fabric configuration command rather than a disk usage summary.
Conclusion: Incorrect.
Allocated Disk Quota for ADOM1:
The output shows the quota for ADOM1 is 'unlimited,' not a fixed 3 GB quota. Therefore, there is no set 3 GB limit for ADOM1.
Conclusion: Incorrect.
Comparison of Archive Logs and Analytic Logs:
The output does not differentiate between archive logs and analytic logs; it only shows overall disk usage by type (e.g., logs, quarantine). Therefore, no conclusion can be made about which type of logs (archive or analytic) is using more space.
Conclusion: Incorrect.
Conclusion:
Correct Answe r : A. There is no disk quota allocated to quarantining files.
This answer aligns with the observed data, where no disk space is used or allocated for quarantine files.
FortiAnalyzer 7.4.1 documentation on diagnose log device command usage and disk quota settings.
Question 8
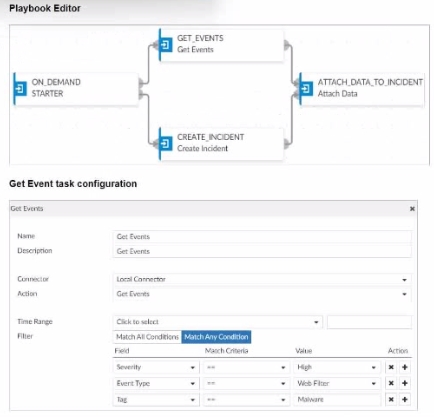
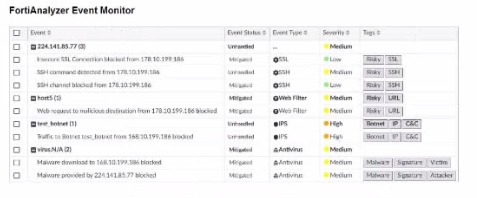
Exhibit.


Assume these are all the events that exist on the FortiAnalyzer device.
How many events will be added to the incident created after running this playbook?
- Eleven events will be added.
- Seven events will be added
- No events will be added.
- Four events will be added.
Correct answer: D
Explanation:
In the exhibit, we see a playbook in FortiAnalyzer designed to retrieve events based on specific criteria, create an incident, and attach relevant data to that incident. The 'Get Event' task configuration specifies filters to match any of the following conditions:Severity = HighEvent Type = Web FilterTag = MalwareAnalysis of Events:In the FortiAnalyzer Event Monitor list:We need to identify events that meet any one of the specified conditions (since the filter is set to 'Match Any Condition').Events Matching Criteria:Severity = High:There are two events with 'High' severity, both with the 'Event Type' IPS.Event Type = Web Filter:There are two events with the 'Event Type' Web Filter. One has a 'Medium' severity, and the other has a 'Low' severity.Tag = Malware:There are two events tagged with 'Malware,' both with the 'Event Type' Antivirus and 'Medium' severity.After filtering based on these criteria, there are four distinct events:Two from the 'Severity = High' filter.One from the 'Event Type = Web Filter' filter.One from the 'Tag = Malware' filter.Conclusion:Correct Answe r : D. Four events will be added.This answer matches the conditions set in the playbook filter configuration and the events listed in the Event Monitor.FortiAnalyzer 7.4.1 documentation on event filtering, playbook configuration, and incident management criteria. In the exhibit, we see a playbook in FortiAnalyzer designed to retrieve events based on specific criteria, create an incident, and attach relevant data to that incident. The 'Get Event' task configuration specifies filters to match any of the following conditions:
Severity = High
Event Type = Web Filter
Tag = Malware
Analysis of Events:
In the FortiAnalyzer Event Monitor list:
We need to identify events that meet any one of the specified conditions (since the filter is set to 'Match Any Condition').
Events Matching Criteria:
Severity = High:
There are two events with 'High' severity, both with the 'Event Type' IPS.
Event Type = Web Filter:
There are two events with the 'Event Type' Web Filter. One has a 'Medium' severity, and the other has a 'Low' severity.
Tag = Malware:
There are two events tagged with 'Malware,' both with the 'Event Type' Antivirus and 'Medium' severity.
After filtering based on these criteria, there are four distinct events:
Two from the 'Severity = High' filter.
One from the 'Event Type = Web Filter' filter.
One from the 'Tag = Malware' filter.
Conclusion:
Correct Answe r : D. Four events will be added.
This answer matches the conditions set in the playbook filter configuration and the events listed in the Event Monitor.
FortiAnalyzer 7.4.1 documentation on event filtering, playbook configuration, and incident management criteria.
Question 9
Which statement about SQL SELECT queries is true?
- They can be used to purge log entries from the database.
- They must be followed immediately by a WHERE clause.
- They can be used to display the database schema.
- They are not used in macros.
