File Info
| Exam | Microsoft Azure Security Technologies |
| Number | AZ-500 |
| File Name | Microsoft.AZ-500.NewDumps.2021-02-28.250q.vcex |
| Size | 32 MB |
| Posted | Feb 28, 2021 |
| Download | Microsoft.AZ-500.NewDumps.2021-02-28.250q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
You need to meet the technical requirements for VNetwork1.
What should you do first?
- Create a new subnet on VNetwork1.
- Remove the NSGs from Subnet11 and Subnet13.
- Associate an NSG to Subnet12.
- Configure DDoS protection for VNetwork1.
Correct answer: A
Explanation:
From scenario: Deploy Azure Firewall to VNetwork1 in Sub2.Azure firewall needs a dedicated subnet named AzureFirewallSubnet. References:https://docs.microsoft.com/en-us/azure/firewall/tutorial-firewall-deploy-portal From scenario: Deploy Azure Firewall to VNetwork1 in Sub2.
Azure firewall needs a dedicated subnet named AzureFirewallSubnet.
References:
https://docs.microsoft.com/en-us/azure/firewall/tutorial-firewall-deploy-portal
Question 2
You need to ensure that User2 can implement PIM.
What should you do first?
- Assign User2 the Global administrator role.
- Configure authentication methods for contoso.com.
- Configure the identity secure score for contoso.com.
- Enable multi-factor authentication (MFA) for User2.
Correct answer: A
Explanation:
To start using PIM in your directory, you must first enable PIM. 1. Sign in to the Azure portal as a Global Administrator of your directory. You must be a Global Administrator with an organizational account (for example, @yourdomain.com), not a Microsoft account (for example, @outlook.com), to enable PIM for a directory. Scenario: Technical requirements include: Enable Azure AD Privileged Identity Management (PIM) for contoso.com References:https://docs.microsoft.com/bs-latn-ba/azure/active-directory/privileged-identity-management/pim-getting-started To start using PIM in your directory, you must first enable PIM.
1. Sign in to the Azure portal as a Global Administrator of your directory.
You must be a Global Administrator with an organizational account (for example, @yourdomain.com), not a Microsoft account (for example, @outlook.com), to enable PIM for a directory.
Scenario: Technical requirements include: Enable Azure AD Privileged Identity Management (PIM) for contoso.com
References:
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/privileged-identity-management/pim-getting-started
Question 3


What is the membership of Group1 and Group2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Box 1: User1, User2, User3, User4 Contains "ON" is true for Montreal (User1), MONTREAL (User2), London (User 3), and Ontario (User4) as string and regex operations are not case sensitive. Box 2: Only User3Match "*on" is only true for London (User3). Scenario:Contoso.com contains the users shown in the following table. Contoso.com contains the security groups shown in the following table. References:https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership Box 1: User1, User2, User3, User4
Contains "ON" is true for Montreal (User1), MONTREAL (User2), London (User 3), and Ontario (User4) as string and regex operations are not case sensitive.
Box 2: Only User3
Match "*on" is only true for London (User3).
Scenario:
Contoso.com contains the users shown in the following table.

Contoso.com contains the security groups shown in the following table.

References:
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership
Question 4


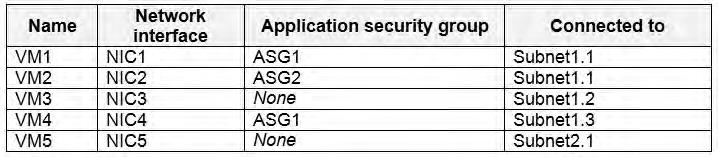


You are evaluating the security of the network communication between the virtual machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Box 1: Yes NSG1 has the inbound security rules shown in the following table. NSG2 has the inbound security rules shown in the following table. Box 2: YesBox 3: NoNote:Sub2 contains the virtual machines shown in the following table. Sub2 contains the network security groups (NSGs) shown in the following table. Box 1: Yes
NSG1 has the inbound security rules shown in the following table.

NSG2 has the inbound security rules shown in the following table.

Box 2: Yes
Box 3: No
Note:
Sub2 contains the virtual machines shown in the following table.


Sub2 contains the network security groups (NSGs) shown in the following table.

