File Info
| Exam | Fortinet NSE 7 - Network Security 7.2 Support Engineer |
| Number | NSE7_NST-7.2 |
| File Name | Fortinet.NSE7_NST-7.2.VCEplus.2024-06-25.23q.vcex |
| Size | 1 MB |
| Posted | Jun 25, 2024 |
| Downloads: | 1 |
| Download | Fortinet.NSE7_NST-7.2.VCEplus.2024-06-25.23q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
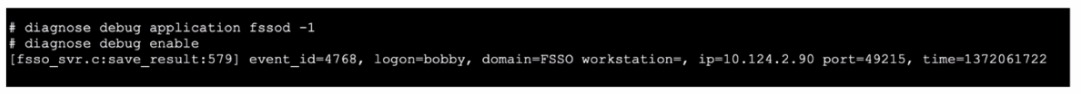
Refer to the exhibit.

Refer to the exhibit, which shows a partial output of the fssod daemon real-time debug command
What two conclusions can you draw from the output? (Choose two.)
- FSSO is using agentless polling mode to detect logon events.
- The workstation with IP 10.124.2.90 will be polled frequently using TCP port 445 to see if the user is still logged on
- The logon event can be seen on the collector agent installed on Windows.
- FSSO is using DC agent mode to detect logon events.
Correct answer: CD
Explanation:
Logon Event on Collector Agent: The debug output indicates that the logon event is recorded, showing that the collector agent on Windows is logging user activities and transmitting this data to the FortiGate.DC Agent Mode: The presence of detailed logon events and their corresponding metadata, such as the domain and workstation information, suggests that the FortiGate is using DC agent mode. This mode involves an agent installed on the Domain Controller (DC) to capture and forward logon events.Fortinet Community: How FSSO Works and Troubleshooting Steps (Welcome to the Fortinet Community!) (Fortinet GURU). Logon Event on Collector Agent: The debug output indicates that the logon event is recorded, showing that the collector agent on Windows is logging user activities and transmitting this data to the FortiGate.
DC Agent Mode: The presence of detailed logon events and their corresponding metadata, such as the domain and workstation information, suggests that the FortiGate is using DC agent mode. This mode involves an agent installed on the Domain Controller (DC) to capture and forward logon events.
Fortinet Community: How FSSO Works and Troubleshooting Steps (Welcome to the Fortinet Community!) (Fortinet GURU).
Question 2
What is the diagnose test application ipsmonitor 5 command used for?
- To disable the IPS engine
- To provide information regarding IPS sessions
- To restart all IPS engines and monitors
- To enable IPS bypass mode
Correct answer: C
Explanation:
The command diagnose test application ipsmonitor 5 is used to restart all IPS (Intrusion Prevention System) engines and monitors on the FortiGate device. This command is part of the diagnostic tools available for troubleshooting and maintaining the IPS functionality on the FortiGate.Running this command forces the IPS system to reset and reinitialize, which can be useful in situations where the IPS functionality appears to be malfunctioning or not responding correctly.This action helps in clearing any issues that might have arisen due to internal errors or misconfigurations, ensuring that the IPS engines operate correctly after the restart. The command diagnose test application ipsmonitor 5 is used to restart all IPS (Intrusion Prevention System) engines and monitors on the FortiGate device. This command is part of the diagnostic tools available for troubleshooting and maintaining the IPS functionality on the FortiGate.
Running this command forces the IPS system to reset and reinitialize, which can be useful in situations where the IPS functionality appears to be malfunctioning or not responding correctly.
This action helps in clearing any issues that might have arisen due to internal errors or misconfigurations, ensuring that the IPS engines operate correctly after the restart.
Question 3
There are four exchanges during IKEv2 negotiation.
Which sequence is correct?
- IKE_Proposal, ID_Auth, PiggyBack_CHILD and Informational
- lnit_Req, Wait_lnit_Req, ID_Auth_Req and Create_CHILD_SA
- INIT_Re, INIT_Auth, ID_Child and SET_Nonce
- IKE_SAJNIT, IKE_Auth, Create_CHILD_SA and Informational
Correct answer: D
Explanation:
IKE_SA_INIT:This is the first exchange in IKEv2. It establishes a secure, authenticated channel between peers and negotiates cryptographic algorithms and keys.IKE_Auth:The second exchange authenticates the IKE SA (Security Association) using the previously negotiated keys and algorithms. This exchange also establishes the first IPsec SA.Create_CHILD_SA:This exchange creates additional IPsec SAs after the initial authentication. It can also be used to rekey existing IPsec SAs to maintain security.Informational:This is a generic exchange used for various purposes such as error notification, deletion of SAs, and other control messages.Fortinet Community: IKEv2 packet exchanges and troubleshootingFortinet Documentation: IPsec VPN Concepts IKE_SA_INIT:
This is the first exchange in IKEv2. It establishes a secure, authenticated channel between peers and negotiates cryptographic algorithms and keys.