Correct answer: D
Explanation:
Option A - Purging Log Entries:A SELECT query in SQL is used to retrieve data from a database and does not have the capability to delete or purge log entries. Purging logs typically requires a DELETE or TRUNCATE command.Conclusion: Incorrect.Option B - WHERE Clause Requirement:In SQL, a SELECT query does not require a WHERE clause. The WHERE clause is optional and is used only when filtering results. A SELECT query can be executed without it, meaning this statement is false.Conclusion: Incorrect.Option C - Displaying Database Schema:A SELECT query retrieves data from specified tables, but it is not used to display the structure or schema of the database. Commands like DESCRIBE, SHOW TABLES, or SHOW COLUMNS are typically used to view schema information.Conclusion: Incorrect.Option D - Usage in Macros:FortiAnalyzer and similar systems often use macros for automated functions or specific query-based tasks. SELECT queries are typically not included in macros because macros focus on procedural or repetitive actions, rather than simple data retrieval.Conclusion: Correct.Conclusion:Correct Answe r : D. They are not used in macros.This aligns with typical SQL usage and the specific functionalities of FortiAnalyzer.FortiAnalyzer 7.4.1 documentation on SQL queries, database operations, and macro usage. Option A - Purging Log Entries:
A SELECT query in SQL is used to retrieve data from a database and does not have the capability to delete or purge log entries. Purging logs typically requires a DELETE or TRUNCATE command.
Conclusion: Incorrect.
Option B - WHERE Clause Requirement:
In SQL, a SELECT query does not require a WHERE clause. The WHERE clause is optional and is used only when filtering results. A SELECT query can be executed without it, meaning this statement is false.
Conclusion: Incorrect.
Option C - Displaying Database Schema:
A SELECT query retrieves data from specified tables, but it is not used to display the structure or schema of the database. Commands like DESCRIBE, SHOW TABLES, or SHOW COLUMNS are typically used to view schema information.
Conclusion: Incorrect.
Option D - Usage in Macros:
FortiAnalyzer and similar systems often use macros for automated functions or specific query-based tasks. SELECT queries are typically not included in macros because macros focus on procedural or repetitive actions, rather than simple data retrieval.
Conclusion: Correct.
Conclusion:
Correct Answe r : D. They are not used in macros.
This aligns with typical SQL usage and the specific functionalities of FortiAnalyzer.
FortiAnalyzer 7.4.1 documentation on SQL queries, database operations, and macro usage.
Question 10
You find that as part of your role as an analyst, you frequently search log View using the same parameters.
Instead of defining your search filters repeatedly, what can you do to save time?
- Configure a custom dashboard.
- Configure a custom view.
- Configure a data selector.
- Configure a marco and apply it to device groups.
Correct answer: B
Explanation:
When you frequently use the same search parameters in FortiAnalyzer's Log View, setting up a reusable filter or view can save considerable time. Here's an analysis of each option:Option A - Configure a Custom Dashboard:Custom dashboards are useful for displaying a variety of widgets and summaries on network activity, performance, and threat data, but they are not designed for storing specific search filters for log views.Conclusion: Incorrect.Option B - Configure a Custom View:Custom views in FortiAnalyzer allow analysts to save specific search filters and configurations. By setting up a custom view, you can retain your frequently used search parameters and quickly access them without needing to reapply filters each time. This option is specifically designed to streamline the process of recurring log searches.Conclusion: Correct.Option C - Configure a Data Selector:Data selectors are used to define specific types of data for FortiAnalyzer reports and widgets. They are useful in reports but are not meant for saving and reusing log search parameters in Log View.Conclusion: Incorrect.Option D - Configure a Macro and Apply It to Device Groups:Macros in FortiAnalyzer are generally used for automation tasks, not for saving log search filters. Applying macros to device groups does not fulfill the requirement of saving specific log view search parameters. Conclusion: Incorrect.Conclusion:Correct Answe r : B. Configure a custom view.Custom views allow you to save specific search filters, enabling quick access to frequently used parameters in Log View.FortiAnalyzer 7.4.1 documentation on creating and using custom views for log searches. When you frequently use the same search parameters in FortiAnalyzer's Log View, setting up a reusable filter or view can save considerable time. Here's an analysis of each option:
Option A - Configure a Custom Dashboard:
Custom dashboards are useful for displaying a variety of widgets and summaries on network activity, performance, and threat data, but they are not designed for storing specific search filters for log views.
Conclusion: Incorrect.
Option B - Configure a Custom View:
Custom views in FortiAnalyzer allow analysts to save specific search filters and configurations. By setting up a custom view, you can retain your frequently used search parameters and quickly access them without needing to reapply filters each time. This option is specifically designed to streamline the process of recurring log searches.
Conclusion: Correct.
Option C - Configure a Data Selector:
Data selectors are used to define specific types of data for FortiAnalyzer reports and widgets. They are useful in reports but are not meant for saving and reusing log search parameters in Log View.
Conclusion: Incorrect.
Option D - Configure a Macro and Apply It to Device Groups:
Macros in FortiAnalyzer are generally used for automation tasks, not for saving log search filters. Applying macros to device groups does not fulfill the requirement of saving specific log view search parameters.
Conclusion: Incorrect.
Conclusion:
Correct Answe r : B. Configure a custom view.
Custom views allow you to save specific search filters, enabling quick access to frequently used parameters in Log View.
FortiAnalyzer 7.4.1 documentation on creating and using custom views for log searches.