File Info
| Exam | Fortinet NSE 7 - Advanced Threat Protection 2.5 |
| Number | NSE7_ATP-2.5 |
| File Name | Fortinet.NSE7_ATP-2.5.CertKey.2019-12-04.18q.vcex |
| Size | 1 MB |
| Posted | Dec 04, 2019 |
| Download | Fortinet.NSE7_ATP-2.5.CertKey.2019-12-04.18q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
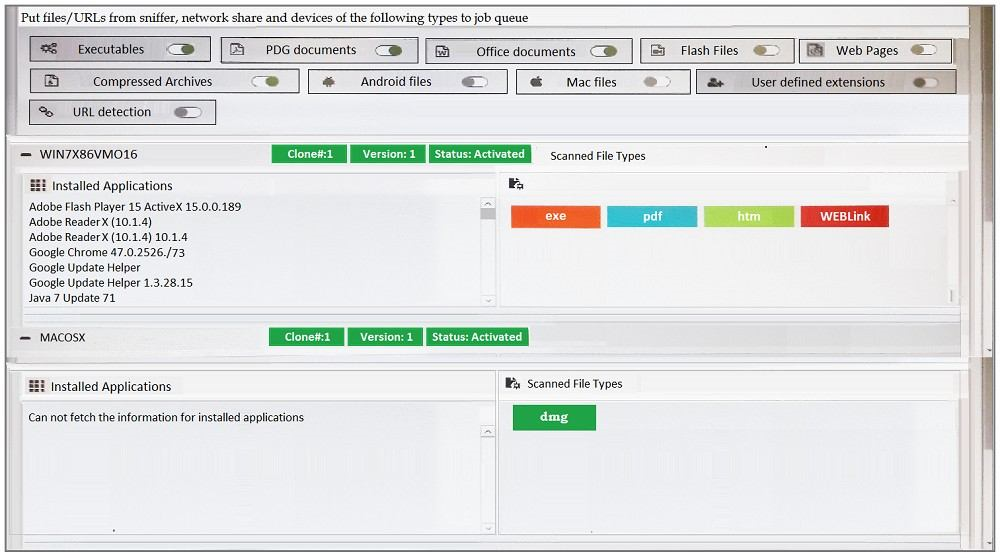
Examine the FortiSandbox Scan Profile configuration shown in the exhibit, and then answer the following question:

Based on the configuration, which of the following statements are true? (Choose two.)
- PDF files will be inspected in the WIN7X86VM)16 VM.
- URLs submitted using JSON API will not be inspected.
- HTM files submitted using the management GUI will be inspected.
- DMG files will be inspected in the MACOSX VM.
Correct answer: CD
Question 2
Which samples can FortiClient submit to FortiSandbox for analysis? (Choose two.)
- Downloads from emails
- URLs from web requests
- Command and control traffic
- Files from removable storage
Correct answer: AC
Question 3
At which stage of the kill chain will an attacker use tools, such as nmap, ARIN, and banner grabbing, on the targeted organization’s network?
- Exploitation
- Reconnaissance
- Lateral movement
- Weaponization
Correct answer: B
Question 4
When using FortiSandbox in sniffer-mode, you should configure FortiSandbox to inspect both inbound and outbound traffic.
What type of threats can FortiSandbox detect on inbound traffic? (Choose two.)
- Botnet connections
- Malware
- Malicious URLs
- Intrusion attempts
Correct answer: AD
Question 5
Which of the advanced threat protection solutions should you use to protect against an attacker may take during the lateral movement stage of the kill chain? (Choose two.)
- FortiClient and FortiSandbox
- FortiMail and FortiSandbox
- FortiGate and FortiSandbox
- FortiWeb and FortiSandbox
Correct answer: BD
Question 6
Which advanced threat protection integration solution should you use to protect against out-of-band attack vectors, such as USB drives, used during the delivery stage of the kill chain?
- FortiGate and FortiSandbox
- FortiMail and FortiSandbox
- FortiWeb and FortiSandbox
- FortiClient and FortiSandbox
Correct answer: B
Explanation:
Reference: https://www.infosecpartners.com/fortimail-fortisandbox-perfect-partners/ Reference: https://www.infosecpartners.com/fortimail-fortisandbox-perfect-partners/
Question 7
Which of the following advanced threat protection are capable of preventing patient-zero infections? (Choose two.)
- FortiWeb and FortiSandbox
- FortiClient and FortiSandbox
- FortiMail and FortiSandbox
- FortiGate and FortiSandbox
Correct answer: AD
Explanation:
FortiGate Enterprise Firewall Platform provides the industry’s highest- performing firewall capabilities, and Fortinet’s FortiGuard Security Subscription Services provide the industry’s highest level of threat research, intelligence, and analytics. Reference: https://www.fortinet.com/content/dam/fortinet/assets/alliances/2019/sb-fortinet-alliances-ziften.pdf FortiGate Enterprise Firewall Platform provides the industry’s highest- performing firewall capabilities, and Fortinet’s FortiGuard Security Subscription Services provide the industry’s highest level of threat research, intelligence, and analytics.
Reference: https://www.fortinet.com/content/dam/fortinet/assets/alliances/2019/sb-fortinet-alliances-ziften.pdf
Question 8
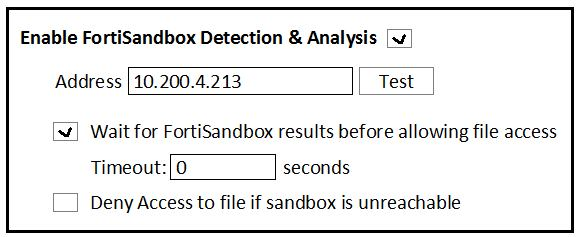
Examine the FortiClient configuration shown in the exhibit. then answer the following question:

What is the general rule you should follow when configuring the Timeout value for files submitted to FortiSandbox?
- It should be long enough for FortiSandbox to complete an antivirus scan of files.
- It should be long enough for FortiSandbox to complete a cloud query of file hashes.
- It should be long enough for FortiSandbox to complete sandbox analysis of files.
- It should be long enough for FortiSandbox to complete a static analysis of files.
Correct answer: C
Explanation:
Reference https://help.fortinet.com/fclient/olh/5-6-6/FortiClient-5.6-Admin/800_Sandbox%20Detection/0605_Config%20submission%20and%20remediation.htm Reference https://help.fortinet.com/fclient/olh/5-6-6/FortiClient-5.6-Admin/800_Sandbox%20Detection/0605_Config%20submission%20and%20remediation.htm
Question 9
Which FortiSandbox interfaces can you use for sniffer mode? (Choose two.)
- port2
- port3
- port1
- port4
Correct answer: BC
Explanation:
FortiSandbox reserves port1 for device management and port3 for scanned files to access the Internet. Port1, port3 Reference: https://help.fortinet.com/fsandbox/olh/2-5-1/Document/900_Scan%20Input/500_Sniffer/100_Sniffer.htm FortiSandbox reserves port1 for device management and port3 for scanned files to access the Internet. Port1, port3
Reference: https://help.fortinet.com/fsandbox/olh/2-5-1/Document/900_Scan%20Input/500_Sniffer/100_Sniffer.htm
Question 10
Which threats can FortiSandbox inspect when it is deployed in sniffer mode? (Choose three.)
- Spam emails
- Known malware
- Encrypted files
- Malicious URLs
- Botnet connections
Correct answer: BDE

