File Info
| Exam | NSE 6-FortiSOAR 7.3 Administrator |
| Number | NSE6_FSR-7.3 |
| File Name | Fortinet.NSE6_FSR-7.3.VCEplus.2024-10-19.15q.tqb |
| Size | 457 KB |
| Posted | Oct 19, 2024 |
| Download | Fortinet.NSE6_FSR-7.3.VCEplus.2024-10-19.15q.tqb |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
Which two statements about upgrading a FortiSOAR HA cluster are true7 (Choose two.)
- Nodes can be upgraded while the primary node or secondary node are in the HA cluster.
- Upgrading a FortiSOAR HA cluster requires no downtime.
- The upgrade procedure for an active-active cluster and an active-passive cluster are the same.
- It is recommended that the passive secondary node be upgraded first, and then the active primary node.
Correct answer: CD
Explanation:
Upgrading a FortiSOAR HA cluster follows the same procedure regardless of whether it is configured in an active-active or active-passive setup. The process generally involves upgrading one node at a time to minimize service disruption. Best practices recommend upgrading the passive secondary node first before moving to the active primary node. This sequence helps maintain cluster stability and ensures that at least one node remains operational during the upgrade. Upgrading a FortiSOAR HA cluster follows the same procedure regardless of whether it is configured in an active-active or active-passive setup. The process generally involves upgrading one node at a time to minimize service disruption. Best practices recommend upgrading the passive secondary node first before moving to the active primary node. This sequence helps maintain cluster stability and ensures that at least one node remains operational during the upgrade.
Question 2
Which SMS vendor does FortiSOAR support for two-factor authentication?
- Twilio
- Google Authenticator
- 2factor
- Telesign
Correct answer: D
Explanation:
For two-factor authentication (2FA) via SMS, FortiSOAR supports integration with Telesign. This vendor provides SMS-based 2FA services, enabling FortiSOAR to leverage Telesign's API for sending verification codes as part of its security features. Telesign's service is compatible with FortiSOAR, ensuring secure user authentication when accessing the platform or certain features. For two-factor authentication (2FA) via SMS, FortiSOAR supports integration with Telesign. This vendor provides SMS-based 2FA services, enabling FortiSOAR to leverage Telesign's API for sending verification codes as part of its security features. Telesign's service is compatible with FortiSOAR, ensuring secure user authentication when accessing the platform or certain features.
Question 3
Which three actions can be performed from within the war room? (Choose three)
- View graphical representation of all records linked to an incident in the Artifacts lab
- Change the room's status to Escalated to enforce hourly updates.
- Investigate issues by tagging results as evidence.
- Use the Task Manager tab to create, manage, assign, and track tasks.
- Integrate a third-party instant messenger directly into the collaboration workspace.
Correct answer: ACD
Explanation:
In FortiSOAR's War Room, users can perform several actions to manage incidents effectively. They can view a graphical representation of records linked to an incident in the Artifacts lab, which helps visualize connections and dependencies. Additionally, the War Room supports tagging investigation results as evidence, allowing for a structured approach to incident documentation. Users can also manage tasks via the Task Manager tab, facilitating task creation, assignment, and tracking within the incident response workflow. In FortiSOAR's War Room, users can perform several actions to manage incidents effectively. They can view a graphical representation of records linked to an incident in the Artifacts lab, which helps visualize connections and dependencies. Additionally, the War Room supports tagging investigation results as evidence, allowing for a structured approach to incident documentation. Users can also manage tasks via the Task Manager tab, facilitating task creation, assignment, and tracking within the incident response workflow.
Question 4
Several users have informed you that the FortiSOAR GUI Is not reachable. When troubleshooting, which step should you take first?
- Enter the csadm license --show-details command to check if there is a duplicate license.
- Enter the csadm services --restart ngiax command to restart only the Nginx process.
- Enter the systemct1 status nginx command to gather more information.
- Review the connecters.log file to see what is happening to the HTTPS connections.
Correct answer: C
Explanation:
When troubleshooting the issue of the FortiSOAR GUI not being reachable, the first step should be to check the status of the nginx service, which is responsible for managing web requests. Using the command systemctl status nginx will provide information on whether the service is running and any potential issues or errors related to it. This approach is more efficient as it directly addresses the service responsible for the web interface, making it possible to diagnose and resolve common issues such as service failure, configuration errors, or connectivity problems. When troubleshooting the issue of the FortiSOAR GUI not being reachable, the first step should be to check the status of the nginx service, which is responsible for managing web requests. Using the command systemctl status nginx will provide information on whether the service is running and any potential issues or errors related to it. This approach is more efficient as it directly addresses the service responsible for the web interface, making it possible to diagnose and resolve common issues such as service failure, configuration errors, or connectivity problems.
