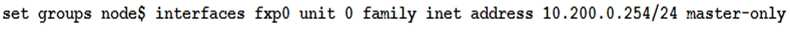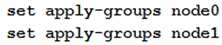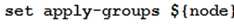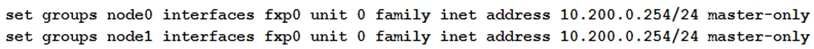File Info
| Exam | Security, Specialist |
| Number | JN0-334 |
| File Name | Juniper.JN0-334.TestKing.2020-05-12.28q.vcex |
| Size | 454 KB |
| Posted | May 12, 2020 |
| Download | Juniper.JN0-334.TestKing.2020-05-12.28q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
What are two examples of RTOs? (Choose two.)
- IPsec SA entries
- session table entries
- fabric link probes
- control link heartbeats
Correct answer: CD
Question 2
Which two statements are correct about server-protection SSP proxy? (Choose two.)
- The server-protection SSL proxy intercepts the server certificate.
- The server-protection SSL proxy is also known as SSL reverse proxy.
- The server-protection SSL proxy forwards the server certificate after modification.
- The server-protection SSL proxy acts as the server from the client’s perspective.
Correct answer: BD
Explanation:
Question 3
What are two types of attack objects used by IPS on SRX Series devices? (Choose two.)
- protocol anomaly-based attacks
- spam-based attacks
- signature-based attacks
- DDoS-based attacks
Correct answer: AC
Question 4
You are asked to improve resiliency for individual redundancy groups in an SRX4600 chassis cluster.
Which two features would accomplish this task? (Choose two.)
- IP address monitoring
- control link recovery
- interface monitoring
- dual fabric links
Correct answer: BD
Question 5
What are two elements of a custom IDP/IPS attack object? (Choose two.)
- the attack signature
- the severity of the attack
- the destination zone
- the exempt rulebase
Correct answer: AB
Question 6
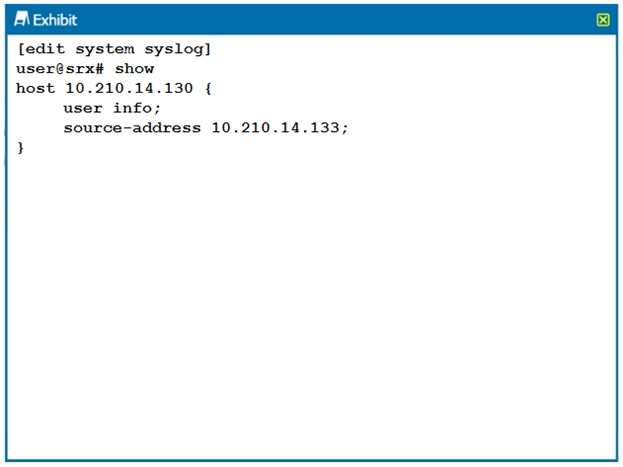

Referring to the configuration shown in the exhibit, which two statements are true? (Choose two.)
- The log is being stored on the local Routing Engine.
- The log is being sent to a remote server.
- The syslog is configured for a user facility.
- The syslog is configured for an info facility.
Correct answer: BC
Question 7
Which two statements are true about virtualized SRX Series devices? (Choose two.)
- vSRX cannot be deployed in transparent mode.
- cSRX can be deployed in routed mode.
- cSRX cannot be deployed in routed mode.
- vSRX can be deployed in transparent mode.
Correct answer: BD
Question 8
Which statement is true about JATP incidents?
- Incidents have an associated threat number assigned to them.
- Incidents are sorted by category, followed by severity.
- Incidents consist of all the events associated with a single threat.
- Incidents are always automatically mitigated.
Correct answer: C
Question 9
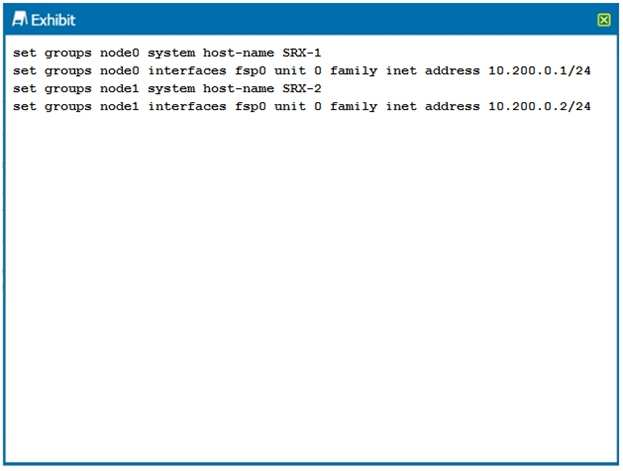

You are configuring an SRX chassis cluster with the node-specific hostname and management address.
Referring to the exhibit, which configuration completes this requirement?
Correct answer: C
Question 10
Which feature supports sandboxing of zero-day attacks?
- Sky ATP
- SSL proxy
- ALGs
- high availability
Correct answer: A