File Info
| Exam | Red Hat Certified Engineer (RHCE) exam for Red Hat Enterprise Linux 8 |
| Number | EX294 |
| File Name | RedHat.EX294.VCEplus.2021-01-10.39q.vcex |
| Size | 2 MB |
| Posted | Jan 10, 2021 |
| Download | RedHat.EX294.VCEplus.2021-01-10.39q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
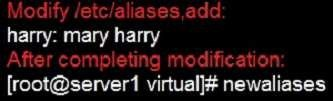
Configure a mail alias to your MTA, for example, send emails to harry but mary actually is receiving emails.
- Please see explanation
Correct answer: A
Explanation:
Notice: This problem is a trap. The question no 31 requires that harry must be able to receive remote emails but the problems in the question no 32 requires mary to receive harry’s emails. So harry must be added when you are deploying aliases. 
Notice:
This problem is a trap. The question no 31 requires that harry must be able to receive remote emails but the problems in the question no 32 requires mary to
receive harry’s emails. So harry must be added when you are deploying aliases.
Question 2
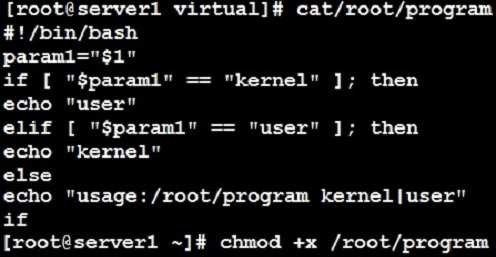
Create a Shell script /root/program:
- The shell script will come back to “user” parameter when you are entering “kernel” parameter.
- The shell script will come back to “kernel” when you are entering “user” parameter.
It will output the standard error when this script “usage:/root/program kernel|user” don’t input any parameter or the parameter you inputted is entered as the
requirements.
- Please see explanation
Correct answer: A
Explanation:

Question 3
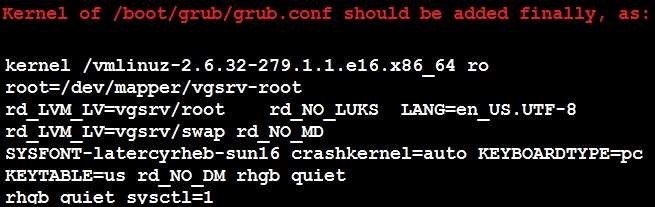
Given the kernel of a permanent kernel parameters: sysctl=1. It can be shown on cmdline after restarting the system. Kernel of /boot/grub/grub.conf should be a34dded finally, as:
- Please see explanation
Correct answer: A
Explanation:

Question 4
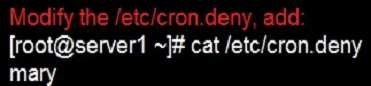

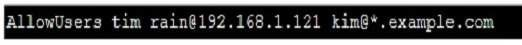
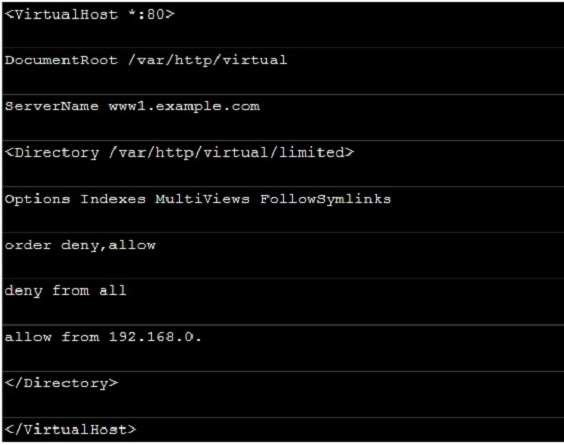

