File Info
| Exam | Security-Professional |
| Number | JN0-637 |
| File Name | Juniper.JN0-637.VCEplus.2024-11-30.59q.vcex |
| Size | 5 MB |
| Posted | Nov 30, 2024 |
| Download | Juniper.JN0-637.VCEplus.2024-11-30.59q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
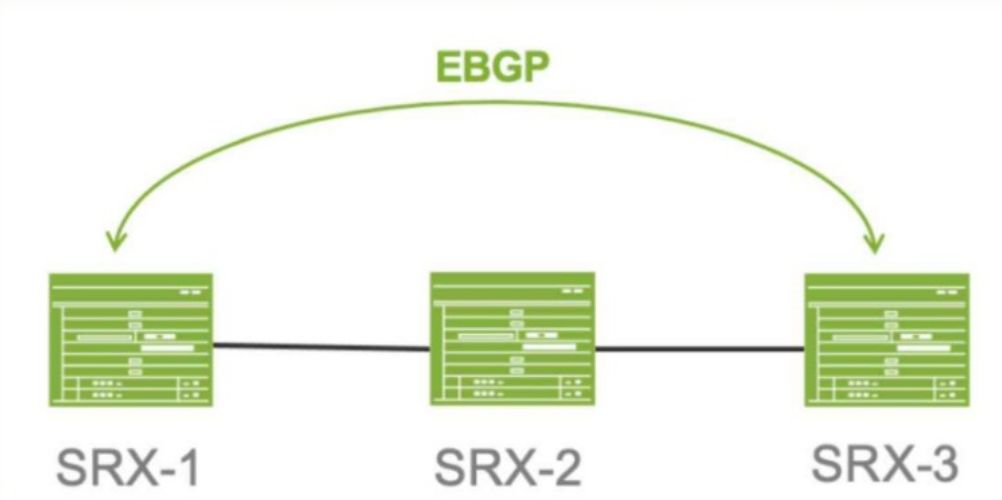
Click the Exhibit button.

Referring to the exhibit. SRX-1 and SRX-3 have to be connected using EBGP. The BGP configuration on SRX-1 and SRX-3 is verified and correct.
Which configuration on SRX-2 would establish an EBGP connection successfully between SRX-1 and SRX-3?
- The host-inbound-traffic statements do not allow EBGP traffic to traverse SRX-2.
- The security policy to allow SRX-1 and SRX-3 to communicate on TCP port 79 should be configured.
- The security policy to allow SRX-1 and SRX-3 to communicate on TCP port 169 should be configured.
- The security policy to allow SRX-1 and SRX-3 to communicate on TCP port 179 should be configured.
Correct answer: D
Explanation:
Comprehensive Detailed Step-by-Step Explanation with All Juniper Security ReferenceUnderstanding the Scenario:SRX-1 and SRX-3:Need to establish an EBGP session through SRX-2.Issue:BGP session is not coming up despite correct configurations on SRX-1 and SRX-3.Option D: The security policy to allow SRX-1 and SRX-3 to communicate on TCP port 179 should be configured.BGP uses TCP port 179 for establishing sessions.SRX-2 must have a security policy allowing traffic between SRX-1 and SRX-3 on TCP port 179.'Security policies must permit BGP traffic (TCP port 179) to allow BGP sessions through the SRX device.'Source: Juniper TechLibrary - Configuring Security Policies for Transit TrafficWhy Other Options Are Incorrect:Option A: Host-inbound-traffic affects traffic destined to SRX-2, not transit traffic.Option B and C: TCP ports 79 and 169 are unrelated to BGP.Conclusion:The correct option is D, configuring a security policy to allow TCP port 179. Comprehensive Detailed Step-by-Step Explanation with All Juniper Security Reference
Understanding the Scenario:
SRX-1 and SRX-3:
Need to establish an EBGP session through SRX-2.
Issue:
BGP session is not coming up despite correct configurations on SRX-1 and SRX-3.
Option D: The security policy to allow SRX-1 and SRX-3 to communicate on TCP port 179 should be configured.
BGP uses TCP port 179 for establishing sessions.
SRX-2 must have a security policy allowing traffic between SRX-1 and SRX-3 on TCP port 179.
'Security policies must permit BGP traffic (TCP port 179) to allow BGP sessions through the SRX device.'
Source: Juniper TechLibrary - Configuring Security Policies for Transit Traffic
Why Other Options Are Incorrect:
Option A: Host-inbound-traffic affects traffic destined to SRX-2, not transit traffic.