IKE_Auth:
The second exchange authenticates the IKE SA (Security Association) using the previously negotiated keys and algorithms. This exchange also establishes the first IPsec SA.
Create_CHILD_SA:
This exchange creates additional IPsec SAs after the initial authentication. It can also be used to rekey existing IPsec SAs to maintain security.
Informational:
This is a generic exchange used for various purposes such as error notification, deletion of SAs, and other control messages.
Fortinet Community: IKEv2 packet exchanges and troubleshooting
Fortinet Documentation: IPsec VPN Concepts
Question 4
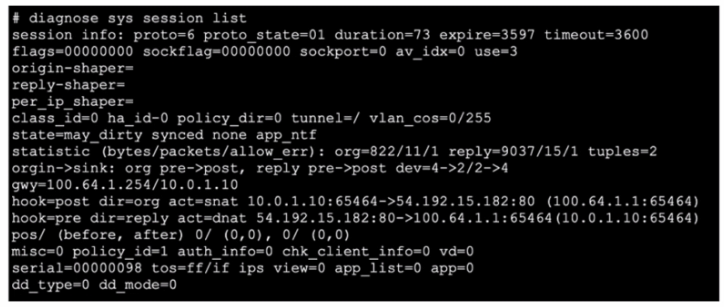
Exhibit.

Refer to the exhibit, which shows the output of diagnose sys session list.
If the HA ID for the primary device is 0. what happens if the primary fails and the secondary becomes the primary?
- The session will be removed from the session table of the secondary device because of the presence of allowed error packets, which will force the client to restart the session with the server.
- The session state is preserved but the kernel will need to re-evaluate the session because NAT was applied.
- Traffic for this session continues to be permitted on the new primary device after failover. without requiring the client to restart the session with the server.
- The secondary device has this session synchronized; however, because application control is applied, the session is marked dirty and has to be re-evaluated after failover.
Correct answer: C
Explanation:
Session Synchronization:FortiGate HA (High Availability) ensures that active sessions are synchronized between the primary and secondary devices. This synchronization allows for seamless failover and continuity of sessions.Handling NAT Sessions:The session in the exhibit has NAT applied, as indicated by the hook=post dir=org act=snat entry. FortiGate's HA setup is designed to handle such sessions, ensuring that traffic continues without interruption during failover.Session Preservation:Even with the presence of NAT, the session state is preserved across the HA devices. This means that ongoing sessions do not require re-establishment by the client, thus providing a seamless experience.Fortinet Documentation: HA session synchronization and failoverFortinet Community: Understanding session synchronization in FortiGate HA Session Synchronization:
FortiGate HA (High Availability) ensures that active sessions are synchronized between the primary and secondary devices. This synchronization allows for seamless failover and continuity of sessions.
Handling NAT Sessions:
The session in the exhibit has NAT applied, as indicated by the hook=post dir=org act=snat entry. FortiGate's HA setup is designed to handle such sessions, ensuring that traffic continues without interruption during failover.
Session Preservation:
Even with the presence of NAT, the session state is preserved across the HA devices. This means that ongoing sessions do not require re-establishment by the client, thus providing a seamless experience.
Fortinet Documentation: HA session synchronization and failover
Fortinet Community: Understanding session synchronization in FortiGate HA
Question 5
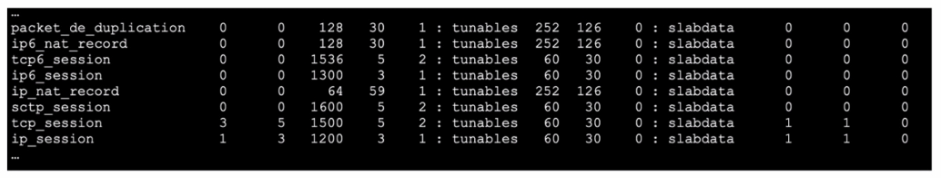
Refer to the exhibit, which shows the omitted output of FortiOS kernel slabs.