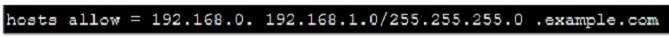

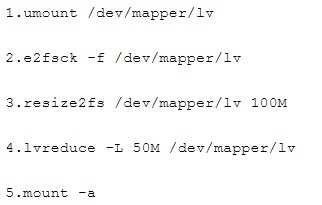
Prevent Mary from performing user configuration tasks in your system.
- Please see explanation
Correct answer: A
Explanation:
Conclusions: 1. I find that it is common to add various service access limits in the exam RHCE. The exercises like: require one network segment can be accessed another network segments can not be accessed, the following are some conclusions for various service: tcp_wrappers:/etc/hosts.allow,/etc/hosts.deny tcp_wrappers can filter the TCP’s accessing service. TCP whether has the filtering function which depends on this service whether use the function library of tcp_wrappers, or this service whether has the xinetd process of starting function of tcp_wrappers. tcp_wrappers’s main configuration file is /etc/hosts.allow,/etc/ hosts.deny.And the priority of the documents in hosts. allow is higher than hosts. deny. Visit will be passed if no match was found.sshd,vsftpd can use the filtering service of tcp_wrappers. Configuration example: Notice: The two configuration files’ syntax can refer to hosts_access (5) and hosts_options(5) sshd_config There are four parameters in this configuration file: DenyUsers, AllowUsers, DenyGroups, AllowGroups, they are used to limit some users or user groups to proceed Remote Login through the SSH. These parameters’ priority level is DenyUsers->AllowUsers->DenyGroups->AllowGroups Configuration example: httpd Service Through the /etc/httpd/conf/httpd.conf in parameters, can add <Directory> to control the url access. Just as: Notice: So pay attention, deny’s and allow’s priority level in order deny,allow is: the backer has the higher priority level. But here, allow’s priority has a higher priority level. nfs Service nfs service directly control the visits through file /etc/exports, just as: samba Service Parameter hosts allow in /etc/samba/smb.conf which is used as Access Control, just as: 2. Paying attention to use Mount parameters: _netdev,defaults when you are mounting ISCSI disk. 3. Stop the NetworkManager /etc/init.d/NetworkManager stop chkconfig NetworkManager off 4. When you are deploying ifcfg-ethX, add parameters: PEERDNS=no 5. Empty the firewall in RHCSA RHCE、 : 6. Narrow lv steps: 7. Mount the using command - swap which is newly added in /etc/fstab 8. If Verification is not passed when you are installing software, can import public key: rpm import /etc/pki/rpm…/…release and so on. In yum.repo, you also can deploy gpgkey, for example, gpgkey=/etc/pki/rpm…/…release 9. When you are using “Find” command to search and keep these files, paying attention to use cp -a to copy files if you use user name and authority as your searching methods. 
Conclusions:
1. I find that it is common to add various service access limits in the exam RHCE. The exercises like: require one network segment can be accessed another
network segments can not be accessed, the following are some conclusions for various service: tcp_wrappers:/etc/hosts.allow,/etc/hosts.deny tcp_wrappers can filter the TCP’s accessing service. TCP whether has the filtering function which depends on this service whether use the function library of tcp_wrappers, or this service whether has the xinetd process of starting function of tcp_wrappers. tcp_wrappers’s main configuration file is /etc/hosts.allow,/etc/
hosts.deny.And the priority of the documents in hosts. allow is higher than hosts. deny. Visit will be passed if no match was found.
sshd,vsftpd can use the filtering service of tcp_wrappers.
Configuration example:

Notice:
The two configuration files’ syntax can refer to hosts_access (5) and hosts_options(5) sshd_config
There are four parameters in this configuration file: DenyUsers, AllowUsers, DenyGroups, AllowGroups, they are used to limit some users or user groups to
proceed Remote Login through the SSH. These parameters’ priority level is DenyUsers->AllowUsers->DenyGroups->AllowGroups Configuration example:

httpd Service
Through the /etc/httpd/conf/httpd.conf in parameters, can add <Directory> to control the url access. Just as:

Notice:
So pay attention, deny’s and allow’s priority level in order deny,allow is: the backer has the higher priority level. But here, allow’s priority has a higher priority level.
nfs Service nfs service directly control the visits through file /etc/exports, just as:

samba Service
Parameter hosts allow in /etc/samba/smb.conf which is used as Access Control, just as:

2. Paying attention to use Mount parameters: _netdev,defaults when you are mounting ISCSI disk.
3. Stop the NetworkManager
/etc/init.d/NetworkManager stop chkconfig
NetworkManager off
4. When you are deploying ifcfg-ethX, add parameters:
PEERDNS=no
5. Empty the firewall in RHCSA RHCE、 :

6. Narrow lv steps:

7. Mount the using command - swap which is newly added in /etc/fstab
8. If Verification is not passed when you are installing software, can import public key: rpm import /etc/pki/rpm…/…release and so on. In yum.repo, you also can
deploy gpgkey, for example, gpgkey=/etc/pki/rpm…/…release
9. When you are using “Find” command to search and keep these files, paying attention to use cp -a to copy files if you use user name and authority as your
searching methods.
Question 5
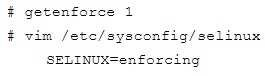
Please set the selinux status as enforcing.
- Please see explanation
Correct answer: A
Explanation:

Question 6
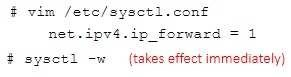
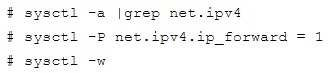
Please open the ip_forward and take effect permanently.
- Please see explanation
Correct answer: A
Explanation:
If no “sysctl.conf” option, use these commands: 
If no “sysctl.conf” option, use these commands:

Question 7
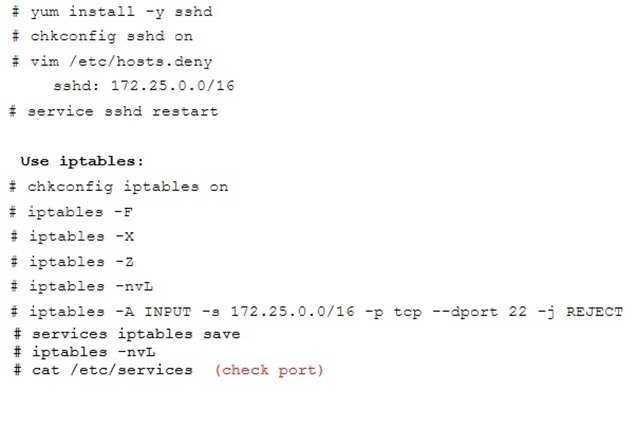
Configure ssh to allow user harry to access, reject the domain t3gg.com (172.25.0.0/16) to access.
- Please see explanation
Correct answer: A
Explanation:

Question 8
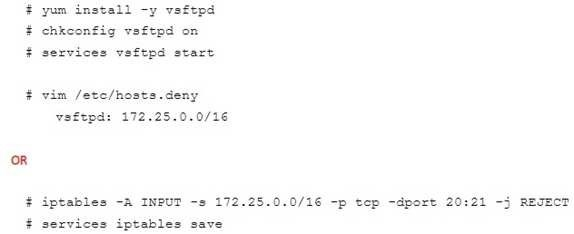
Configure the ftp to allow anonymously download the directory /var/ftp/pub, and reject the domain t3gg.com to access.
- Please see explanation
Correct answer: A
Explanation:

Question 9
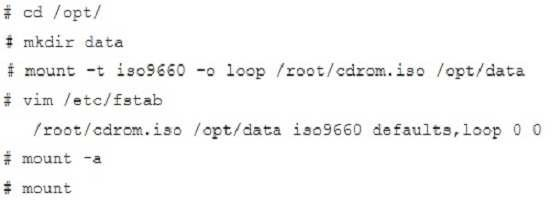
Shutdown the /root/cdrom.iso under /opt/data and set as boot automatically mount.
- Please see explanation
Correct answer: A
Explanation:

Question 10
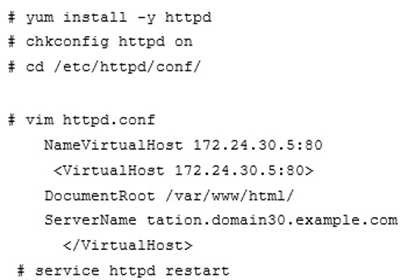
Configure the web server, which can be accessed by http://station.domain30.example.com.
- Please see explanation
Correct answer: A
Explanation:



