File Info
| Exam | Fireware Essentials Exam |
| Number | Essentials |
| File Name | WatchGuard.Essentials.CertKey.2019-01-04.47q.vcex |
| Size | 826 KB |
| Posted | Jan 04, 2019 |
| Download | WatchGuard.Essentials.CertKey.2019-01-04.47q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%





Demo Questions
Question 1
You configured four Device Administrator user accounts for your Firebox. To see a report of witch Device Management users have made changes to the device
configuration, what must you do? (Select two.)
- Start Firebox System Manager for the device and review the activity for the Management Users on the Authentication List tab.
- Connect to Report Manager or Dimension and view the Audit Trail report for your device.
- Open WatchGuard Server Center and review the configuration history for managed devices.
- Configure your device to send audit trail log messages to your WatchGuard Log Server or Dimension Log Server.
Correct answer: BC
Question 2
Which items are included in a Firebox backup image? (Select four.)
- Support snapshot
- Fireware OS
- Configuration file
- Log file
- Feature keys
- Certificates
Correct answer: BCEF
Explanation:
A Firebox backup image is a saved copy of the working image from the Firebox flash disk. The backup image includes the Firebox appliance software, configuration file, licenses, and certificates. When you purchase an option for your Firebox, you add a new feature key to your configuration file. Reference: Fireware Basics, Courseware: WatchGuard System Manager 10, pages 14, 57 A Firebox backup image is a saved copy of the working image from the Firebox flash disk. The backup image includes the Firebox appliance software, configuration file, licenses, and certificates.
When you purchase an option for your Firebox, you add a new feature key to your configuration file.
Reference: Fireware Basics, Courseware: WatchGuard System Manager 10, pages 14, 57
Question 3
Only 50 clients on the trusted network of your Firebox can connect to the Internet at the same time. What could cause this? (Select one.)
- TheLiveSecurity feature key is expired.
- The device feature key allows a maximum of 50 client connections.
- The DHCP address pool on the trusted interface has only 50 IP addresses.
- The Outgoing policy allows a maximum of 50 client connections.
Correct answer: C
Question 4
The IP address for the trusted interface on your Firebox is 10.0.40.1/24, but you want to change the IP address for this interface. How can you avoid a network outage for clients on the trusted network when you change the interface IP address to 10.0.50.1/24? (Select one.)
- Create a 1-to-1 NAT rule for traffic from the 10.0.40.0/24 subnet to addresses on the 10.0.50.0/24 subnet.
- Add 10.0.40.1/24 as a secondary IP address for the interface.
- Add IP addresses on the 10.0.40.0/24 subnet to the DHCP Server IP address pool for this interface.
- Add a route to 10.0.40.0/24 with the gateway 10.0.50.1.
Correct answer: B
Question 5
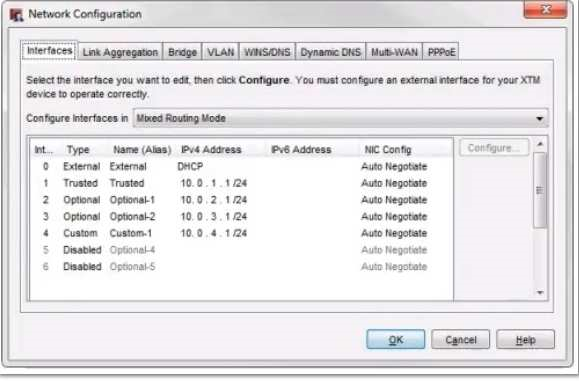
In the network configuration in this image, which aliases is Eth2 a member of? (Select three.)

- Any-optional
- Any-External
- Optional-1
- Any
- Any-Trusted
Correct answer: ACD
Explanation:
Question 6
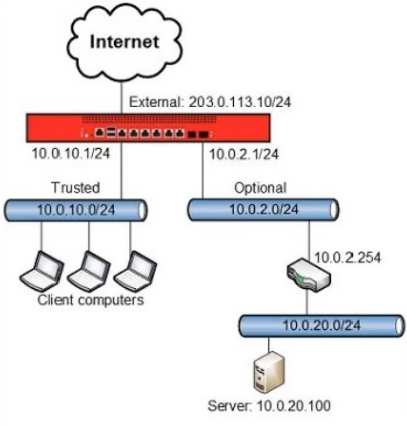
Clients on the trusted network need to connect to a server behind a router on the optional network. Based on this image, what static route must be added to the
Firebox for traffic from clients on the trusted network to reach a server at 10.0.20.100? (Select one.)