Which statement is true?
- The total slab size of the tcp_sessior. slab Is 7500 kB and is associated with the kernel.
- The total slab size of the ip6_session slab is 1300 kB and is associated with the kernel.
- The total slab size of the sctp_session slab is 0 kB and is associated with the user space
- The total slab size of the ip_session slab is 3600 kB and is associated with the user space.
Correct answer: B
Explanation:
Kernel Slabs Overview:The slab allocator in the Linux kernel is used for efficient memory management. It groups objects of the same type into caches, which are divided into slabs.Each slab contains multiple objects and helps to minimize fragmentation and enhance memory allocation efficiency.Interpreting the Exhibit:The exhibit shows output related to various kernel slab caches.The line for ip6_session indicates that there are 1300 kB allocated for this slab, which means the total memory size allocated for IPv6 session objects in the kernel is 1300 kB.Fortinet Community: Explanation of kernel slab allocation and usage (Welcome to the Fortinet Community!) (Hammertux).Linux Kernel Documentation: Slab Allocator details (Hammertux). Kernel Slabs Overview:
The slab allocator in the Linux kernel is used for efficient memory management. It groups objects of the same type into caches, which are divided into slabs.
Each slab contains multiple objects and helps to minimize fragmentation and enhance memory allocation efficiency.
Interpreting the Exhibit:
The exhibit shows output related to various kernel slab caches.
The line for ip6_session indicates that there are 1300 kB allocated for this slab, which means the total memory size allocated for IPv6 session objects in the kernel is 1300 kB.
Fortinet Community: Explanation of kernel slab allocation and usage (Welcome to the Fortinet Community!) (Hammertux).
Linux Kernel Documentation: Slab Allocator details (Hammertux).
Question 6
Consider the scenario where the server name indication (SNI) does not match either the common name (CN) or any of the subject alternative names (SAN) in the server certificate. Which action will FortiGate take when using
the default settings for SSL certificate inspection?
- FortiGate closes the connection because this represents an invalid SSL/TLS configuration
- FortiGate uses the 31 information from the Subject field in the server certificate.
- FortiGate uses the first entry listed in the SAN field in the server certificate.
- FortiGate uses the SNI from the user's web browser.
Correct answer: A
Explanation:
SNI and Certificate Mismatch: When the Server Name Indication (SNI) does not match either the Common Name (CN) or any of the Subject Alternative Names (SAN) in the server certificate, FortiGate's default behavior is to consider this as an invalid SSL/TLS configuration.Default Action: FortiGate, under default settings for SSL certificate inspection, will close the connection to prevent potential security risks associated with mismatched certificates.Fortinet Community: SSL Certificate Inspection Configuration and Behavior (Welcome to the Fortinet Community!). SNI and Certificate Mismatch: When the Server Name Indication (SNI) does not match either the Common Name (CN) or any of the Subject Alternative Names (SAN) in the server certificate, FortiGate's default behavior is to consider this as an invalid SSL/TLS configuration.
Default Action: FortiGate, under default settings for SSL certificate inspection, will close the connection to prevent potential security risks associated with mismatched certificates.
Fortinet Community: SSL Certificate Inspection Configuration and Behavior (Welcome to the Fortinet Community!).
Question 7
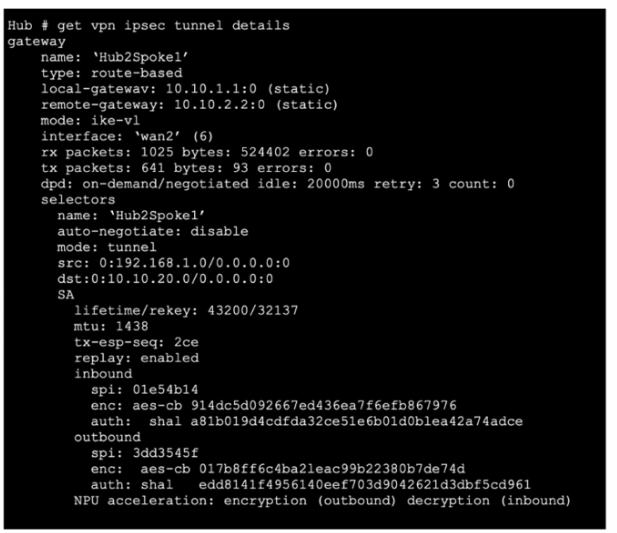
Exhibit.

