File Info
| Exam | Windows 10 |
| Number | MD-100 |
| File Name | Microsoft.MD-100.TestKing.2019-06-17.39q.vcex |
| Size | 786 KB |
| Posted | Jun 17, 2019 |
| Download | Microsoft.MD-100.TestKing.2019-06-17.39q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
You plan to deploy Windows 10 to 100 secure computers.
You need to select a version of Windows 10 that meets the following requirements:
- Uses Microsoft Edge as the default browser
- Minimizes the attack surface on the computer
- Supports joining Microsoft Azure Active Directory (Azure AD)
- Only allows the installation of applications from the Microsoft Store
What is the best version to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
- Windows 10 Pro in S mode
- Windows 10 Home in S mode
- Windows 10 Pro
- Windows 10 Enterprise
Correct answer: C
Explanation:
References:https://www.microsoft.com/en-za/windows/compare References:
https://www.microsoft.com/en-za/windows/compare
Question 2
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows10.
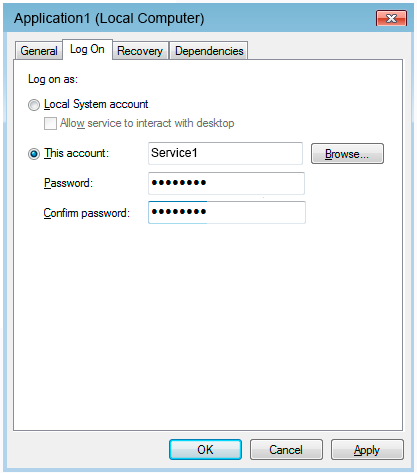
A service named Application1 is configured as shown in the exhibit.

You discover that a user used the Service1 account to sign in to Computer1 and deleted some files.
You need to ensure that the identity used by Application1 cannot be used by a user to sign in to sign in to the desktop on Computer1. The solution must use the principle of least privilege.
Solution: On Computer1, you configure Application1 to sign in as the LocalSystem account and select the Allow service to interact with desktop check box. You delete the Service1 account.
Does this meet the goal?
- Yes
- No
Correct answer: B
Question 3

Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10.
A service named Application1 is configured as shown in the exhibit.

You discover that a user used the Service1 account to sign in to Computer1 and deleted some files.
You need to ensure that the identity used by Application1 cannot be used by a user to sign in to sign in to the desktop on Computer1. The solution must use the principle of least privilege.
Solution: On Computer1, you assign Service1 the deny log on locally user right.
Does this meet the goal?
- Yes
- No
Correct answer: B
Explanation:
References:https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/deny-log-on-locally References:
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/deny-log-on-locally
Question 4

Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10.
A service named Application1 is configured as shown in the exhibit.

You discover that a user used the Service1 account to sign in to Computer1 and deleted some files.
You need to ensure that the identity used by Application1 cannot be used by a user to sign in to sign in to the desktop on Computer1. The solution must use the principle of least privilege.
Solution: On Computer1, you assign Service1 the deny log on as a service user right.
Does this meet the goal?
- Yes
- No
Correct answer: A
Explanation:
References:https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/deny-log-on-as-a-service References:
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/deny-log-on-as-a-service
Question 5
You need to sign in as LocalAdmin on Computer11.
What should you do first?
- From the LAPS UI tool, view the administrator account password for the computer object of Computer11.
- From Local Security Policy, edit the policy password settings on Computer11.
- From the LAPS UI tool, reset the administrator account password for the computer object of Computer11.
- From Microsoft Intune, edit the policy password settings on Computer11.
Correct answer: A
Explanation:
References:https://technet.microsoft.com/en-us/mt227395.aspx References:
https://technet.microsoft.com/en-us/mt227395.aspx
Question 6
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10. The computer contains a folder. The folder contains sensitive data.
You need to log which user reads the contents of the folder and modifies and deletes files in the folder.
Solution: From the properties of the folder, you configure the Auditing settings and from the Audit Policy in the local Group Policy, you configure Audit directory service access.
Does this meet the goal?
- Yes
- No
Correct answer: B
Explanation:
References:https://www.netwrix.com/how_to_detect_who_changed_file_or_folder_owner.html References:
https://www.netwrix.com/how_to_detect_who_changed_file_or_folder_owner.html
Question 7
Your network contains an Active Directory domain. The domain contains 1,000 computers that run Windows 10.
You discover that when users are on their lock screen, they see a different background image every day, along with tips for using different features in Windows 10.
You need to disable the tips and the daily background image for all the Windows 10 computers.
Which Group Policy settings should you modify?
- Turn off the Windows Welcome Experience
- Turn off Windows Spotlight on Settings
- Do not suggest third-party content in Windows spotlight
- Turn off all Windows spotlight features
Correct answer: D
Explanation:
References:https://docs.microsoft.com/en-us/windows/configuration/windows-spotlight References:
https://docs.microsoft.com/en-us/windows/configuration/windows-spotlight
Question 8
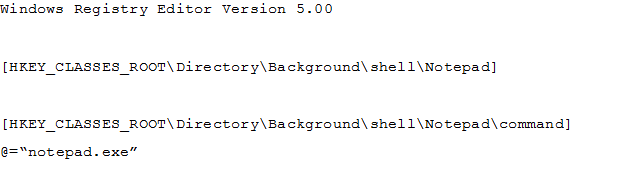
You have a file named Reg1.reg that contains the following content.

What is the effect of importing the file?
- A key named command will be renamed as notepad.exe.
- In a key named Notepad, the command value will be set to @="notepad.exe".
- In a key named command, the default value will be set to notepad.exe.
Correct answer: B
Question 9
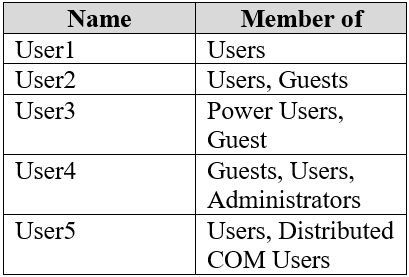
You have a computer named Computer1 that runs Windows 10.
On Computer1, you create the local users shown in the following table.

Which three user profiles will persist after each user signs out? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- User1
- User2
- User3
- User4
- User5
Correct answer: ADE
Question 10
You have 20 computers that run Windows 10. The computers are in a workgroup.
You need to create a local user named Admin1 on all the computers. Admin1 must be a member of the Remote Management Users group.
What should you do?
- From Windows Configuration Designer, create a provisioning package, and then run the provisioning package on each computer.
- Create a script that runs the New-ADUser cmdlet and the Set-AdGroup cmdlet.
- Create a Group Policy object (GPO) that contains the Local User Group Policy preference.
- Create a script that runs the New-MsolUser cmdlet and the Add-ADComputerServiceAccount cmdlet.
Correct answer: C
Explanation:
References:https://blogs.technet.microsoft.com/askpfeplat/2017/11/06/use-group-policy-preferences-to-manage-the-local-administrator-group/ References:
https://blogs.technet.microsoft.com/askpfeplat/2017/11/06/use-group-policy-preferences-to-manage-the-local-administrator-group/