- Route to 10.0.20.0/24, Gateway 10.0.2.1
- Route to 10.0.20.0/24, Gateway 10.0.2.254
- Route to 10.0.20.0, Gateway 10.0.2.254
- Route to 10.0.10.0/24, Gateway 10.0.10.1
Correct answer: B
Explanation:
We must add a trusted static route to the 10.0.20.0/24 network through the 10.0.2.254 gateway. We must add a trusted static route to the 10.0.20.0/24 network through the 10.0.2.254 gateway.
Question 7
Which of these options are private IPv4 addresses you can assign to a trusted interface, as described in RFC 1918, Address Allocation for Private Internets?
(Select three.)
- 192.168.50.1/24
- 10.50.1.1/16
- 198.51.100.1/24
- 172.16.0.1/16
- 192.0.2.1/24
Correct answer: ABD
Question 8
The policies in a default Firebox configuration do not allow outgoing traffic from optional interfaces.
- True
- False
Correct answer: B
Question 9
Which of these actions adds a host to the temporary or permanent blocked sites list? (Select three.)
- Enable the AUTO-block sites that attempt to connect option in a deny policy.
- Add the site to the Blocked Sites Exceptions list.
- On the Firebox System Manager >Blocked Sites tab, select Add.
- In Policy Manager, select Setup> Default Threat Protection > Blocked Sites and click Add.
Correct answer: ACD
Explanation:
A: You can configure a deny policy to automatically block sites that originate traffic that does not comply with the policy rulese1. From Policy Manager, double-click the PCAnywhere policy. 2. Click the Properties tab. Select the Auto-block sites that attempt to connect checkbox. Reference: https://www.watchguard.com/training/fireware/80/defense8.htmC: The blocked sites list shows all the sites currently blocked as a result of the rules defined in Policy Manager. From this tab, you can add sites to the temporaryblocked sites list, or remove temporary blocked sites. Reference: http://www.watchguard.com/training/fireware/82/monitoa6.htmD: You can use Policy Manager to permanently add sites to the Blocked Sites list.1. select Setup > Default Threat Protection > Blocked Sites. 2. Click Add. The Add Site dialog box appears. Reference: http://www.watchguard.com/help/docs/wsm/xtm_11/en-US/index.html#cshid=en-US/intrusionprevention/blocked_sites_permanent_c.html A: You can configure a deny policy to automatically block sites that originate traffic that does not comply with the policy rulese
1. From Policy Manager, double-click the PCAnywhere policy.
2. Click the Properties tab. Select the Auto-block sites that attempt to connect checkbox.
Reference: https://www.watchguard.com/training/fireware/80/defense8.htm
C: The blocked sites list shows all the sites currently blocked as a result of the rules defined in Policy Manager. From this tab, you can add sites to the temporary
blocked sites list, or remove temporary blocked sites.
Reference: http://www.watchguard.com/training/fireware/82/monitoa6.htm
D: You can use Policy Manager to permanently add sites to the Blocked Sites list.
1. select Setup > Default Threat Protection > Blocked Sites.
2. Click Add.
The Add Site dialog box appears.
Reference: http://www.watchguard.com/help/docs/wsm/xtm_11/en-US/index.html#cshid=en-US/intrusionprevention/blocked_sites_permanent_c.html
Question 10
Which of these threats can the Firebox prevent with the default packet handling settings? (Select four.)
- Access to inappropriate websites
- Denial of service attacks
- Flood attacks
- Malware in downloaded files
- Port scans
- Viruses in email messages
- IP spoofing
Correct answer: BCEG
Explanation:
B: The default configuration of the XTM device is to block DDoS attacks.C: In a flood attack, attackers send a very high volume of traffic to a system so it cannot examine and allow permitted network traffic. For example, an ICMP flood attack occurs when a system receives too many ICMP ping commands and must use all of its resources to send reply commands. The XTM device can protect against these types of flood attacks: IPSec, IKE, ICMP. SYN, and UDP.E: When the Block Port Space Probes (port scans) and Block Address Space Probes check boxes are selected, all incoming traffic on all interfaces is examined by the XTM device. CG: Default packet handling can reject a packet that could be a security risk, including packets that could be part of a spoofing attack or SYN flood attackReference: http://www.watchguard.com/help/docs/wsm/xtm_11/en-US/index.html#en-US/intrusionprevention/default_pkt_handling_opt_about_c.html%3FTocPath%3DDefault%2520Threat%2520Protection%7CAbout%2520Default%2520Packet%2520Handling%2520Options%7C_____0 B: The default configuration of the XTM device is to block DDoS attacks.
C: In a flood attack, attackers send a very high volume of traffic to a system so it cannot examine and allow permitted network traffic. For example, an ICMP flood attack occurs when a system receives too many ICMP ping commands and must use all of its resources to send reply commands. The XTM device can protect against these types of flood attacks: IPSec, IKE, ICMP. SYN, and UDP.
E: When the Block Port Space Probes (port scans) and Block Address Space Probes check boxes are selected, all incoming traffic on all interfaces is examined by the XTM device.
CG: Default packet handling can reject a packet that could be a security risk, including packets that could be part of a spoofing attack or SYN flood attack
Reference: http://www.watchguard.com/help/docs/wsm/xtm_11/en-US/index.html#en-US/intrusionprevention/default_pkt_handling_opt_about_c.html%3FTocPath%
3DDefault%2520Threat%2520Protection%7CAbout%2520Default%2520Packet%2520Handling%2520Options%7C_____0