Option B and C: TCP ports 79 and 169 are unrelated to BGP.
Conclusion:
The correct option is D, configuring a security policy to allow TCP port 179.
Question 2
In a multinode HA environment, which service must be configured to synchronize between nodes?
- Advanced policy-based routing
- PKI certificates
- IPsec VPN
- IDP
Correct answer: B
Question 3
A company has acquired a new branch office that has the same address space of one of its local networks, 192.168.100/24. The offices need to communicate with each other.
Which two NAT configurations will satisfy this requirement? (Choose two.)
- [edit security nat source] user@OfficeA# show rule-set OfficeBtoA { from zone OfficeB; to zone OfficeA; rule 1 { match { source-address 192.168.210.0/24; destination-address 192.168.200.0/24; } then { source-nat {interface; } } } }
- [edit security nat static] user@OfficeA# show rule-set From-Office-B { from interface ge-0/0/0.0; rule 1 { match { destination-address 192.168.200.0/24; } then { static-nat { prefix 192.168.100.0/24; } } } }
- [edit security nat static] user@OfficeB# show rule-set From-Office-A { from interface ge-0/0/0.0; rule 1 { match { destination-address 192.168.210.0/24; } then { static-nat { prefix 192.168.100.0/24; } } } }
- [edit security nat source] user@OfficeB# show rule-set OfficeAtoB { from zone OfficeA; to zone OfficeB; rule 1 { match { source-address 192.168.200.0/24; destination-address 192.168.210.0/24; } then { source-nat {interface; } } } }
Correct answer: AD
Explanation:
The problem describes two offices needing to communicate, but both share the same IP address space, 192.168.100.0/24. To resolve this, NAT must be configured to translate the conflicting address spaces on each side.Here's how each of the configurations works:Option A (Correct):This source NAT rule translates the source address of traffic from Office B to Office A. By configuring source NAT, the source IP addresses from Office B (192.168.210.0/24) will be translated when communicating with Office A (192.168.200.0/24). This method ensures that there is no overlap in address space when packets are transmitted between the two offices.Option D (Correct):This is a source NAT rule configured on Office B, which translates the source addresses from Office A to prevent address conflicts. It ensures that when traffic is initiated from Office A to Office B, the overlapping address range (192.168.100.0/24) is translated.Options B and C (Incorrect):These options involve static NAT rules that map address ranges between the two offices, but they do not resolve the overlapping IP address space issue effectively. Static NAT is not the optimal solution in this scenario since the problem involves address space conflict, which requires translation of source addresses during communication.JuniperReference:Juniper NAT Configuration Guide: Detailed instructions on how to configure source NAT and resolve address conflicts between networks. The problem describes two offices needing to communicate, but both share the same IP address space, 192.168.100.0/24. To resolve this, NAT must be configured to translate the conflicting address spaces on each side.
Here's how each of the configurations works:
Option A (Correct):
This source NAT rule translates the source address of traffic from Office B to Office A. By configuring source NAT, the source IP addresses from Office B (192.168.210.0/24) will be translated when communicating with Office A (192.168.200.0/24). This method ensures that there is no overlap in address space when packets are transmitted between the two offices.
Option D (Correct):
This is a source NAT rule configured on Office B, which translates the source addresses from Office A to prevent address conflicts. It ensures that when traffic is initiated from Office A to Office B, the overlapping address range (192.168.100.0/24) is translated.
Options B and C (Incorrect):
These options involve static NAT rules that map address ranges between the two offices, but they do not resolve the overlapping IP address space issue effectively. Static NAT is not the optimal solution in this scenario since the problem involves address space conflict, which requires translation of source addresses during communication.
Juniper
Reference:
Juniper NAT Configuration Guide: Detailed instructions on how to configure source NAT and resolve address conflicts between networks.
Question 4
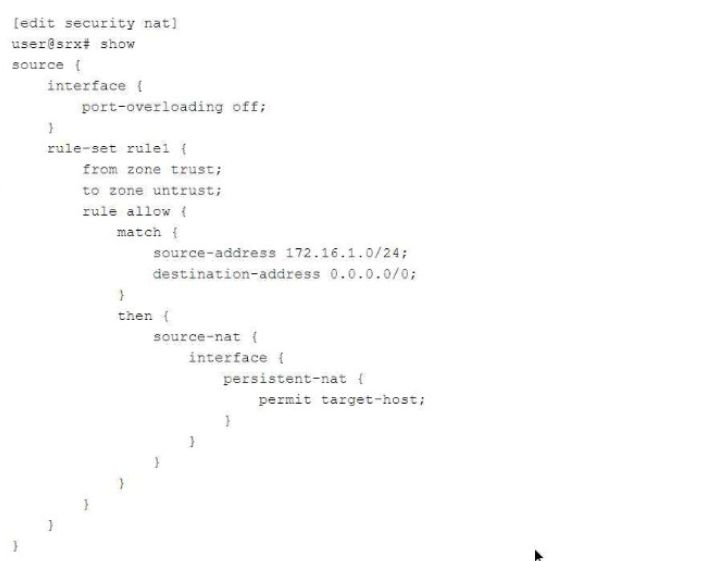
Referring to the exhibit,

which two statements are correct about the NAT configuration? (Choose two.)
