File Info
| Exam | Microsoft Security Operations Analyst |
| Number | SC-200 |
| File Name | Microsoft.SC-200.VCEplus.2021-03-31.42q.vcex |
| Size | 2 MB |
| Posted | Mar 31, 2021 |
| Downloads: | 2 |
| Download | Microsoft.SC-200.VCEplus.2021-03-31.42q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
The issue for which team can be resolved by using Microsoft Defender for Endpoint?
- executive
- sales
- marketing
Correct answer: B
Explanation:
Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/microsoft-defender-atp-ios Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/microsoft-defender-atp-ios
Question 2
The issue for which team can be resolved by using Microsoft Defender for Office 365?
- executive
- marketing
- security
- sales
Correct answer: B
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/atp-for-spo-odb-and-teams?view=o365-worldwide Testlet 2 Reference: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/atp-for-spo-odb-and-teams?view=o365-worldwide Testlet 2
Question 3
You need to implement the Azure Information Protection requirements.
What should you configure first?
- Device health and compliance reports settings in Microsoft Defender Security Center
- scanner clusters in Azure Information Protection from the Azure portal
- content scan jobs in Azure Information Protection from the Azure portal
- Advanced features from Settings in Microsoft Defender Security Center
Correct answer: D
Explanation:
Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/information-protection-in-windows-overview Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/information-protection-in-windows-overview
Question 4
You need to modify the anomaly detection policy settings to meet the Cloud App Security requirements.
- Activity from suspicious IP addresses
- Activity from anonymous IP addresses
- Impossible travel
- Risky sign-in
Correct answer: C
Explanation:
Reference: https://docs.microsoft.com/en-us/cloud-app-security/anomaly-detection-policy Reference:
https://docs.microsoft.com/en-us/cloud-app-security/anomaly-detection-policy
Question 5
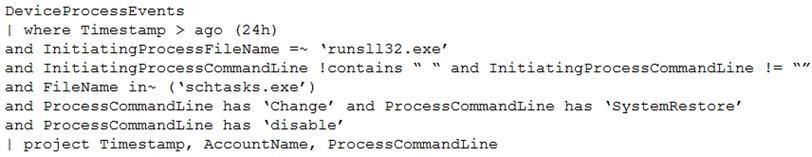
You have the following advanced hunting query in Microsoft 365 Defender.

You need to receive an alert when any process disables System Restore on a device managed by Microsoft Defender during the last 24 hours.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Create a detection rule.
- Create a suppression rule.
- Add | order by Timestamp to the query.
- Replace DeviceProcessEvents with DeviceNetworkEvents.
- Add DeviceId and ReportId to the output of the query.
Correct answer: AE
Explanation:
Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/custom-detection-rules Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/custom-detection-rules
Question 6
You need to receive a security alert when a user attempts to sign in from a location that was never used by the other users in your organization to sign in.
Which anomaly detection policy should you use?
- Impossible travel
- Activity from anonymous IP addresses
- Activity from infrequent country
- Malware detection
Correct answer: C
Explanation:
Reference: https://docs.microsoft.com/en-us/cloud-app-security/anomaly-detection-policy Reference: https://docs.microsoft.com/en-us/cloud-app-security/anomaly-detection-policy
Question 7
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365.
You have Microsoft SharePoint Online sites that contain sensitive documents. The documents contain customer account numbers that each consists of 32 alphanumeric characters.
You need to create a data loss prevention (DLP) policy to protect the sensitive documents.
What should you use to detect which documents are sensitive?
- SharePoint search
- a hunting query in Microsoft 365 Defender
- Azure Information Protection
- RegEx pattern matching
Correct answer: C
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/information-protection/what-is-information-protection Reference:
https://docs.microsoft.com/en-us/azure/information-protection/what-is-information-protection
Question 8
Your company uses line-of-business apps that contain Microsoft Office VBA macros.
You plan to enable protection against downloading and running additional payloads from the Office VBA macros as additional child processes.
You need to identify which Office VBA macros might be affected.
Which two commands can you run to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Correct answer: BC
Explanation:
Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/attack-surface-reduction Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/attack-surface-reduction
Question 9
Your company uses Microsoft Defender for Endpoint.
The company has Microsoft Word documents that contain macros. The documents are used frequently on the devices of the company’s accounting team.
You need to hide false positive in the Alerts queue, while maintaining the existing security posture.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Resolve the alert automatically.
- Hide the alert.
- Create a suppression rule scoped to any device.
- Create a suppression rule scoped to a device group.
- Generate the alert.
Correct answer: BCE
Explanation:
Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/manage-alerts Reference: https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/manage-alerts
Question 10
You are investigating a potential attack that deploys a new ransomware strain.
You plan to perform automated actions on a group of highly valuable machines that contain sensitive information.
You have three custom device groups.
You need to be able to temporarily group the machines to perform actions on the devices.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Add a tag to the device group.
- Add the device users to the admin role.
- Add a tag to the machines.
- Create a new device group that has a rank of 1.
- Create a new admin role.
- Create a new device group that has a rank of 4.
Correct answer: BDE
Explanation:
Reference: https://www.drware.com/how-to-use-tagging-effectively-in-microsoft-defender-for-endpoint-part-1/ Reference:
https://www.drware.com/how-to-use-tagging-effectively-in-microsoft-defender-for-endpoint-part-1/