Question 5
You are evaluating the effect of the application security groups on the network communication between the virtual machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Box 1: No. VM4 is in Subnet13 which has NSG3 attached to it. VM1 is in ASG1. NSG3 would only allow ICMP pings from ASG2 but not ASG1. Only TCP traffic is allowed from ASG1. NSG3 has the inbound security rules shown in the following table. Box 2: Yes.VM2 is in ASG2. Any protocol is allowed from ASG2 so ICMP ping would be allowed. Box3. VM1 is in ASG1. TCP traffic is allowed from ASG1 so VM1 could connect to the web server as connections to the web server would be on ports TCP 80 or TCP 443. Box 1: No. VM4 is in Subnet13 which has NSG3 attached to it.
VM1 is in ASG1. NSG3 would only allow ICMP pings from ASG2 but not ASG1. Only TCP traffic is allowed from ASG1.
NSG3 has the inbound security rules shown in the following table.
Box 2: Yes.
VM2 is in ASG2. Any protocol is allowed from ASG2 so ICMP ping would be allowed.
Box3. VM1 is in ASG1. TCP traffic is allowed from ASG1 so VM1 could connect to the web server as connections to the web server would be on ports TCP 80 or TCP 443.
Question 6
You assign User8 the Owner role for RG4, RG5, and RG6.
In which resource groups can User8 create virtual networks and NSGs? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Box 1: RG4 only Virtual Networks are not allowed for Rg5 and Rg6. Box 2: Rg4 and Rg6Scenario:Contoso has two Azure subscriptions named Sub1 and Sub2. Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6. You assign User8 the Owner role for RG4, RG5, and RG6 User8 city Sidney, Role:NoneNote: A network security group (NSG) contains a list of security rules that allow or deny network traffic to resources connected to Azure Virtual Networks (VNet). NSGs can be associated to subnets, individual VMs (classic), or individual network interfaces (NIC) attached to VMs (Resource Manager). References:https://docs.microsoft.com/en-us/azure/governance/policy/overview Box 1: RG4 only
Virtual Networks are not allowed for Rg5 and Rg6.
Box 2: Rg4 and Rg6
Scenario:
Contoso has two Azure subscriptions named Sub1 and Sub2.
Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6.
You assign User8 the Owner role for RG4, RG5, and RG6
User8 city Sidney, Role:None
Note: A network security group (NSG) contains a list of security rules that allow or deny network traffic to resources connected to Azure Virtual Networks (VNet). NSGs can be associated to subnets, individual VMs (classic), or individual network interfaces (NIC) attached to VMs (Resource Manager).
References:
https://docs.microsoft.com/en-us/azure/governance/policy/overview
Question 7


Which virtual networks in Sub1 can User2 modify and delete in their current state? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Box 1: VNET4 and VNET1 only RG1 has only Delete lock, while there are no locks on RG4. RG2 and RG3 both have Read-only locks. Box 2: VNET4 onlyThere are no locks on RG4, while the other resource groups have either Delete or Read-only locks. Note: As an administrator, you may need to lock a subscription, resource group, or resource to prevent other users in your organization from accidentally deleting or modifying critical resources. You can set the lock level to CanNotDelete or ReadOnly. In the portal, the locks are called Delete and Read-only respectively. CanNotDelete means authorized users can still read and modify a resource, but they can't delete the resource. ReadOnly means authorized users can read a resource, but they can't delete or update the resource. Applying this lock is similar to restricting all authorized users to the permissions granted by the Reader role. Scenario:User2 is a Security administrator. Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6. User2 creates the virtual networks shown in the following table. Sub1 contains the locks shown in the following table. References:https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources Box 1: VNET4 and VNET1 only
RG1 has only Delete lock, while there are no locks on RG4.
RG2 and RG3 both have Read-only locks.
Box 2: VNET4 only
There are no locks on RG4, while the other resource groups have either Delete or Read-only locks.
Note: As an administrator, you may need to lock a subscription, resource group, or resource to prevent other users in your organization from accidentally deleting or modifying critical resources. You can set the lock level to CanNotDelete or ReadOnly. In the portal, the locks are called Delete and Read-only respectively.
CanNotDelete means authorized users can still read and modify a resource, but they can't delete the resource.
ReadOnly means authorized users can read a resource, but they can't delete or update the resource.
Applying this lock is similar to restricting all authorized users to the permissions granted by the Reader role.
Scenario:
User2 is a Security administrator.
Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6.
User2 creates the virtual networks shown in the following table.

Sub1 contains the locks shown in the following table.

References:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources
Question 8


Which virtual networks in Sub1 can User9 modify and delete in their current state? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Box 1: VNET4 and VNET1 only RG1 has only Delete lock, while there are no locks on RG4. RG2 and RG3 both have Read-only locks. Box 2: VNET4 onlyThere are no locks on RG4, while the other resource groups have either Delete or Read-only locks. Note: As an administrator, you may need to lock a subscription, resource group, or resource to prevent other users in your organization from accidentally deleting or modifying critical resources. You can set the lock level to CanNotDelete or ReadOnly. In the portal, the locks are called Delete and Read-only respectively. 1.CanNotDelete means authorized users can still read and modify a resource, but they can't delete the resource. 2.ReadOnly means authorized users can read a resource, but they can't delete or update the resource. Applying this lock is similar to restricting all authorized users to the permissions granted by the Reader role. Scenario:Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6. User9 creates the virtual networks shown in the following table. Sub1 contains the locks shown in the following table. Reference:https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources Box 1: VNET4 and VNET1 only
RG1 has only Delete lock, while there are no locks on RG4.
RG2 and RG3 both have Read-only locks.
Box 2: VNET4 only
There are no locks on RG4, while the other resource groups have either Delete or Read-only locks.
Note: As an administrator, you may need to lock a subscription, resource group, or resource to prevent other users in your organization from accidentally deleting or modifying critical resources. You can set the lock level to CanNotDelete or ReadOnly. In the portal, the locks are called Delete and Read-only respectively.
1.CanNotDelete means authorized users can still read and modify a resource, but they can't delete the resource.
2.ReadOnly means authorized users can read a resource, but they can't delete or update the resource.
Applying this lock is similar to restricting all authorized users to the permissions granted by the Reader role.
Scenario:
Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6.
User9 creates the virtual networks shown in the following table.

Sub1 contains the locks shown in the following table.

Reference:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources
Question 9
You need to ensure that you can meet the security operations requirements.
What should you do first?
- Turn on Auto Provisioning in Security Center.
- Integrate Security Center and Microsoft Cloud App Security.
- Upgrade the pricing tier of Security Center to Standard.
- Modify the Security Center workspace configuration.
Correct answer: C
Explanation:
The Standard tier extends the capabilities of the Free tier to workloads running in private and other public clouds, providing unified security management and threat protection across your hybrid cloud workloads. The Standard tier also adds advanced threat detection capabilities, which uses built-in behavioral analytics and machine learning to identify attacks and zero-day exploits, access and application controls to reduce exposure to network attacks and malware, and more. Scenario: Security Operations RequirementsLitware must be able to customize the operating system security configurations in Azure Security Center. References:https://docs.microsoft.com/en-us/azure/security-center/security-center-pricing The Standard tier extends the capabilities of the Free tier to workloads running in private and other public clouds, providing unified security management and threat protection across your hybrid cloud workloads.
The Standard tier also adds advanced threat detection capabilities, which uses built-in behavioral analytics and machine learning to identify attacks and zero-day exploits, access and application controls to reduce exposure to network attacks and malware, and more.
Scenario: Security Operations Requirements
Litware must be able to customize the operating system security configurations in Azure Security Center.
References:
https://docs.microsoft.com/en-us/azure/security-center/security-center-pricing
Question 10


You need to ensure that users can access VM0. The solution must meet the platform protection requirements.
What should you do?
- Move VM0 to Subnet1.
- On Firewall, configure a network traffic filtering rule.
- Assign RT1 to AzureFirewallSubnet.
- On Firewall, configure a DNAT rule.
Correct answer: A
Explanation:
Azure Firewall has the following known issue:Conflict with Azure Security Center (ASC) Just-in-Time (JIT) feature. If a virtual machine is accessed using JIT, and is in a subnet with a user-defined route that points to Azure Firewall as a default gateway, ASC JIT doesn’t work. This is a result of asymmetric routing – a packet comes in via the virtual machine public IP (JIT opened the access), but the return path is via the firewall,which drops the packet because there is no established session on the firewall. Solution: To work around this issue, place the JIT virtual machines on a separate subnet that doesn’t have a user-defined route to the firewall. Scenario: Following the implementation of the planned changes, the IT team must be able to connect to VM0 by using JIT VM access. References:https://docs.microsoft.com/en-us/azure/firewall/overview Azure Firewall has the following known issue:
Conflict with Azure Security Center (ASC) Just-in-Time (JIT) feature.
If a virtual machine is accessed using JIT, and is in a subnet with a user-defined route that points to Azure Firewall as a default gateway, ASC JIT doesn’t work. This is a result of asymmetric routing – a packet comes in via the virtual machine public IP (JIT opened the access), but the return path is via the firewall,which drops the packet because there is no established session on the firewall.
Solution: To work around this issue, place the JIT virtual machines on a separate subnet that doesn’t have a user-defined route to the firewall.
Scenario:

Following the implementation of the planned changes, the IT team must be able to connect to VM0 by using JIT VM access.

References:
https://docs.microsoft.com/en-us/azure/firewall/overview