Refer to the exhibit, which contains the partial output of the get vpn ipsec tunnel details command. Based on the output, which two statements are correct? (Choose two.)
- Anti-replay is enabled.
- The npu_flag for this tunnel is 03.
- The npu_flag for this tunnel is 02
- Different SPI values are a result of auto-negotiation being disabled for phase 2 selectors.
Correct answer: AC
Explanation:
Anti-replay Enabled:The exhibit shows replay: enabled, which confirms that anti-replay is enabled for this IPsec tunnel. Anti-replay is a security feature that prevents replay attacks by ensuring that packets are not duplicated or reused.NPU Acceleration:The NPU acceleration: encryption (outbound) decryption (inbound) line indicates that Network Processing Unit (NPU) acceleration is used.The npu_flag for this tunnel is 02. This indicates that encryption and decryption are handled by the NPU, improving the performance of the VPN tunnel.Fortinet Community: Troubleshooting IPsec VPN Tunnels (Welcome to the Fortinet Community!) (Welcome to the Fortinet Community!).Fortinet Documentation: Verifying IPsec VPN Tunnels (Fortinet Docs) (Fortinet Docs). Anti-replay Enabled:
The exhibit shows replay: enabled, which confirms that anti-replay is enabled for this IPsec tunnel. Anti-replay is a security feature that prevents replay attacks by ensuring that packets are not duplicated or reused.
NPU Acceleration:
The NPU acceleration: encryption (outbound) decryption (inbound) line indicates that Network Processing Unit (NPU) acceleration is used.
The npu_flag for this tunnel is 02. This indicates that encryption and decryption are handled by the NPU, improving the performance of the VPN tunnel.
Fortinet Community: Troubleshooting IPsec VPN Tunnels (Welcome to the Fortinet Community!) (Welcome to the Fortinet Community!).
Fortinet Documentation: Verifying IPsec VPN Tunnels (Fortinet Docs) (Fortinet Docs).
Question 8
Which two statements about conserve mode are true? (Choose two.)
- FortiGate starts dropping all new sessions when the system memory reaches the configured red threshold.
- FortiGate starts taking the configured action for new sessions requiring content inspection when the system memory reaches the configured red threshold.
- FortiGate enters conserve mode when the system memory reaches the configured extreme threshold.
- FortiGate exits conserve mode when the system memory goes below the configured green threshold
Correct answer: AD
Explanation:
Conserve Mode Activation:FortiGate enters conserve mode to prevent system crashes when the memory usage reaches critical levels. The 'red threshold' is the point at which FortiGate starts dropping new sessions to conserve memory.When the system memory usage exceeds this threshold, the FortiGate will block new sessions that require significant memory resources, such as those needing content inspection.Exiting Conserve Mode:The 'green threshold' is the memory usage level below which FortiGate exits conserve mode and resumes normal operation.Once the system memory usage drops below this threshold, FortiGate will start allowing new sessions again.Fortinet Community: Understanding conserve mode and its thresholds (Welcome to the Fortinet Community!) (Welcome to the Fortinet Community!).Fortinet Documentation: Memory conserve mode and thresholds (Welcome to the Fortinet Community!) (Fortinet GURU). Conserve Mode Activation:
FortiGate enters conserve mode to prevent system crashes when the memory usage reaches critical levels. The 'red threshold' is the point at which FortiGate starts dropping new sessions to conserve memory.
When the system memory usage exceeds this threshold, the FortiGate will block new sessions that require significant memory resources, such as those needing content inspection.
Exiting Conserve Mode:
The 'green threshold' is the memory usage level below which FortiGate exits conserve mode and resumes normal operation.
Once the system memory usage drops below this threshold, FortiGate will start allowing new sessions again.
Fortinet Community: Understanding conserve mode and its thresholds (Welcome to the Fortinet Community!) (Welcome to the Fortinet Community!).
Fortinet Documentation: Memory conserve mode and thresholds (Welcome to the Fortinet Community!) (Fortinet GURU).
Question 9
Refer to the exhibits, which show the configuration on FortiGate and partial session information for internet traffic from a user on the internal network.
If the priority on route ID _ were changed from 10 to 0, what would happen to traffic matching that user session?
- The session would be deleted, and the client would need to start a new session.
- The session would remain in the session table, but its traffic would now egress from both port1. andport2.
- The session would remain in the session table, and its traffic would egress from port2.
- The session would remain in the session table, and its traffic would egress from port1.
