File Info
| Exam | Fortinet NSE 4 -FortiOS 7-2 |
| Number | NSE4_FGT-7.2 |
| File Name | Fortinet.NSE4_FGT-7.2.Lead2Pass.2024-09-01.204q.vcex |
| Size | 15 MB |
| Posted | Sep 01, 2024 |
| Download | Fortinet.NSE4_FGT-7.2.Lead2Pass.2024-09-01.204q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
Which certificate value can FortiGate use to determine the relationship between the issuer and the certificate?
- Subject Key Identifiervalue
- SMMIE Capabilitiesvalue
- Subjectvalue
- Subject Alternative Namevalue
Correct answer: A
Question 2

An administrator has configured the following settings:

What are the two results of this configuration? (Choose two.)
- Device detection on all interfaces is enforced for 30 minutes.
- Denied users are blocked for 30 minutes.
- A session for denied traffic is created.
- The number of logs generated by denied traffic is reduced.
Correct answer: CD
Explanation:
By keeping the denied sessions in the session table reduces the number of session denied events in the logs not minutes. https://kb.fortinet.com/kb/documentLink.do?externalID=FD46328 By keeping the denied sessions in the session table reduces the number of session denied events in the logs not minutes.
https://kb.fortinet.com/kb/documentLink.do?externalID=FD46328
Question 3
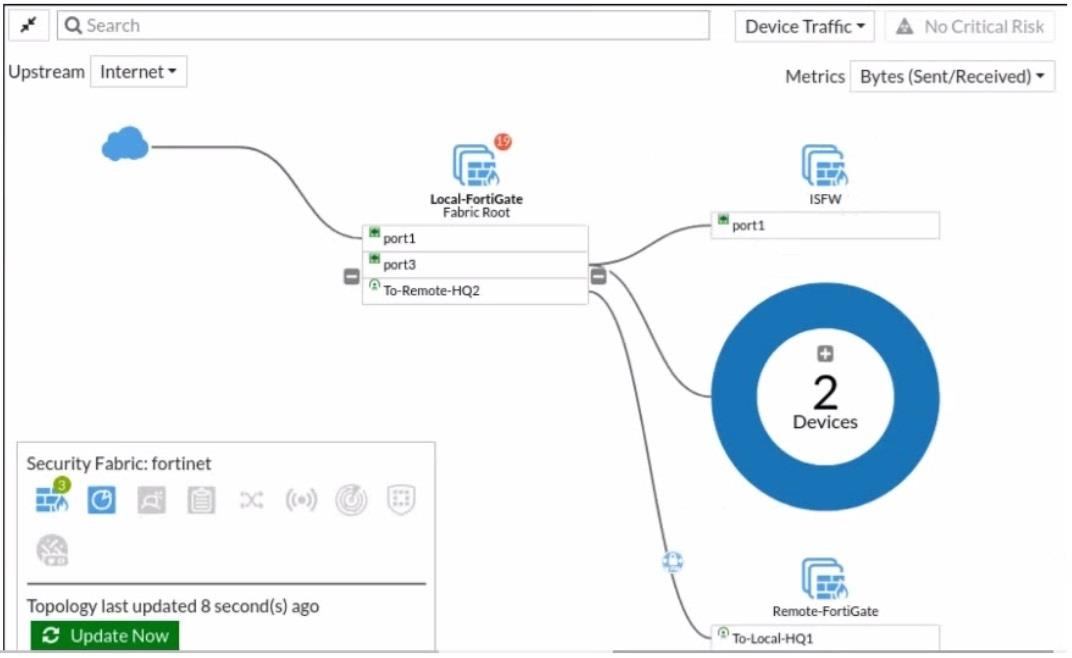
Refer to the exhibit. Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)

- This security fabric topology is a logical topology view.
- There are 19 security recommendations for the security fabric.
- There are five devices that are part of the security fabric.
- Device detection is disabled on all FortiGate devices.
Correct answer: AB
Explanation:
https://docs.fortinet.com/document/fortigate/5.6.0/cookbook/761085/results https://docs.fortinet.com/document/fortimanager/6.2.0/new-features/736125/security-fabric-topology https://docs.fortinet.com/document/fortigate/5.6.0/cookbook/761085/results
https://docs.fortinet.com/document/fortimanager/6.2.0/new-features/736125/security-fabric-topology
Question 4
Which statements best describe auto discovery VPN (ADVPN). (Choose two.)
- It requires the use of dynamic routing protocols so that spokes can learn the routes to other spokes.
- ADVPN is only supported with IKEv2.
- Tunnels are negotiated dynamically between spokes.
- Every spoke requires a static tunnel to be configured to other spokes so that phase 1 and phase 2 proposals are defined in advance.
Correct answer: AC
Question 5
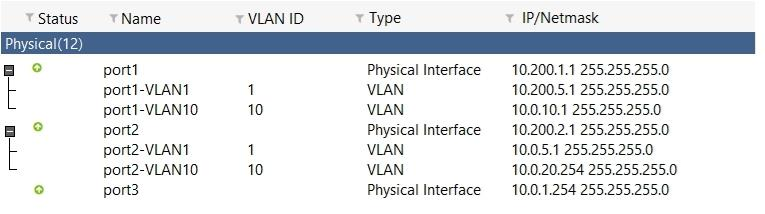
View the exhibit. Which the FortiGate handle web proxy traffic true? (Choose two.)

