File Info
| Exam | Oracle Cloud Infrastructure 2019 Cloud Operations Associate |
| Number | 1Z0-1067 |
| File Name | Oracle.1Z0-1067.CertDumps.2020-06-15.60q.vcex |
| Size | 2 MB |
| Posted | Jun 15, 2020 |
| Download | Oracle.1Z0-1067.CertDumps.2020-06-15.60q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
You have recently Joined a startup company and quickly find that nobody is tracking the amount of money spent on Oracle Cloud Infrastructure (OCI). Seeing an opportunity to help save money you begin creating a solution to better track the cost of resources provisioned by each individual on the team.
Which option allows you to identify excessive spend across all resources in your tenancy?
- Use the Python SDK to write a custom application that will monitor the Audit Log. Look for CREATE events and configure the application to send you an email each time a new resource is created.
- Create a budget for each compartment that will send a notification when monthly spend reaches a pre- defined amount.
- Create a tag namespace named BILLING with a Tag Key named CostCcnter. Tag each of your resources with this Tag Key and the correct value.
- Use the Events Service and create rules that will act when a new Object Storage bucket or Compute Instance has been created. Have the rule email you each time one of these events occurs.
Correct answer: A
Question 2
A subscriber of on Oracle Cloud Infrastructure (OCI) Notifications service topic complained about not receiving messages from the service. Which of the following options can help you debug this issue?
- If OCI Notifications service does not receive an acknowledgement from a subscription endpoint, the service tries to redeliver messages for up to two hours. Configure an alarm on the NumberofNotificationFaiied metric through the OCI Monitoring service to help debug the issue.
- If OCI Notifications service does not receive an acknowledgement from a subscription endpoint, the service drops the message. Confirm that the subscriber is always online to receive messages to help debug the issue.
- If OCI Notifications service does not receive an acknowledgement from a subscription endpoint, the service tries to redeliver messages for up to one day. Make sure that the subscriber is online at least once a day to help debug the Issue.
- If OCI Notifications service does not receive an acknowledgement from a subscription endpoint, check the NumberofNotificationFaiied metric through the OCI Monitoring service for failed messages.
- Copy these messages to an OCI Object Storage bucket. Make sure the subscriber has the required credentials to access this bucket to help debug the Issue
Correct answer: D
Question 3
You have been brought In to help secure an existing application that leverages Object Storage buckets to distribute content.
The data is currently being shared from public buckets and the security team Is not satisfied with this approach. They have stated that all data must be stored In storage buckets. Your application should be able to provide secure access to the dat a.
The URL that is provided for access to the data must be rotated every 30 days.
Which design option will meet these requirements?
- Use Pre-Authentlcated request, even though there will be multiple URLs this will provide better security.
- Create a private bucket only to share the data.
- Create a new group and map users to this group, create a IAM policy providing access to Object Storage service only to this group. Users can then simply login to OCI console and retrieve needed flies.
- Create multiple bucket and classify them as Public and Private. Use public bucket for non-sensitive data and private bucket for sensitive data.
Correct answer: B
Question 4
You have received an email from your manager to provision new resources on Oracle Cloud Infrastructure (OCI). When researching OCI y detect that you should use OCI Resource Manager.
Since this is a task that will be done multiple times for development, test, and production need to create a command that can be re-used.
Which CLI command can be used In this situation? A.
Correct answer: B
Question 5
You have created several block volumes in the us-phoenix-1 region in a specific compartment. The compartment can be identified by the following Orade Cloud Infrastructure (OCI) unique identifier, or OCID: dl-compartment.oc1.phx..exampleuniquelD
Your manager has asked you to leverage the OCI monitoring service and write a metric query showing all read IOPS at a one-minute interval, filtered to this compartment and aggregated for the maximum.
Which metric query will you create?
- IopsWrite[lm]{compartmentId=Hocidl.compartment.ocl.phx..exampleuniquelD"}.mean()
- IopsRead[lm]{compartmentId="ocldl.compartment.ocl.phx..exampleuniquelD"}.max()
- IopsRead[lm]{compartmentId="ocidl.compartment.ocl.phx..exampleuniquelD"}.grouplng().max()
- IopsRead[lm]{compartmentId = "oddl.compartment.ocl.phx..exampleuniquelD"}.grouping().mean()
Correct answer: D
Question 6
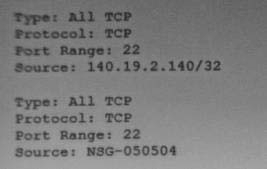
You set up a bastion host in your VCN to only alow your IP address (140.19.2.140) to establish SSH connections to your Compute instances that are deployed private subnet. The Compute instances have an attached Network Security Group with a Source Type: Network security Group (NSG) , Source NSG: -050504.
To secure the bastion host, you added the following ingress rules to its Network Security Group:

However, after checking the bastion host logs, you discovered that there are IP addresses other than your own that can access your bastion host.
What is the root cause of this issue?
- A netmask of /32 allows all IP address in the 140.19.2.0 network, other than your IP 110.19.2.140
- The port 22 provides unrestneted access to 140.19.2.140 and to other IP address
- Al compute instances associated with nso-050504 are also able to connect to the bastion host.
- The Security List allows access to all IP address which overrides the Network Security Group ingress rules.
Correct answer: A
Question 7
Your company recently adopted a hybrid cloud architecture which requires them to migrate some of their on- premises web applications to Oracle Cloud Infrastructure OCI). You created a Terraform template which automatically provisions OCI resources such as compute instances, load balancer, and a database instance. After running the stack using the terraform apply command, it successfully launched the compute Instances and the load balancer, but it failed to create a new database Instance with the following error:
Service error:NotAuthorizedOrNotFound. shape VM.Standard2.4 not found, http status code: 404 You discovered that the resource quotas assigned to your compartment prevent you from using VM.Standard2.4 instance shapes available in your tenancy. You edit the Terraform script and replace the shape with VM.Standard2.2.
Which option would you recommend to re-run the terraform command to have required OCI resources provisioned with the least effort?
- terraform apply -target=ocl_database_db_system.db_system
- terraform refresh -target=oci_database_db_system.db_system
- terraform apply -auto-approve
- terraform plan -target=oci_database_db_system.db_system
Correct answer: B
Question 8
You are configuring on alarm In Oracle Cloud Infrastructure (OCI) for a compute instance named vision. The metric needs to be triggered when the ingress network rate is greater than 1MB.
Which statement will accomplish this?
- NetworksBytesIn[1MB]{resourceDisplayName - "vision"}.rate() > 1
- NetworksBytesIn[1m]{resourceDisplayName - "vision"}.rate() > 1024
- {resourceDisplayName = "vision"}(NetworksBytesIn[lm]).rate() > 1024
- {resourceDisplayName = Hvision"}(NetworksBytesIn[1MB]).rate() > 1
Correct answer: C
Question 9
As the operations administrator for your company's Oracle Cloud Infrastructure (OCI), you have been entrusted the task of ensuring that data being accessed by the application is encrypted.
Your application portfolio Includes both Virtual Machine (VM) and Bare Metal (BM) database systems. Which method should you use to achieve encryption of data in-transit?
- Configure backup encryption for RMAN backup sets before transferring data
- Native Oracle Net Services encryption and integrity capabilities
- Key Store/Wallet service for on the fly encryption of data in transit
- Data is encrypted at rest using TDE and no additional encryption Is needed
Correct answer: A
Question 10

You Saw created a group for several auditors. You assign the following policies to the group:

What actions are the auditors allowed to perform within your tenancy?
- Auditors are able to view all resources in the compartment.
- Auditors are able to create new instances in the tenancy.
- The Auditors can view resources in the tenancy.
- The Auditors are able to delete resources in the tenancy.
Correct answer: D