- Both the internal and the external host can initiate a session after the initial translation.
- Only a specific host can initiate a session to the reflexive address after the initial session.
- Any external host will be able to initiate a session to the reflexive address.
- The original destination port is used for the source port for the session.
Correct answer: AB
Question 5
You are attempting to ping an interface on your SRX Series device, but the ping is unsuccessful.
What are three reasons for this behavior? (Choose three.)
- The interface is not assigned to a security zone.
- The interface's host-inbound-traffic security zone configuration does not permit ping
- The ping traffic is matching a firewall filter.
- The device has J-Web enabled.
- The interface has multiple logical units configured.
Correct answer: ABC
Explanation:
A . The interface is not assigned to a security zone.SRX Series devices rely heavily on security zones for traffic management. If an interface isn't assigned to a zone, the device won't know how to handle traffic arriving on that interface, including ping requests (ICMP echo requests).B . The interface's host-inbound-traffic security zone configuration does not permit ping.Even if an interface is in a zone, you must explicitly allow ICMP ping traffic within the zone's host-inbound-traffic settings. By default, most zones block ping for security reasons.C . The ping traffic is matching a firewall filter.Firewall filters (configured using the security policies hierarchy) can block specific traffic types, including ICMP. If a filter is applied to the interface or zone, and it doesn't have a rule to permit ping, the ping will be unsuccessful.Why other options are incorrect:D . The device has J-Web enabled. J-Web is a web-based management interface and has no direct impact on the device's ability to respond to pings.E . The interface has multiple logical units configured. Logical units divide a physical interface into multiple virtual interfaces. While this can affect routing and traffic flow, it doesn't inherently prevent ping responses as long as the relevant zones and policies are correctly configured.Troubleshooting Steps:If you're unable to ping an SRX interface, here's a systematic approach to troubleshoot:Verify Interface Status: Ensure the interface is up and operational using show interfaces terse.Check Zone Assignment: Confirm the interface belongs to a security zone using show security zones. Examine host-inbound-traffic: Verify that the zone's host-inbound-traffic settings allow ping (e.g., set security zones security-zone trust host-inbound-traffic system-services ping).Analyze Firewall Filters: Review any firewall filters applied to the interface or zone to ensure they allow ICMP ping traffic. Use show security policies and monitor traffic to diagnose filter behavior.Test from Different Zones: Try pinging the interface from devices in different zones to isolate potential policy issues.By systematically checking these aspects, you can identify the root cause and resolve the ping issue on your SRX Series device. A . The interface is not assigned to a security zone.
SRX Series devices rely heavily on security zones for traffic management. If an interface isn't assigned to a zone, the device won't know how to handle traffic arriving on that interface, including ping requests (ICMP echo requests).
B . The interface's host-inbound-traffic security zone configuration does not permit ping.
Even if an interface is in a zone, you must explicitly allow ICMP ping traffic within the zone's host-inbound-traffic settings. By default, most zones block ping for security reasons.
C . The ping traffic is matching a firewall filter.
Firewall filters (configured using the security policies hierarchy) can block specific traffic types, including ICMP. If a filter is applied to the interface or zone, and it doesn't have a rule to permit ping, the ping will be unsuccessful.
Why other options are incorrect:
D . The device has J-Web enabled. J-Web is a web-based management interface and has no direct impact on the device's ability to respond to pings.
E . The interface has multiple logical units configured. Logical units divide a physical interface into multiple virtual interfaces. While this can affect routing and traffic flow, it doesn't inherently prevent ping responses as long as the relevant zones and policies are correctly configured.
Troubleshooting Steps:
If you're unable to ping an SRX interface, here's a systematic approach to troubleshoot:
Verify Interface Status: Ensure the interface is up and operational using show interfaces terse.
Check Zone Assignment: Confirm the interface belongs to a security zone using show security zones.
Examine host-inbound-traffic: Verify that the zone's host-inbound-traffic settings allow ping (e.g., set security zones security-zone trust host-inbound-traffic system-services ping).
Analyze Firewall Filters: Review any firewall filters applied to the interface or zone to ensure they allow ICMP ping traffic. Use show security policies and monitor traffic to diagnose filter behavior.
Test from Different Zones: Try pinging the interface from devices in different zones to isolate potential policy issues.
By systematically checking these aspects, you can identify the root cause and resolve the ping issue on your SRX Series device.
Question 6
You are deploying IPsec VPNs to securely connect several enterprise sites with ospf for dynamic
routing. Some of these sites are secured by third-party devices not running Junos.
Which two statements are true for this deployment? (Choose two.)
- OSPF over IPsec can be used for intersite dynamic routing.
- Sites with overlapping address spaces can be supported.
- OSPF over GRE over IPsec is required to enable intersite dynamic routing
- Sites with overlapping address spaces cannot be supported.
Correct answer: BC
Explanation:
Understanding the Scenario:Objective: Deploy IPsec VPNs connecting multiple enterprise sites using OSPF for dynamic routing.Challenge: Some sites use third-party devices not running Junos OS.Considerations:Compatibility between Juniper and third-party devices.Support for dynamic routing protocols (OSPF) over IPsec VPNs.Handling overlapping IP address spaces.Option Analysis:Option A: OSPF over IPsec can be used for intersite dynamic routing.OSPF Characteristics:OSPF uses multicast addresses (224.0.0.5 and 224.0.0.6) for neighbor discovery and routing updates.IPsec Limitations:Standard IPsec tunnel mode does not support multicast traffic natively.Multicast traffic cannot traverse IPsec tunnels unless encapsulated.Juniper Solution:Juniper devices can use routed VPNs (route-based VPNs) with st0 interfaces, allowing OSPF over IPsec.However, this requires support from both ends of the VPN tunnel.Third-Party Devices:May not support OSPF over IPsec without additional configurations.Conclusion:Option A is not universally true in this scenario due to third-party device limitations.'OSPF can be run over IPsec VPNs using route-based VPNs, but interoperability with third-party devices must be verified.'Source: Juniper TechLibrary - OSPF over IPsec VPNsOption B: Sites with overlapping address spaces can be supported.Overlapping IP Address Spaces:Occurs when different sites use the same IP subnets.Can cause routing ambiguities and conflicts.Solution:NAT over VPN:Use Network Address Translation (NAT) to translate overlapping IP addresses to unique addresses.Juniper devices support NAT over IPsec VPNs.Third-Party Device Considerations:Need to ensure third-party devices support NAT over IPsec.Many enterprise-grade devices provide this functionality.Conclusion:Option B is true; overlapping address spaces can be supported using NAT.'When sites have overlapping IP addresses, NAT can be used over IPsec VPNs to resolve address conflicts.'Source: Juniper TechLibrary - NAT with IPsec VPNsOption C: OSPF over GRE over IPsec is required to enable intersite dynamic routing.GRE Tunnels:Generic Routing Encapsulation (GRE) can encapsulate multicast and broadcast traffic.Allows OSPF packets to be transmitted over IPsec VPNs.IPsec Encryption:GRE tunnels can be encrypted using IPsec for secure communication.Interoperability:GRE over IPsec is a common method to support OSPF between devices from different vendors.Third-party devices are more likely to support GRE over IPsec than OSPF over IPsec directly.Conclusion:Option C is true; using OSPF over GRE over IPsec is required in this scenario.'To run OSPF between devices that do not support multicast over IPsec, GRE tunnels can be used over IPsec VPNs.'Source: Juniper TechLibrary - Configuring GRE over IPsecOption D: Sites with overlapping address spaces cannot be supported.Contradicts Option B.As established, overlapping address spaces can be supported using NAT over IPsec VPNs.Conclusion:Option D is false.Conclusion:Answer:s: B and COption B: Overlapping address spaces can be supported using NAT over IPsec VPNs.Option C: OSPF over GRE over IPsec is required to enable intersite dynamic routing, especially when third-party devices are involved.Additional DetailedWhy OSPF over IPsec May Not Be Feasible (Option A):Multicast Traffic:OSPF relies on multicast for neighbor discovery and updates.IPsec in tunnel mode does not natively support multicast traffic.Third-Party Devices:May not support proprietary extensions or configurations required to run OSPF directly over IPsec.Workaround:Encapsulate OSPF multicast packets within GRE tunnels, which can carry multicast traffic over unicast IPsec tunnels.Why OSPF over GRE over IPsec Is Necessary (Option C):GRE Tunnels:Encapsulate multicast/broadcast traffic into unicast packets.Allow routing protocols like OSPF to function over IPsec VPNs.Compatibility:GRE is a widely supported protocol across different vendors.Facilitates interoperability between Juniper and third-party devices.Supporting Overlapping Address Spaces (Option B):NAT over IPsec:Translates private IP addresses to unique addresses across the VPN.Prevents routing conflicts and allows communication between sites with overlapping subnets.Considerations:Requires proper configuration on both ends of the VPN tunnel.Third-party devices must support NAT over IPsec.Reference to Juniper Security Concepts:Route-Based VPNs:'Route-based VPNs use virtual tunnel interfaces (st0) and support dynamic routing protocols over IPsec.'Source: Juniper TechLibrary - Route-Based VPNsGRE over IPsec:'GRE over IPsec allows the transmission of multicast and non-IP protocols over IPsec tunnels.'Source: Juniper TechLibrary - GRE over IPsec OverviewNAT with IPsec VPNs:'NAT can be applied to IPsec VPN traffic to resolve overlapping address issues and facilitate communication between sites.'Source: Juniper TechLibrary - NAT with IPsecFinal Notes:Interoperability:When working with third-party devices, always verify compatibility for protocols and features.Best Practices:Use GRE over IPsec for dynamic routing protocols requiring multicast support across IPsec VPNs.Implement NAT over VPN when dealing with overlapping address spaces. Understanding the Scenario:Objective: Deploy IPsec VPNs connecting multiple enterprise sites using OSPF for dynamic routing.Challenge: Some sites use third-party devices not running Junos OS.Considerations:Compatibility between Juniper and third-party devices.Support for dynamic routing protocols (OSPF) over IPsec VPNs.Handling overlapping IP address spaces.Option Analysis:Option A: OSPF over IPsec can be used for intersite dynamic routing.OSPF Characteristics:OSPF uses multicast addresses (224.0.0.5 and 224.0.0.6) for neighbor discovery and routing updates.IPsec Limitations:Standard IPsec tunnel mode does not support multicast traffic natively.Multicast traffic cannot traverse IPsec tunnels unless encapsulated.Juniper Solution:Juniper devices can use routed VPNs (route-based VPNs) with st0 interfaces, allowing OSPF over IPsec.However, this requires support from both ends of the VPN tunnel.Third-Party Devices:May not support OSPF over IPsec without additional configurations.Conclusion:Option A is not universally true in this scenario due to third-party device limitations.'OSPF can be run over IPsec VPNs using route-based VPNs, but interoperability with third-party devices must be verified.'Source: Juniper TechLibrary - OSPF over IPsec VPNsOption B: Sites with overlapping address spaces can be supported.Overlapping IP Address Spaces:Occurs when different sites use the same IP subnets.Can cause routing ambiguities and conflicts.Solution:NAT over VPN:Use Network Address Translation (NAT) to translate overlapping IP addresses to unique addresses.Juniper devices support NAT over IPsec VPNs.Third-Party Device Considerations:Need to ensure third-party devices support NAT over IPsec.Many enterprise-grade devices provide this functionality.Conclusion:Option B is true; overlapping address spaces can be supported using NAT.'When sites have overlapping IP addresses, NAT can be used over IPsec VPNs to resolve address conflicts.'Source: Juniper TechLibrary - NAT with IPsec VPNsOption C: OSPF over GRE over IPsec is required to enable intersite dynamic routing.GRE Tunnels:Generic Routing Encapsulation (GRE) can encapsulate multicast and broadcast traffic.Allows OSPF packets to be transmitted over IPsec VPNs.IPsec Encryption:GRE tunnels can be encrypted using IPsec for secure communication.Interoperability:GRE over IPsec is a common method to support OSPF between devices from different vendors.Third-party devices are more likely to support GRE over IPsec than OSPF over IPsec directly.Conclusion:Option C is true; using OSPF over GRE over IPsec is required in this scenario.'To run OSPF between devices that do not support multicast over IPsec, GRE tunnels can be used over IPsec VPNs.'Source: Juniper TechLibrary - Configuring GRE over IPsecOption D: Sites with overlapping address spaces cannot be supported.Contradicts Option B.As established, overlapping address spaces can be supported using NAT over IPsec VPNs.Conclusion:Option D is false.Conclusion:Answer:s: B and COption B: Overlapping address spaces can be supported