File Info
| Exam | Fortinet NSE 4 - FortiOS 7.0 |
| Number | NSE4_FGT-7.0 |
| File Name | Fortinet.NSE4_FGT-7.0.CertDumps.2023-01-01.172q.vcex |
| Size | 12 MB |
| Posted | Jan 01, 2023 |
| Download | Fortinet.NSE4_FGT-7.0.CertDumps.2023-01-01.172q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
Which two statements about antivirus scanning mode are true? (Choose two.)
- In proxy-based inspection mode, files bigger than the buffer size are scanned.
- In flow-based inspection mode, FortiGate buffers the file, but also simultaneously transmits it to the client.
- In proxy-based inspection mode, antivirus scanning buffers the whole file for scanning, before sending it to the client.
- In flow-based inspection mode, files bigger than the buffer size are scanned.
Correct answer: BC
Explanation:
An antivirus profile in full scan mode buffers up to your specified file size limit. The default is 10 MB. That is large enough for most files, except video files. If your FortiGate model has more RAM, you may be able to increase this threshold. Without a limit, very large files could exhaust the scan memory. So, this threshold balances risk and performance. Is this tradeoff unique to FortiGate, or to a specific model? No.Regardless of vendor or model, you must make a choice. This is because of the difference between scans in theory, that have no limits, and scans on real-world devices, that have finite RAM. In order to detect 100% of malware regardless of file size, a firewall would need infinitely large RAM--something that no device has in the real world. Most viruses are very small. This table shows a typical tradeoff. You can see that with the default 10 MB threshold, only 0.01% of viruses pass through. An antivirus profile in full scan mode buffers up to your specified file size limit. The default is 10 MB. That is large enough for most files, except video files. If your FortiGate model has more RAM, you may be able to increase this threshold. Without a limit, very large files could exhaust the scan memory. So, this threshold balances risk and performance. Is this tradeoff unique to FortiGate, or to a specific model? No.
Regardless of vendor or model, you must make a choice. This is because of the difference between scans in theory, that have no limits, and scans on real-world devices, that have finite RAM. In order to detect 100% of malware regardless of file size, a firewall would need infinitely large RAM--something that no device has in the real world. Most viruses are very small. This table shows a typical tradeoff. You can see that with the default 10 MB threshold, only 0.01% of viruses pass through.
Question 2
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for example.com home page, the override must be configured using a specific syntax.
Which two syntaxes are correct to configure web rating for the home page? (Choose two.)
- www.example.com:443
- example.com
Correct answer: BC
Explanation:
FortiGate_Security_6.4 page 384When using FortiGuard category filtering to allow or block access to a website, one option is to make a web rating override and define the website in a different category. Web ratings are only for host names--"no URLs or wildcard characters are allowed". FortiGate_Security_6.4 page 384
When using FortiGuard category filtering to allow or block access to a website, one option is to make a web rating override and define the website in a different category. Web ratings are only for host names--"no URLs or wildcard characters are allowed".
Question 3
An administrator is configuring an IPsec VPN between site A and site A. The Remote Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192.168.1.0/24 and the remote quick mode selector is 192.168.2.0/24.Which subnet must the administrator configure for the local quick mode selector for site B?
- 192.168.1.0/24
- 192.168.0.0/24
- 192.168.2.0/24
- 192.168.3.0/24
Correct answer: C
Question 4
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
- get system status
- get system performance status
- diagnose sys top
- get system arp
Correct answer: D
Explanation:
"If you suspect that there is an IP address conflict, or that an IP has been assigned to the wrong device, you may need to look at the ARP table." "If you suspect that there is an IP address conflict, or that an IP has been assigned to the wrong device, you may need to look at the ARP table."
Question 5
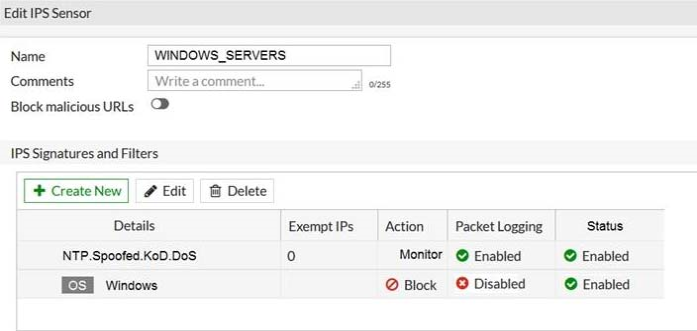
Refer to the exhibit.

