File Info
| Exam | Fortinet NSE 7 - Advanced Threat Protection 2.5 |
| Number | NSE7_ATP-2.5 |
| File Name | Fortinet.NSE7_ATP-2.5.VCEplus.2019-12-05.30q.vcex |
| Size | 2 MB |
| Posted | Dec 05, 2019 |
| Download | Fortinet.NSE7_ATP-2.5.VCEplus.2019-12-05.30q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
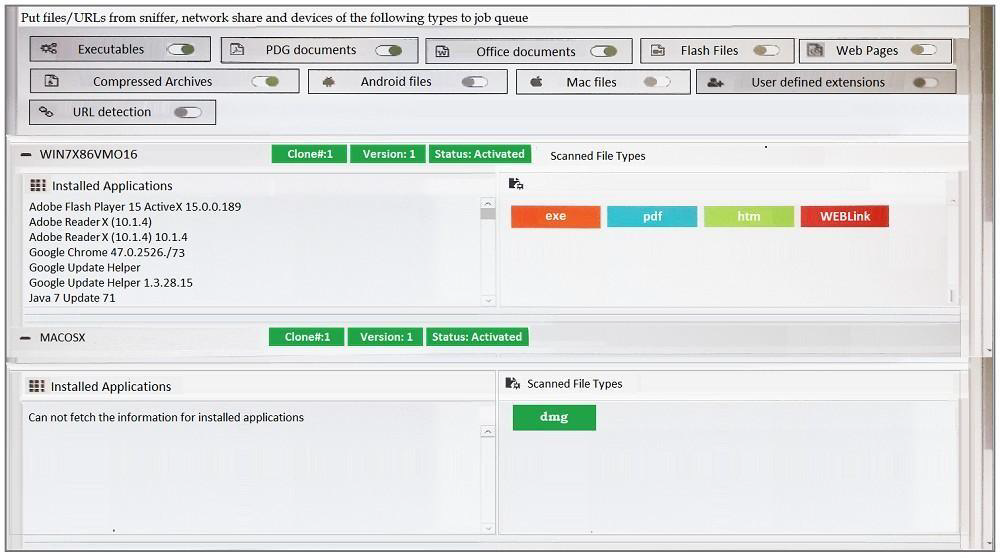
Examine the FortiSandbox Scan Profile configuration shown in the exhibit, and then answer the following question:

Based on the configuration, which of the following statements are true? (Choose two.)
- PDF files will be inspected in the WIN7X86VM)16 VM.
- URLs submitted using JSON API will not be inspected.
- HTM files submitted using the management GUI will be inspected.
- DMG files will be inspected in the MACOSX VM.
Correct answer: CD
Question 2
Which samples can FortiClient submit to FortiSandbox for analysis? (Choose two.)
- Downloads from emails
- URLs from web requests
- Command and control traffic
- Files from removable storage
Correct answer: AC
Question 3
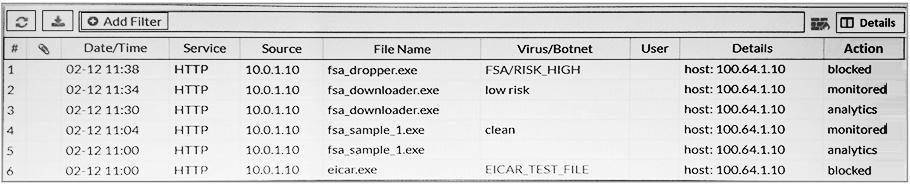
Examine the FortiGate antivirus logs shown in the exhibit, than answer the following question:

Based on the logs shown, which of the following statements is correct? (Choose two.)
- The fsa_dropper.exe file was blocked using a local black list entry.
- The fsa_sample_1.exe file was not sent to FortiSandbox.
- The eicar.exe file was blocked using a FortiGiard generated signature.
- The fsa_downloader.exe file was not blocked by FortiGate.
Correct answer: BD
Explanation:
File Filter allows the Web Filter profile to block files passing through a FortiGate based on file type. Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/610893/file-filter File Filter allows the Web Filter profile to block files passing through a FortiGate based on file type. Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/610893/file-filter
Question 4
At which stage of the kill chain will an attacker use tools, such as nmap, ARIN, and banner grabbing, on the targeted organization's network?
- Exploitation
- Reconnaissance
- Lateral movement
- Weaponization
Correct answer: B
Question 5
FortiGate root VDOM is authorized and configured to send suspicious files to FortiSandbox for inspection. The administrator creates a new VDOM, and then generates some traffic so that the new VDOM sends a file to FortiSandbox for the first time.
Which of the following is true regarding this scenario?
- FortiSandbox will accept the file, but not inspect it until the administrator manually configures the new VDOM on FortiSandbox.
- FortiSandbox will inspect all files based on the root VDOM authorization state and configuration.
- FortiSandbox will accept the file, but not inspect it until the administrator manually authorizes the new VDOM on FortiSandbox.
- By default, FortiSandbox will autoauthorize the new VDOM, and inspect files as they are received.
Correct answer: B
Question 6
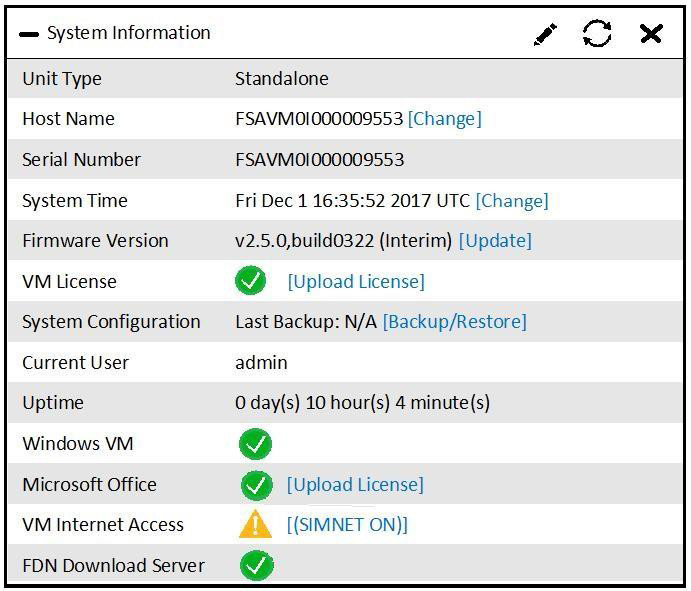
Examine the System Information widget shown in the exhibit, then answer the following question:

Which of the following inspections will FortiSandbox perform on samples submitted for sandboxing? (Choose two.)
- URL rating on FQDN seen in DNS requests
- IP reputation check on callback connections
- Antivirus inspection on downloaded files
- URL rating on HTTP GET requests
Correct answer: CD
Question 7
Which of the kill chain stages does Fortinet's advanced threat protection solution block? (Choose three.)
- Command and control
- Delivery
- Reconnaissance
- Lateral movement
- Weaponization
Correct answer: ACD
Question 8
Which of the following are features of network share scanning of FortiSandbox? (Choose two.)
- Move clean files to a separate network share.
- Replace suspicious files with a replacement message.
- Detect malicious URLs.
- Detect network attacks.
Correct answer: AB
Explanation:
Reference: https://help.fortinet.com/fsandbox/olh/2-5-1/Document/900_Scan%20Input/900_Network%20Share/100_Network%20Share.htm Reference: https://help.fortinet.com/fsandbox/olh/2-5-1/Document/900_Scan%20Input/900_Network%20Share/100_Network%20Share.htm
Question 9
When using FortiSandbox in sniffer-mode, you should configure FortiSandbox to inspect both inbound and outbound traffic.
What type of threats can FortiSandbox detect on inbound traffic? (Choose two.)
- Botnet connections
- Malware
- Malicious URLs
- Intrusion attempts
Correct answer: AD
Question 10
Which of the advanced threat protection solutions should you use to protect against an attacker may take during the lateral movement stage of the kill chain? (Choose two.)
- FortiClient and FortiSandbox
- FortiMail and FortiSandbox
- FortiGate and FortiSandbox
- FortiWeb and FortiSandbox
Correct answer: BD