using NAT over IPsec VPNs.Option C: OSPF over GRE over IPsec is required to enable intersite dynamic routing, especially when third-party devices are involved.Additional DetailedWhy OSPF over IPsec May Not Be Feasible (Option A):Multicast Traffic:OSPF relies on multicast for neighbor discovery and updates.IPsec in tunnel mode does not natively support multicast traffic.Third-Party Devices:May not support proprietary extensions or configurations required to run OSPF directly over IPsec.Workaround:Encapsulate OSPF multicast packets within GRE tunnels, which can carry multicast traffic over unicast IPsec tunnels.Why OSPF over GRE over IPsec Is Necessary (Option C):GRE Tunnels:Encapsulate multicast/broadcast traffic into unicast packets.Allow routing protocols like OSPF to function over IPsec VPNs.Compatibility:GRE is a widely supported protocol across different vendors.Facilitates interoperability between Juniper and third-party devices.Supporting Overlapping Address Spaces (Option B):NAT over IPsec:Translates private IP addresses to unique addresses across the VPN.Prevents routing conflicts and allows communication between sites with overlapping subnets.Considerations:Requires proper configuration on both ends of the VPN tunnel.Third-party devices must support NAT over IPsec.Reference to Juniper Security Concepts:Route-Based VPNs:'Route-based VPNs use virtual tunnel interfaces (st0) and support dynamic routing protocols over IPsec.'Source: Juniper TechLibrary - Route-Based VPNsGRE over IPsec:'GRE over IPsec allows the transmission of multicast and non-IP protocols over IPsec tunnels.'Source: Juniper TechLibrary - GRE over IPsec OverviewNAT with IPsec VPNs:'NAT can be applied to IPsec VPN traffic to resolve overlapping address issues and facilitate communication between sites.'Source: Juniper TechLibrary - NAT with IPsecFinal Notes:Interoperability:When working with third-party devices, always verify compatibility for protocols and features.Best Practices:Use GRE over IPsec for dynamic routing protocols requiring multicast support across IPsec VPNs.Implement NAT over VPN when dealing with overlapping address spaces.
Question 7
Exhibit:
You have deployed a pair of SRX series devices in a multimode HA environment. You need to enable IPsec encryption on the interchassis link.
Referring to the exhibit, which three steps are required to enable ICL encryption? (Choose three.)
- Install the Junos IKE package on both nodes.
- Enable OSPF for both interchassis link interfaces and tum on the dynamic-neighbors parameter.
- Configure a VPN profile for the HA traffic and apply to both nodes.
- Enable HA link encryption in the IPsec profile on both nodes.
- Enable HA link encryption in the IKE profile on both nodes,
Correct answer: ACD
Explanation:
A . Install the Junos IKE package on both nodes. While I previously stated that IKE is usually included in the base Junos OS image, it's essential to ensure that the necessary IKE package is indeed installed and enabled on both SRX nodes to support ICL encryption.C . Configure a VPN profile for the HA traffic and apply it to both nodes. This dedicated VPN profile defines the security parameters (encryption algorithms, authentication, etc.) specifically for the ICL traffic.D . Enable HA link encryption in the IPsec profile on both nodes. Within the IPsec profile, you must explicitly enable ICL encryption to ensure that all traffic traversing the interchassis link is protected.Why E is incorrect:E . Enable HA link encryption in the IKE profile on both nodes. While securing IKE negotiations is important, it's typically handled within the IPsec profile itself when configuring ICL encryption on SRX devices. A . Install the Junos IKE package on both nodes. While I previously stated that IKE is usually included in the base Junos OS image, it's essential to ensure that the necessary IKE package is indeed installed and enabled on both SRX nodes to support ICL encryption.
C . Configure a VPN profile for the HA traffic and apply it to both nodes. This dedicated VPN profile defines the security parameters (encryption algorithms, authentication, etc.) specifically for the ICL traffic.
D . Enable HA link encryption in the IPsec profile on both nodes. Within the IPsec profile, you must explicitly enable ICL encryption to ensure that all traffic traversing the interchassis link is protected.
Why E is incorrect:
E . Enable HA link encryption in the IKE profile on both nodes. While securing IKE negotiations is important, it's typically handled within the IPsec profile itself when configuring ICL encryption on SRX devices.
Question 8
What are three core components for enabling advanced policy-based routing? (Choose three.)