Question 5
Which log file contains license synchronization logs on FortiSOAR?
- fdn.log
- beat.log
- celery.log
- falcon.log
Correct answer: A
Explanation:
The fdn.log file in FortiSOAR contains logs related to license synchronization activities. This log file records events and errors associated with license checks and synchronization with Fortinet's licensing servers, ensuring that the FortiSOAR instance remains compliant with licensing requirements. Monitoring fdn.log can help administrators troubleshoot issues related to license synchronization and ensure the system operates within the licensed limits. The fdn.log file in FortiSOAR contains logs related to license synchronization activities. This log file records events and errors associated with license checks and synchronization with Fortinet's licensing servers, ensuring that the FortiSOAR instance remains compliant with licensing requirements. Monitoring fdn.log can help administrators troubleshoot issues related to license synchronization and ensure the system operates within the licensed limits.
Question 6
Which playbook collection includes system-level playbooks that FortiSOAR uses to auto-populate date fields when the status of incident or alert records changes to Resolved or Closed?
- SLA Management Playbooks
- Utilities Playbooks
- Schedule Management Playbooks
- Approval/Manual Task Playbooks
Correct answer: A
Explanation:
The SLA Management Playbooks collection in FortiSOAR includes system-level playbooks designed to auto-populate date fields when the status of incident or alert records changes to Resolved or Closed. This functionality ensures that relevant date fields, such as resolution date or closure date, are accurately filled based on SLA criteria. By using SLA Management Playbooks, FortiSOAR automatically maintains date-related data integrity, which is essential for tracking and reporting purposes. The SLA Management Playbooks collection in FortiSOAR includes system-level playbooks designed to auto-populate date fields when the status of incident or alert records changes to Resolved or Closed. This functionality ensures that relevant date fields, such as resolution date or closure date, are accurately filled based on SLA criteria. By using SLA Management Playbooks, FortiSOAR automatically maintains date-related data integrity, which is essential for tracking and reporting purposes.
Question 7
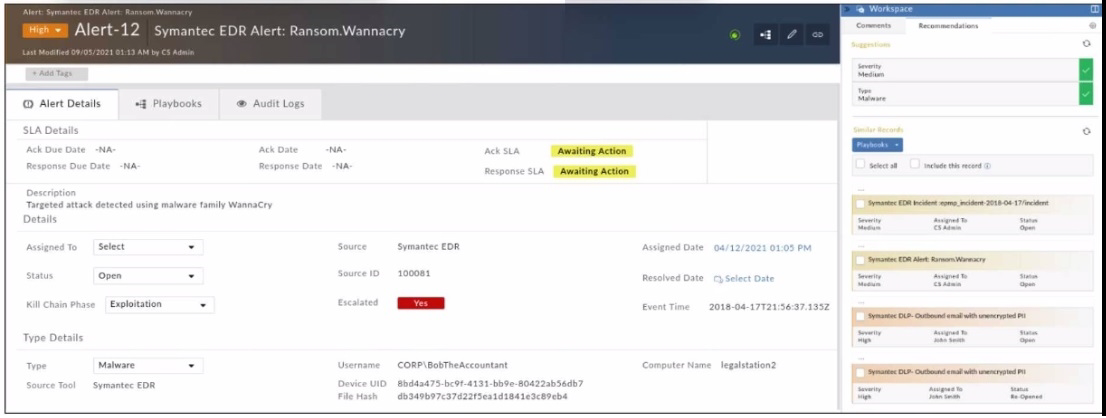
Refer to the exhibit.

Which two statements about the recommendation engine are true? (Choose two.)
- There are no playbooks that can be run on the recommended alerts using the recommendation panel
- The dataset is trained to predict the Severity and Type fields.
- The recommendation engine is set to automatically accept suggestions.
- The alert severity is High, but the recommendation is for it to be set to Medium
Correct answer: BD
Explanation:
The Recommendation Engine in FortiSOAR is designed to assist in alert triage by suggesting values for certain fields based on historical data and machine learning models. In this case, the engine is trained to predict both the Severity and Type fields, suggesting values that align with past incidents and threat intelligence. Although the current alert severity is High, the recommendation engine has suggested adjusting it to Medium based on the pattern of similar past alerts, indicating a less critical threat level than initially perceived. This functionality helps analysts by providing data-driven insights, which can optimize alert handling and resource allocation. The Recommendation Engine in FortiSOAR is designed to assist in alert triage by suggesting values for certain fields based on historical data and machine learning models. In this case, the engine is trained to predict both the Severity and Type fields, suggesting values that align with past incidents and threat intelligence. Although the current alert severity is High, the recommendation engine has suggested adjusting it to Medium based on the pattern of similar past alerts, indicating a less critical threat level than initially perceived. This functionality helps analysts by providing data-driven insights, which can optimize alert handling and resource allocation.