The exhibit shows the IPS sensor configuration.
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
- The sensor will allow attackers matching the NTP.Spoofed.KoD.DoS signature.
- The sensor will block all attacks aimed at Windows servers.
- The sensor will reset all connections that match these signatures.
- The sensor will gather a packet log for all matched traffic.
Correct answer: AB
Question 6
Which statement is correct regarding the inspection of some of the services available by web applications embedded in third-party websites?
- The security actions applied on the web applications will also be explicitly applied on the third-party websites.
- The application signature database inspects traffic only from the original web application server.
- FortiGuard maintains only one signature of each web application that is unique.
- FortiGate can inspect sub-application traffic regardless where it was originated.
Correct answer: D
Explanation:
Reference: https://help.fortinet.com/fortiproxy/11/Content/Admin%20Guides/FPX-AdminGuide/300_System/303d_FortiGuard.htm Reference: https://help.fortinet.com/fortiproxy/11/Content/Admin%20Guides/FPX-AdminGuide/300_System/303d_FortiGuard.htm
Question 7
Which two statements are correct about SLA targets? (Choose two.)
- You can configure only two SLA targets per one Performance SLA.
- SLA targets are optional.
- SLA targets are required for SD-WAN rules with a Best Quality strategy.
- SLA targets are used only when referenced by an SD-WAN rule.
Correct answer: BD
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/382233/performance-sla-sla-targets Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/382233/performance-sla-sla-targets
Question 8
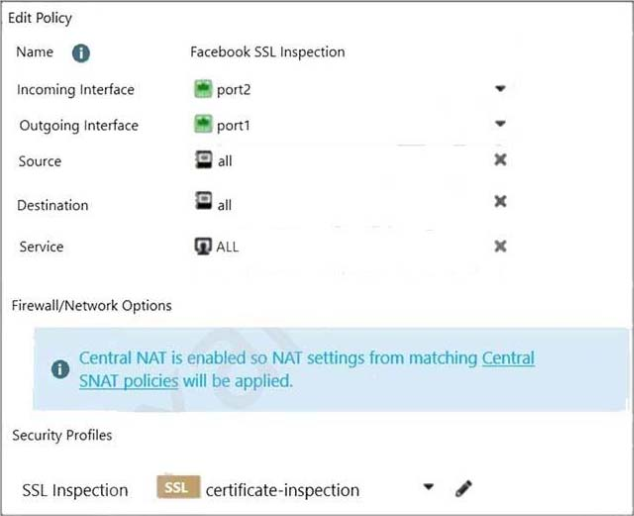
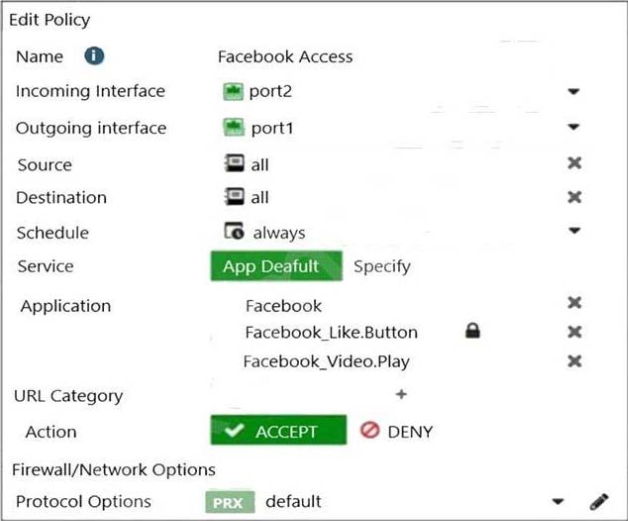
Refer to the exhibits.
Exhibit A.

Exhibit B.

The exhibits show the SSL and authentication policy (Exhibit A) and the security policy (Exhibit B) tor Facebook.
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the policy configuration must you change to resolve the issue?
- The SSL inspection needs to be a deep content inspection.
- Force access to Facebook using the HTTP service.
- Additional application signatures are required to add to the security policy.
- Add Facebook in the URL category in the security policy.
Correct answer: A
Explanation:
The lock logo behind Facebook_like.Button indicates that SSL Deep Inspection is Required. The lock logo behind Facebook_like.Button indicates that SSL Deep Inspection is Required.
Question 9
Which two attributes are required on a certificate so it can be used as a CA certificate on SSL Inspection? (Choose two.)
- The keyUsage extension must be set to keyCertSign.
- The common name on the subject field must use a wildcard name.
- The issuer must be a public CA.
- The CA extension must be set to TRUE.
Correct answer: AD
Explanation:
Reference: https://www.reddit.com/r/fortinet/comments/c7j6jg/recommended_ssl_cert/ Reference: https://www.reddit.com/r/fortinet/comments/c7j6jg/recommended_ssl_cert/
Question 10
An administrator wants to configure Dead Peer Detection (DPD) on IPSEC VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when no traffic is observed in the tunnel.
Which DPD mode on FortiGate will meet the above requirement?
- Disabled
- On Demand
- Enabled
- On Idle
Correct answer: D
Explanation:
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD40813 Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD40813