- Broadcast traffic received in port1-VLAN10 will not be forwarded to port2-VLAN10.
- port-VLAN1 is the native VLAN for the port1 physical interface.
- port1-VLAN10 and port2-VLAN10 can be assigned to different VDOMs.
- Traffic between port1-VLAN1 and port2-VLAN1 is allowed by default.
Correct answer: AC
Question 6
Which two inspection modes can you use to configure a firewall policy on a profile-based next-generation firewall (NGFW)? (Choose two.)
- Proxy-based inspection
- Certificate inspection
- Flow-based inspection
- Full Content inspection
Correct answer: AC
Question 7
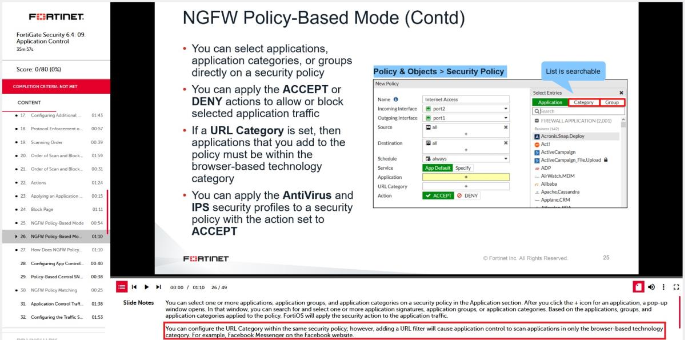
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
- It limits the scope of application control to the browser-based technology category only.
- It limits the scope of application control to scan application traffic based on application category only.
- It limits the scope of application control to scan application traffic using parent signatures only
- It limits the scope of application control to scan application traffic on DNS protocol only.
Correct answer: A
Explanation:
You can configure the URL category within the same firewall policy; however, adding a URL filter will cause application control to scan applications in only the browser-based technology category. For example, Facebook Messenger on the Facebook website. You can configure the URL category within the same firewall policy; however, adding a URL filter will cause application control to scan applications in only the browser-based technology category.
For example, Facebook Messenger on the Facebook website.

Question 8
If the Servicesfield is configured in a Virtual IP (VIP), which statement is true when central NAT is used?
- The Servicesfield prevents SNAT and DNAT from being combined in the same policy.
- The Servicesfield is used when you need to bundle several VIPs into VIP groups.
- The Servicesfield removes the requirement to create multiple VIPs for different services.
- The Servicesfield prevents multiple sources of traffic from using multiple services to connect to a single computer.
Correct answer: C
Question 9
When browsing to an internal web server using a web-mode SSL VPN bookmark, which IP address is used as the source of the HTTP request?
- remote user's public IP address
- The public IP address of the FortiGate device.
- The remote user's virtual IP address.
- The internal IP address of the FortiGate device.
Correct answer: D
Explanation:
Source IP seen by the remote resources is FortiGate's internal IP address and not the user's IP address Source IP seen by the remote resources is FortiGate's internal IP address and not the user's IP address
Question 10
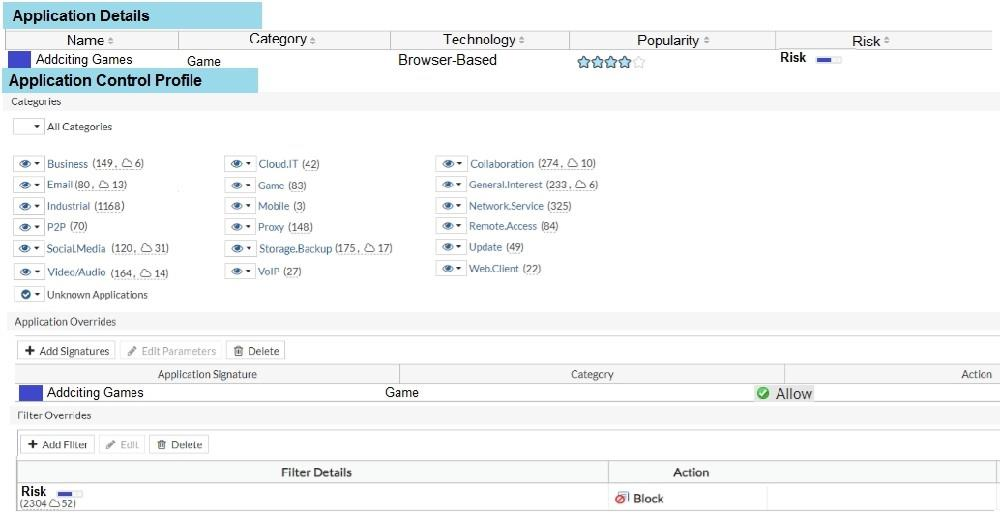
View the exhibit. A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting Games). Based on this configuration, which statement is true?

- Addicting.Games is allowed based on the Application Overrides configuration.
- Addicting.Games is blocked on the Filter Overrides configuration.
- Addicting.Games can be allowed only if the Filter Overrides actions is set to Exempt.
- Addcting.Games is allowed based on the Categories configuration.
Correct answer: A