Question 8
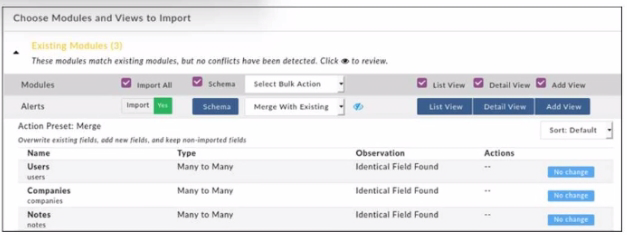
Refer to the exhibit.

When importing modules to FortiSOAR using the configuration wizard, what actions are applied to fields it you select Merge with Existing as the Bulk action?
- Existing fields are kept, new fields are added, and non-imported fields are deleted.
- Existing Holds are overwritten, now fields are added, and non-imported fields are deleted.
- Existing fields are kept, new fields are added, and non-imported fields are kept.
- Existing fields are overwritten, new fields are added, and non-Imported fields are kept.
Correct answer: D
Explanation:
When importing modules into FortiSOAR using the configuration wizard and selecting 'Merge with Existing' as the bulk action, the behavior for field handling is as follows: any fields that already exist in the system are overwritten with the imported values. New fields from the imported module are added to the system, while fields that are not part of the imported module remain unaffected and are retained in the system. This option ensures that existing data structures are updated with new information without losing existing, but non-imported, fields. When importing modules into FortiSOAR using the configuration wizard and selecting 'Merge with Existing' as the bulk action, the behavior for field handling is as follows: any fields that already exist in the system are overwritten with the imported values. New fields from the imported module are added to the system, while fields that are not part of the imported module remain unaffected and are retained in the system. This option ensures that existing data structures are updated with new information without losing existing, but non-imported, fields.
Question 9
Which service on FortiSOAR is the playbook scheduler?
- cyops-torccat
- colcrybeatd
- celeryd
- uwsgi
Correct answer: B
Explanation:
In FortiSOAR, the service responsible for the playbook scheduling functionality is colcrybeatd. This service manages the timing and execution of scheduled playbooks, allowing for the automation of various tasks at specified intervals. It ensures that playbooks execute according to their configured schedules, which can include tasks such as data ingestion, threat detection, or incident response actions. Proper functioning of this service is essential for the reliable automation of time-dependent processes within FortiSOAR. In FortiSOAR, the service responsible for the playbook scheduling functionality is colcrybeatd. This service manages the timing and execution of scheduled playbooks, allowing for the automation of various tasks at specified intervals. It ensures that playbooks execute according to their configured schedules, which can include tasks such as data ingestion, threat detection, or incident response actions. Proper functioning of this service is essential for the reliable automation of time-dependent processes within FortiSOAR.
Question 10
A security analyst has reported unauthorized access to System Configuration. You must review the user's current level of access, and then restrict their access according to your organization's requirements. As part of your auditing process, which two actions should you perform? (Choose two.)
- Remove the create, read, update, and delete (CRUD) permissions or roles that the user does not require.
- View the user's effective role permissions, and then investigate which role is providing that access.
- Remove all record ownership that is assigned to the user.
- Review the user's learn hierarchy to ensure that the appropriate relationships are configured.
Correct answer: BD
Explanation:
To audit and restrict a user's access within FortiSOAR, particularly in response to unauthorized access reports, it's necessary to review the user's effective role permissions. This involves checking which roles grant the user access to the System Configuration module and adjusting as needed. Additionally, reviewing the user's team hierarchy ensures that the user's access aligns with the organization's policies. Misconfigurations in team relationships can sometimes inadvertently provide elevated access; hence, confirming that the team setup is correct is a critical part of the auditing process. To audit and restrict a user's access within FortiSOAR, particularly in response to unauthorized access reports, it's necessary to review the user's effective role permissions. This involves checking which roles grant the user access to the System Configuration module and adjusting as needed. Additionally, reviewing the user's team hierarchy ensures that the user's access aligns with the organization's policies. Misconfigurations in team relationships can sometimes inadvertently provide elevated access; hence, confirming that the team setup is correct is a critical part of the auditing process.