Correct answer: C
Explanation:
The exhibits show the configuration of static routes and a session table entry for an active session. The static routes are configured with different priorities:Route through port1 with a gateway of 10.200.1.254 and priority 5.Route through port2 with a gateway of 10.200.2.254 and priority 10.If the priority of the route through port2 is changed from 10 to 0, this route will become more preferred than the route through port1 because lower priority values indicate higher preference. As a result, the traffic for the existing session will switch to using the more preferred route:The session would remain active in the session table, as FortiGate does not immediately clear sessions upon route changes unless explicitly configured to do so.The traffic for the session would then start egressing from port2, which now has the higher priority route due to its lower priority value.Fortinet Documentation on Routing ConfigurationFortinet Community on Session Handling The exhibits show the configuration of static routes and a session table entry for an active session. The static routes are configured with different priorities:
Route through port1 with a gateway of 10.200.1.254 and priority 5.
Route through port2 with a gateway of 10.200.2.254 and priority 10.
If the priority of the route through port2 is changed from 10 to 0, this route will become more preferred than the route through port1 because lower priority values indicate higher preference. As a result, the traffic for the existing session will switch to using the more preferred route:
The session would remain active in the session table, as FortiGate does not immediately clear sessions upon route changes unless explicitly configured to do so.
The traffic for the session would then start egressing from port2, which now has the higher priority route due to its lower priority value.
Fortinet Documentation on Routing Configuration
Fortinet Community on Session Handling
Question 10
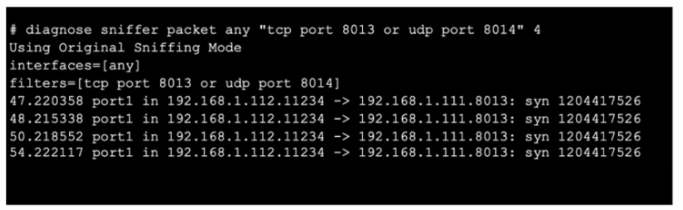
Refer to the exhibit, which shows oneway communication of the downstream FortiGate with the upstream FortiGate within a Security Fabric.

What three actions must you take to ensure successful communication? (Choose three.)
- Ensure the port for Neighbor Discovery has been changed.
- FortiGate must not be in NAT mode.
- Ensure TCP port 8013 is not blocked along the way
- You must authorize the downstream FortiGate on the root FortiGate.
- You must enable Security Fabric/Fortitelemetry on the receiving interface of the upstream FortiGate.
Correct answer: CDE
Explanation:
The exhibit shows a sniffer capture where TCP port 8013 is being used for communication. The communication appears one-way, indicating potential issues with the upstream FortiGate receiving the necessary packets or being able to respond.To ensure successful communication in a Security Fabric setup:Ensure TCP port 8013 is not blocked along the way: Verify that no firewalls or network devices between the downstream and upstream FortiGates are blocking TCP port 8013. This port is crucial for Security Fabric communication.Authorize the downstream FortiGate on the root FortiGate: In the Security Fabric, the root FortiGate must recognize and authorize the downstream FortiGate to allow proper communication and management.Enable Security Fabric/Fortitelemetry on the receiving interface of the upstream FortiGate: The upstream FortiGate must have the Security Fabric or Fortitelemetry enabled on the interface that receives the communication from the downstream FortiGate. This enables proper data exchange and monitoring within the Security Fabric.Fortinet Documentation on Security Fabric ConfigurationFortinet Community Discussion on Port Requirements The exhibit shows a sniffer capture where TCP port 8013 is being used for communication. The communication appears one-way, indicating potential issues with the upstream FortiGate receiving the necessary packets or being able to respond.
To ensure successful communication in a Security Fabric setup:
Ensure TCP port 8013 is not blocked along the way: Verify that no firewalls or network devices between the downstream and upstream FortiGates are blocking TCP port 8013. This port is crucial for Security Fabric communication.
Authorize the downstream FortiGate on the root FortiGate: In the Security Fabric, the root FortiGate must recognize and authorize the downstream FortiGate to allow proper communication and management.
Enable Security Fabric/Fortitelemetry on the receiving interface of the upstream FortiGate: The upstream FortiGate must have the Security Fabric or Fortitelemetry enabled on the interface that receives the communication from the downstream FortiGate. This enables proper data exchange and monitoring within the Security Fabric.
Fortinet Documentation on Security Fabric Configuration
Fortinet Community Discussion on Port Requirements