- Filter-based forwarding
- Routing options
- Routing instance
- APBR profile
- Policies
Correct answer: ACD
Explanation:
To enable Advanced Policy-Based Routing (APBR) on SRX Series devices, three key components are necessary: filter-based forwarding, routing instances, and APBR profiles. Filter-based forwarding is utilized to direct specific traffic flows to a routing instance based on criteria set by a policy. Routing instances allow the traffic to be managed independently of the main routing table, and APBR profiles define how and when traffic should be forwarded. These elements ensure that APBR is flexible and tailored to the network's requirements. Refer to Juniper's APBR Documentation for more details.Advanced policy-based routing (APBR) in Juniper's SRX devices allows the selection of different paths for traffic based on policies, rather than relying purely on routing tables. To enable APBR, the following core components are required:Filter-based Forwarding (Answer A): Filter-based forwarding (FBF) is a technique used to forward traffic based on policies rather than the default routing table. It is essential for enabling APBR, as it helps match traffic based on filters and directs it to specific routes.Configuration Example:bashset firewall family inet filter FBF match-term source-address 192.168.1.0/24set firewall family inet filter FBF then routing-instance custom-routing-instanceRouting Instance (Answer C): A routing instance is required to define the separate routing table used by APBR. You can create multiple routing instances and assign traffic to these instances based on policies. The traffic will then use the routes defined within the specific routing instance.Configuration Example:bashset routing-instances custom-routing-instance instance-type forwardingset routing-instances custom-routing-instance routing-options static route 0.0.0.0/0 next-hop 10.10.10.1APBR Profile (Answer D): The APBR profile defines the rules and policies for advanced policy-based routing. It allows you to set up conditions such as traffic type, source/destination address, and port, and then assign actions such as redirecting traffic to specific routing instances.Configuration Example:bashset security forwarding-options advanced-policy-based-routing profile apbr-profile match application http set security forwarding-options advanced-policy-based-routing profile apbr-profile then routing-instance custom-routing-instanceOther Components:Routing Options (Answer B) are not a core component of APBR, as routing options define the general behavior of the routing table and protocols. However, APBR works by overriding these default routing behaviors using policies.Policies (Answer E) are crucial in many network configurations but are not a core component of enabling APBR. APBR specifically relies on profiles rather than standard security policies.Juniper SecurityReference:Advanced Policy-Based Routing (APBR): Juniper's APBR is a powerful tool that allows routing based on specific traffic characteristics rather than relying on static routing tables. APBR ensures that specific types of traffic can take alternate paths based on business or network needs. Reference: Juniper Networks APBR Documentation. To enable Advanced Policy-Based Routing (APBR) on SRX Series devices, three key components are necessary: filter-based forwarding, routing instances, and APBR profiles. Filter-based forwarding is utilized to direct specific traffic flows to a routing instance based on criteria set by a policy. Routing instances allow the traffic to be managed independently of the main routing table, and APBR profiles define how and when traffic should be forwarded. These elements ensure that APBR is flexible and tailored to the network's requirements. Refer to Juniper's APBR Documentation for more details.
Advanced policy-based routing (APBR) in Juniper's SRX devices allows the selection of different paths for traffic based on policies, rather than relying purely on routing tables. To enable APBR, the following core components are required:
Filter-based Forwarding (Answer A): Filter-based forwarding (FBF) is a technique used to forward traffic based on policies rather than the default routing table. It is essential for enabling APBR, as it helps match traffic based on filters and directs it to specific routes.
Configuration Example:
bash
set firewall family inet filter FBF match-term source-address 192.168.1.0/24
set firewall family inet filter FBF then routing-instance custom-routing-instance
Routing Instance (Answer C): A routing instance is required to define the separate routing table used by APBR. You can create multiple routing instances and assign traffic to these instances based on policies. The traffic will then use the routes defined within the specific routing instance.
Configuration Example:
bash
set routing-instances custom-routing-instance instance-type forwarding
set routing-instances custom-routing-instance routing-options static route 0.0.0.0/0 next-hop 10.10.10.1
APBR Profile (Answer D): The APBR profile defines the rules and policies for advanced policy-based routing. It allows you to set up conditions such as traffic type, source/destination address, and port, and then assign actions such as redirecting traffic to specific routing instances.
Configuration Example:
bash
set security forwarding-options advanced-policy-based-routing profile apbr-profile match application http
set security forwarding-options advanced-policy-based-routing profile apbr-profile then routing-instance custom-routing-instance
Other Components:
Routing Options (Answer B) are not a core component of APBR, as routing options define the general behavior of the routing table and protocols. However, APBR works by overriding these default routing behaviors using policies.
Policies (Answer E) are crucial in many network configurations but are not a core component of enabling APBR. APBR specifically relies on profiles rather than standard security policies.
Juniper Security
Reference:
Advanced Policy-Based Routing (APBR): Juniper's APBR is a powerful tool that allows routing based on specific traffic characteristics rather than relying on static routing tables. APBR ensures that specific types of traffic can take alternate paths based on business or network needs. Reference: Juniper Networks APBR Documentation.
Question 9
You want to bypass IDP for traffic destined to social media sites using APBR, but it is not working and IDP is dropping the session.
What are two reasons for this problem? (Choose two.)
- The session did not properly reclassify midstream to the correct APBR rule.
- IDP disable is not configured on the APBR rule.
- The application services bypass is not configured on the APBR rule.
- The APBR rule does a match on the first packet.
Correct answer: AC
Explanation:
of Answer A (Session Reclassification):APBR (Advanced Policy-Based Routing) requires the session to be classified based on the specified rule, which can change midstream as additional packets are processed. If the session was already established before the APBR rule took effect, the traffic may not be correctly reclassified to match the new APBR rule, leading to IDP (Intrusion Detection and Prevention) processing instead of being bypassed. This can occur especially when the session was already established before the rule change. of Answer C (Application Services Bypass):For APBR to work and bypass the IDP service, the application services bypass must be explicitly configured. Without this configuration, the APBR rule may redirect the traffic, but the IDP service will still inspect and potentially drop the traffic. This is especially important for traffic destined for specific sites like social media platforms where bypassing IDP is desired.Example configuration for bypassing IDP services:bashset security forwarding-options advanced-policy-based-routing profile application-services-bypassStep-by-Step Resolution:Reclassify the Session Midstream:If the traffic was already being processed before the APBR rule was applied, ensure that the session is reclassified by terminating the current session or ensuring the APBR rule is applied from the start.Command to clear the session:bashclear security flow session destination-prefix <ip-address>Configure Application Services Bypass:Ensure that the APBR rule includes the application services bypass configuration to properly bypass IDP or any other security services for traffic that should not be inspected.Example configuration:bashset security forwarding-options advanced-policy-based-routing profile application-services-bypassJuniper SecurityReference:Session Reclassification in APBR: APBR requires reclassification of sessions in real-time to ensure midstream packets are processed by the correct rule. This is crucial when policies change dynamically or new rules are added.Application Services Bypass in APBR: This feature ensures that security services such as IDP are bypassed for traffic that matches specific APBR rules. This is essential for applications where performance is a priority and security inspection is not necessary. of Answer A (Session Reclassification):
APBR (Advanced Policy-Based Routing) requires the session to be classified based on the specified rule, which can change midstream as additional packets are processed. If the session was already established before the APBR rule took effect, the traffic may not be correctly reclassified to match the new APBR rule, leading to IDP (Intrusion Detection and Prevention) processing instead of being bypassed. This can occur especially when the session was already established before the rule change.
of Answer C (Application Services Bypass):
For APBR to work and bypass the IDP service, the application services bypass must be explicitly configured. Without this configuration, the APBR rule may redirect the traffic, but the IDP service will still inspect and potentially drop the traffic. This is especially important for traffic destined for specific sites like social media platforms where bypassing IDP is desired.
Example configuration for bypassing IDP services:
bash
set security forwarding-options advanced-policy-based-routing profile application-services-bypass
Step-by-Step Resolution:
Reclassify the Session Midstream:
If the traffic was already being processed before the APBR rule was applied, ensure that the session is reclassified by terminating the current session or ensuring the APBR rule is applied from the start.
Command to clear the session:
bash
clear security flow session destination-prefix <ip-address>
Configure Application Services Bypass:
Ensure that the APBR rule includes the application services bypass configuration to properly bypass IDP or any other security services for traffic that should not be inspected.
Example configuration:
bash
set security forwarding-options advanced-policy-based-routing profile application-services-bypass
Juniper Security
Reference:
Session Reclassification in APBR: APBR requires reclassification of sessions in real-time to ensure midstream packets are processed by the correct rule. This is crucial when policies change dynamically or new rules are added.
Application Services Bypass in APBR: This feature ensures that security services such as IDP are bypassed for traffic that matches specific APBR rules. This is essential for applications where performance is a priority and security inspection is not necessary.
Question 10
Which two statements are correct about mixed mode? (Choose two.)
- Layer 2 and Layer 3 interfaces can use the same security zone.
- IRB interfaces can be used to route traffic.
- Layer 2 and Layer 3 interfaces can use separate security zones.
- IRB interfaces cannot be used to route traffic.
Correct answer: BC


